What is DNS hijacking?
DNS hijacking poses a significant threat to system security and can result in severe consequences. This attack empowers malicious actors to seize control of DNS settings, diverting users to deceptive websites, impacting a wide range of users. Understanding DNS hijacking necessitates grasping the fundamental function of the DNS.
Put simply, the DNS serves to organize and manage websites globally, facilitating user access by converting domain names into the requisite IP addresses for loading internet resources in browsers. With this foundational understanding of the DNS and its role, we can delve deeper into the intricacies of DNS hijacking.
What is DNS Hijacking?
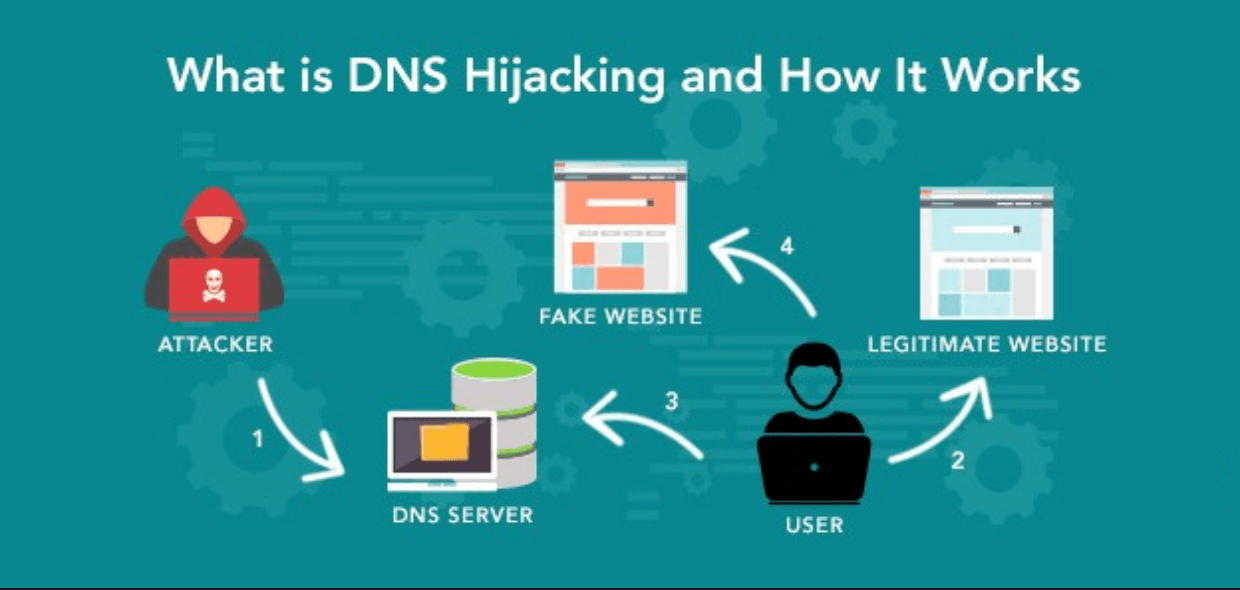
DNS hijacking, also known as DNS redirection, occurs when a user’s browser queries are manipulated, leading them to malicious websites.
ad
Unlike some DNS spoofing attacks, such as DNS cache poisoning which alters DNS records, DNS hijacking involves directly modifying DNS settings. This is often done through malware installed on the victim’s computer. This allows hackers to take control of routers, intercept DNS signals, or manipulate DNS communications. DNS hijacking poses a significant threat within the Domain Name System.
This presents risks to both individuals and businesses. Individuals may fall victim to phishing scams, unknowingly providing sensitive information on fake websites. For businesses, DNS hijacking can redirect visitors to fraudulent pages, potentially compromising data security and trust. Moreover, DNS hijacking can compromise email security, leading to privacy breaches.
Interestingly, some Internet Service Providers (ISPs) and governments use DNS hijacking for various purposes. ISPs may employ it for advertising or data collection, while governments may use it for censorship or guiding users to approved websites.
How Does DNS Hijacking Work?
When you enter a website address into your browser, it fetches webpage data from either your local browser cache (if you’ve recently visited the site) or by sending a DNS query to the name server, typically provided by a reputable Internet Service Provider (ISP). The vulnerable point lies in the unencrypted communication between your browser sending the DNS request and the name server’s response. It’s at this juncture that hackers can intercept the query and redirect the user to their malicious websites. There are four primary types of DNS hijacking methods utilized by cybercriminals today: “local,” “router,” “rogue,” and “man-in-the-middle.”
Local hijacking:
Local hijacking involves a hacker installing Trojan malware on your system to manipulate the local DNS settings. Following the attack, they can alter these settings to direct requests to their own DNS servers or other malicious servers.
Router hijacking:
Contrary to popular belief, router hijacking is often the primary target for cybercriminals due to default passwords or firmware vulnerabilities. Once they gain access to the router, hackers modify DNS settings to route users’ requests through their preferred DNS server, affecting all users connected to the compromised router.
Rogue hijacking:
Rogue hijacking is more intricate, as it involves hackers infiltrating the ISP’s name server to alter specific entries. This deceives unsuspecting users into accessing the compromised DNS server, resulting in their DNS requests being redirected to malicious websites.
Man-in-the-middle attacks:
Man-in-the-middle attacks focus on intercepting communications between users and the DNS. By interrupting the unencrypted communication, hackers can provide users with a different destination IP address, leading them to malicious websites. This method can also be used for DNS cache poisoning, affecting both local devices and DNS servers.
How to Detect DNS Hijacking
Fortunately, there are various simple ways to check if your DNS has been hacked. If you notice certain websites loading slower than usual or an increase in random pop-up ads suggesting your computer is infected, it could indicate a DNS compromise. However, these signs alone may not confirm it. Here are some practical steps you can take:
Verify your router settings or use a “router checker”:
Many online services offer tools to check your router settings. These tools can analyze your system using a reliable DNS resolver to determine if you’re using an authorized DNS server. Alternatively, you can access your router’s admin page online and review the DNS settings.
If you’ve experienced DNS hacks before or suspect one now, consider switching to a different public DNS service, such as Google’s Public DNS servers.
How To Prevent DNS Hijacking?
Whether facing local, router, or rogue DNS hijacking, it’s always preferable to prevent hacking attempts altogether. Fortunately, there are several measures you can implement to enhance your DNS security and overall data security.
Avoid clicking on suspicious or unfamiliar links:
Exercise caution with links in emails, text messages, or on social media. Shortened URLs can obscure dangerous destinations, so minimize their use. Whenever possible, manually enter URLs into your browser after confirming their legitimacy.
Use reputable antivirus software:
Regularly scan your computer for malware and keep your software updated. Effective security software can detect and remove infections resulting from a DNS hijack, particularly if your system has been compromised by Trojan malware during a local hijack. Since malicious websites can distribute various types of malware and adware, consistently scan for viruses, spyware, and other threats.
Use a virtual private network (VPN):
A VPN creates an encrypted tunnel for your website queries and traffic. Many reputable VPNs operate private DNS servers that exclusively handle end-to-end encrypted requests, safeguarding your local machine and their DNS servers. This significantly reduces the risk of a man-in-the-middle DNS hijack.
Change your router’s password (and username):
While seemingly straightforward, many users overlook this precaution. Default router login details are often easy to crack because they’re rarely changed. When creating a new password, opt for a “strong” one (approximately 10-12 characters long, incorporating special characters, numbers, uppercase, and lowercase letters).
Be aware:
If you encounter an unfamiliar website with unexpected pop-ups, landing pages, or tabs, exit the page immediately. Awareness of digital warning signs is crucial for bolstering cybersecurity.
For website owners, there are specific steps to prevent DNS hijacking:
Limit access to the DNS:
Restrict DNS settings access to select members of your IT team to mitigate opportunistic cybercriminals. Additionally, ensure those individuals use two-factor authentication when accessing the DNS registrar.
Enable client lock:
Some DNS registrars offer “client locking,” preventing unauthorized changes to DNS records without approval. Enable this feature whenever possible.
Use a registrar that supports DNSSEC:
Domain Name System Security Extensions provide a “verified real” label, enhancing DNS lookup authenticity and making it more challenging for hackers to intercept requests. Choose a registrar that supports DNSSEC implementation.
Real-world examples of DNS hijacking
There are numerous real-life instances of DNS hijacking. Here are a few notable examples:
The Sea Turtle campaign:
In early 2017, a group known as Sea Turtle targeted 40 organizations across 13 countries, primarily in the Middle East and North Africa. They compromised third-party entities managing the victims’ DNS queries, redirecting them to fake websites to steal login credentials.
The Twitter, New York Times & Huffington Post DNS hijack:
In 2013, the Syrian Electronic Army, a hacker group, hijacked the DNS servers of prominent media outlets such as Twitter, the New York Times, and the Huffington Post.
The ICANN DNS hijack attack:
In 2018, the Internet Corporation for Assigned Names and Numbers (ICANN) was hijacked by a Turkish hacker group known as NetDevilz. Users attempting to access the ICANN site were redirected to a page displaying the message: “You think that you control the domains but you don’t! Everybody knows wrong.”
DNS attack against WikiLeaks:
In 2017, the DNS servers of WikiLeaks were compromised by the Saudi Arabian-based hacker group OurMine. This led to the redirection of WikiLeaks’ users to a counterfeit website.
FAQ’s
What is DNS Hijacking?
DNS hijacking, also known as DNS redirection, occurs when a user’s browser queries are manipulated, leading them to malicious websites.
How does DNS Hijacking work?
DNS hijacking involves manipulating DNS settings to redirect users’ queries to fake websites. This can occur through malware installed on the victim’s computer or by compromising routers or DNS servers.
How can I detect DNS Hijacking?
Signs of DNS hijacking include slower website loading times, increased pop-up ads, and unexpected website redirects. You can verify your DNS settings using online tools or by accessing your router’s admin page.
How can I prevent DNS Hijacking?
To prevent DNS hijacking, avoid clicking on suspicious links, use reputable antivirus software, employ a virtual private network (VPN), change your router’s password regularly, and stay vigilant for signs of compromise.
Can DNS Hijacking affect both individuals and businesses?
Yes, DNS hijacking poses risks to both individuals and businesses. Individuals may fall victim to phishing scams, while businesses may suffer data breaches and loss of trust due to redirected visitors to fraudulent pages.
How do ISPs and governments use DNS Hijacking?
ISPs may employ DNS hijacking for advertising or data collection purposes, while governments may use it for censorship or guiding users to approved websites. However, these practices can also pose security risks to users.
What measures can website owners take to prevent DNS Hijacking?
Website owners can limit access to DNS settings, enable client lock features offered by DNS registrars, and use registrars that support DNSSEC implementation to enhance DNS security and prevent hijacking attempts.
Conclusion
DNS hijacking poses a serious threat to individuals and businesses, with potential consequences ranging from data breaches to privacy violations. Understanding its nature, detection methods, and prevention strategies is essential for safeguarding against such attacks. By staying vigilant, using reputable security measures, and adopting proactive practices, users can reduce the risk of falling victim to DNS hijacking. Similarly, website owners can take steps to fortify their defenses against such threats. Ultimately, raising awareness and implementing robust cybersecurity measures are crucial in protecting the integrity of the digital landscape.
ad


Comments are closed.