Network Protocols: Types, Layers and Advantages Explained
Network protocols are a set of pre-established rules that ensure the safe, reliable, and simple exchange of data. These rules apply to a wide range of situations. Ethernet, WLANs, and the Internet are all examples of protocols that are well-known to the general public. Many protocols make up the Internet protocol suite, which transmits and broadcasts data over the Internet.
What is the role and importance of protocols in Networks?
ad
If two or more communication systems use the same network protocol, they can exchange information using any variation in a physical quantity. As an illustration, there are data interchange protocols for hardware devices and protocols for application programs.
Network Protocols play a critical role in networking because of the following:
• The end-to-end processes of timely and secure network communication are governed by network protocols, which are set up in advance.
• It is impossible to communicate between computer systems, servers, routers, switches, and other network-enabled devices without following a set of protocols.
Without protocols, devices would be unable to understand the electronic signals sent between them via network connections.
ad
Modern computer networking protocols typically employ packet switching techniques to send and receive messages in the form of packets, which are messages divided into pieces that are collected and reassembled at their destination. Hundreds of computer network protocols have been created, each with a specific purpose and environment in mind.
Types of Network Protocols
1. Address Resolution Protocol (ARP)
IP address is used to identify a media access control (MAC) address in a communication layer protocol (the mapping process between the data link layer and network layer). In a peer-to-peer network, the host has no way of knowing where a network packet originated. ARP spoofing can occur as a result of this vulnerability. If the attacker is on the same LAN as the target or uses a compromised machine that is on the same network, this vulnerability can be exploited by the attacker. It’s based on the idea that an attacker can associate his MAC address with the target’s IP address so that the attacker can receive any traffic that the target sends.
2. Domain Name System (DNS) Protocol
DNS IP addresses have a numerical format, making them difficult for humans to read or remember. Hostnames are generated from IP addresses using a hierarchical system known as DNS. Cached poisoning is the most common vulnerability in DNS. Here, a malicious IP address is used instead of the legitimate one in order to redirect the intended audience to malicious websites. Recursive lookups can be used to increase the attack’s power by exploiting DNS amplification on a DNS server that supports them.
3. HyperText Transfer Protocol/Secure (HTTP/S)
On a computer network, it is used for secure communication. Authentication of the website accessed and protection of the data exchanged are its primary functions. As a result of the Drown attack, hackers are able to break the encryption and steal sensitive information such as credit card numbers. It’s also important to point out the Heartbleed bug, which allows for the theft of data protected by TLS/SSL encryption. Additionally, RSA export keys can be factored and Compressing Ratio Info-leak Made Easy is a vulnerability that can allow information to be leaked.
📚 Also Read:
4. File Transfer Protocol/Secure (FTP/S)
Transferring files over a computer network between clients and servers is made possible through this client-server network protocol. Cross-Site Scripting (XSS) is the most common method used by attackers to send malicious code to FTP users, in the form of a browser-side script (or cookies). There are no security measures in place for the remote FTP protocol. It is possible for any network sniffer or even a man-in-the-middle attack to intercept the usernames and passwords transmitted in clear text (MITM).
5. Post Office Protocol (POP3)
In order to retrieve emails from a remote server, an application-layer Internet protocol is used. A message can be read even when you are not connected to the internet. Firewire direct memory access or DMS attacks, which use direct hardware access in order to read or write directly to the main memory without the involvement of the operating system, target mailbox storage vulnerabilities. As a result, login credentials are sent across the network in clear text when the user connects via an unencrypted path.
6. Internet Message Access Protocol (IMAP)
An Internet email protocol that stores emails on the mail server but allows users to retrieve, see, and manipulate the messages as if they were stored locally on their devices retrieves, sees, and manipulates emails stored on the mail server. Firstly, when an email is sent over the internet, it travels through unencrypted channels. Messages, usernames, and passwords can all be intercepted by the user.. As a result of a Denial of Service (DoS) attack on the mail server, emails will not be received or sent. Viruses can be injected into the email server, which can then be distributed to recipients via infected attachments.
7. Simple Mail Transfer Protocol (SMTP)
Emails are sent using this application layer protocol. It’s possible for spammers and hackers to use an email server to send spam or malware to an open-relay owner who isn’t aware of it. Directory harvesting attacks are also used by hackers to gather valid email addresses from a server or domain. Attacks such as buffer overflows, trojan horse attacks, shell script attacks, and more are all examples of vulnerabilities.
8. Session Initiation Protocol (SIP)
Real-time sessions can be started, maintained, altered, and terminated using this signaling protocol. Voice, video, messaging, and other IP-based communication applications and services can all be used in these sessions between two or more endpoints. Such as buffer overflows, injection attacks, hijackings and so on. To mount these opponents, the attacker only has to pay a few or no charges at all. During a flood attack, an attacker sends a large amount of traffic that overwhelms the target system’s resources and prevents it from serving legitimate customers. flooding attacks Since the channels for signaling and data transfer in the SIP network infrastructure are not separated, flooding can occur easily.
9. Remote Desktop Protocol (RDP)
Developed by Microsoft, RDP is a protocol that allows users to connect to another computer via a network and share a graphical user interface (GUI) with that computer. Malware like ransomware could spread through vulnerable systems because of a vulnerability called BlueKeep. BlueKeep makes it possible for intruders to gain access to RDP servers. In the following steps, commands to steal or alter data, install malicious software, or engage in other nefarious activities can be issued by the attackers. The user does not need to be authenticated in order to exploit a vulnerability. Activation doesn’t even necessitate any input from the user.
10. Server Message Block (SMB)
Sharing files, printers, and serial ports between nodes on a network is made possible by this protocol. Inter-process communication can also be authenticated and authorized using this mechanism. The SMB Relay attack is used to carry out Man-in-the-middle attacks in the SMB protocol. The EternalBlue attack is another option. The SMBv1server in various Microsoft Windows versions mishandles specially crafted packets from remote attackers, allowing them to execute arbitrary code on the target computer.
11. Simple Network Management Protocol (SNMP)
It is an Internet Protocol (IP) standard for gathering and organizing information about managed devices on IP networks, and it is also used to alter and modify that information in order to change the behavior of those devices. DDoS attacks, such as the SNMP reflection, are a type of SNMP reflection attack. From various broadband networks, these attacks can generate attack volumes of hundreds of gigabits per second. The attacker uses a forged IP address (which is actually the victim’s IP address) to send a large number of SNMP queries to multiple connected devices, which then respond to the forged IP address. As more and more devices join in, the attack volume increases dramatically, eventually bringing down the targeted network as a result of the sheer volume of responses.
12. Secure SHell (SSH)
It’s a network protocol based on cryptography for securing and reliably running network services over an unsecure network. With the help of SSH, you can secure any network service, from remote command-line access to remote command execution to logging in. Encryption may be destabilized by a man-in-the middle (MITM) attack, allowing the adversary to access encrypted content, including passwords. As a result, an attacker who is successful is a cable that can inject commands into a terminal to alter or steal data. Using this method, malicious code can be injected into binary files and other software updates that have been downloaded via the system. In the past, this method has been employed by a variety of cybercriminals and malware packages.
13. Telnet (Terminal Network)
An application protocol for the Internet or LAN that provides bidirectional interactive text-oriented communication via a virtual terminal connection is called a virtual terminal connection. The lack of encryption in the telnet protocol is the most dangerous flaw in its security. Each and every message sent from a remote device to a networking device is sent as plain text. When an attacker gets into the device, he can see what we’re configuring, as well as the password that we entered when we connected to the device. Telnet attacks can also be classified as denial-of-service (DoS) attacks, in which the attacker suffocates the connection by flooding it with a large number of useless data frames.
14. Virtual Network Computing (VNC)
As a result of virtual network computing, a form of remote access to computer networks can be established. VNC displays another computer’s desktop and allows you to control it over a network. It is impossible to launch an attack without first committing a denial-of-service (DoS) attack or causing a system malfunction due to incorrect memory usage, which is the root cause of all other attacks. DoS attacks, buffer overflows, buffer underflows, and remote code execution are all examples of vulnerabilities and attacks.
15. User Datagram Protocol (UDP)
When transmitting data of a small size, UDP’s standard form is User Datagram Protocol. In gaming and video conferencing, UDP packets are known as datagrams, and the IP protocol is sent with them as UDP-IP. Layer four of the OSI model includes this UDP protocol as well.
16. Wi-Fi Protocols
Wireless Fidelity is the most common form of Wi-Fi, and it is a type of wireless network used to transmit and receive data over a high-speed network. Wi-Fi was invented in 1997 by Dr. John Osullivan and made available to the public in 1997.
17. Bluetooth
One of Jaap Haartsen’s inventions, Bluetooth, is a wireless network technology. Images, movies, files, music, and other data can only be transferred between the paired devices. Data transmission is not possible if the devices are not paired.
18. LTE
All of these services are provided by the Long Term Evolution (LTE), which stands for Long Term Evolution. LTE is a global open interoperable standard for wireless high-speed data that is supported by all smartphones and is used for data access on all networks. Every three to four years, a new version of LTE is released, and the current version is 4G.
19. Internet Protocols
The Internet Protocol (IP) family is a collection of closely related and widely used network protocols. In addition to the Internet Protocol, higher-level protocols such as TCP, UDP, HTTP, and FTP work with IP to provide additional functionality.
Lower-level Internet Protocols like ARP and ICMP coexist with IP. Higher-level protocols in the IP family, in general, interact with applications such as web browsers, whereas lower-level protocols interact with network adapters and other computer hardware.
20. Wireless Network Protocols
Wireless networks have become commonplace because of Wi-Fi, Bluetooth, and LTE. Network protocols designed for use on wireless networks must support roaming mobile devices and deal with issues such as variable data rates and network security.
21. Network Routing Protocols
Routing protocols are special-purpose protocols designed specifically for use by internet network routers. A routing protocol can identify other routers, manage the paths (called routes) between network message sources and destinations, and make dynamic routing decisions. EIGRP, OSPF, and BGP are examples of common routing protocols.
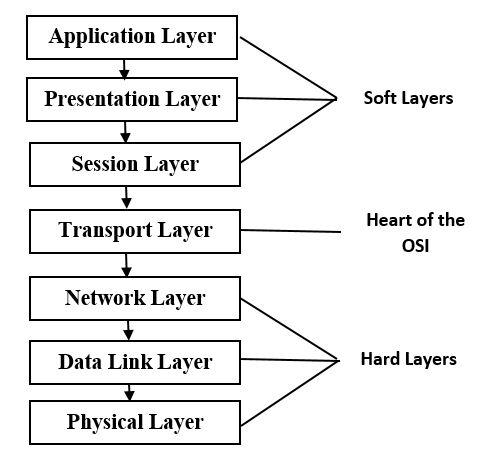
Layers of Network Protocol
Below, we’ll go over each of the seven network protocol layers.
Physical Layer
There are bits of data in the first layer, and it’s a tough one. Moving bits from one node to another is the primary function of this component. In addition to controlling bit synchronization, it lays out the interface between devices and the transmission media.
Data link layer
The second layer is the data link layer, which is a hard layer by definition. LLC and MAC are two sub-layers of this layer.
LLC: A common abbreviation for “Logical Link Control” (LLC) is the process by which software provides network-layer services.
MAC: “Media Access Control” (MAC) is the standard form of MAC, which defines the hardware’s media access processes.
Network layer
In the third layer, the network layer, data packets must be delivered from source to destination. It is a hard layer. When a network protocol uses a physical address, it is known as a network route.
Transport Layer
Fourth-layer responsibility for process-to-process communication rests with the transport layer, which serves as the OSI’s beating heart. There are two main transfer layer protocols: TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
Session Layer
This session layer is in charge of dialog synchronization and control. Systems can converse with one another while being kept in time with each other via synchronization. It’s also in charge of setting up and maintaining the links between the various programs on either end.
Presentation Layer
One type of software layer, the presentation layer, is responsible for translating, compressing, and decrypting/encrypting data.
Application layer
The application layer is the seventh layer, which is also a software layer and the desktop layer. Example: DNS and Email.
How Are Network Protocols Implemented?
Some network protocols are supported by built-in software services in modern operating systems. Web browsers, for example, contain software libraries that support the high-level protocols required for the application to function. For some lower-level TCP/IP and routing protocols, direct hardware (silicon chipsets) support is implemented for improved performance.
Each packet sent and received across a network contains binary data (ones and zeros that encode the contents of each message). Most protocols include a small header at the beginning of each packet to store information about the sender and intended destination of the message. Some protocols include a footer at the end as well. As part of moving data between devices, each network protocol can identify messages of its own type and process the headers and footers.
A protocol family is a group of network protocols that collaborate at higher and lower levels. Students of networking are typically taught about the OSI model, which conceptually organises network protocol families into distinct layers for educational purposes.
Advantages of Network Protocol
The advantages of network protocols are
- Flexibility
- Less time to transfer files
- Transfers data to different systems
- Allows programs to run on different systems
- High speed
Frequently Asked Questions (FAQs)
1. What is the difference between TCP and UDP?
TCP ensures reliable, ordered, and error-checked delivery, making it ideal for file transfers. UDP, on the other hand, is faster but unreliable, commonly used for streaming and gaming.
2. How does DNS work?
DNS translates domain names into IP addresses, allowing users to access websites without memorizing numeric addresses.
3. Why is HTTPS more secure than HTTP?
HTTPS encrypts data using SSL/TLS, preventing MITM attacks and eavesdropping, ensuring safer online transactions.
4. What are the security risks associated with RDP?
RDP is vulnerable to brute-force attacks, credential theft, and malware exploits like BlueKeep.
5. How can I protect my network from protocol vulnerabilities?
- Use encryption (SSL/TLS, VPNs, and SSH) to protect sensitive data.
- Update software regularly to patch known vulnerabilities.
- Use firewalls and intrusion detection systems to block unauthorized access.
- Disable unused protocols to reduce the attack surface.
Conclusion
Network protocols are the backbone of modern communication, ensuring the secure and efficient transfer of data across the Internet. However, each protocol comes with its own set of vulnerabilities and risks that cybercriminals can exploit. By understanding these network security risks and implementing best practices, organizations and individuals can protect their data, prevent cyberattacks, and enhance overall network security.
With cyber threats constantly evolving, staying informed about network protocol security is crucial for businesses, IT professionals, and everyday users. By adopting secure protocols, encryption techniques, and proactive defense measures, we can create a more resilient and protected digital environment.
ad


Comments are closed.