Computer Security And How To Keep Safe Your System
Computer Security is the deep matter of concern for all of us because the computers and Internet have changed our lives in many advanced ways and we are eating its ripen fruits every day, either making video calls, shopping online or booking a ride on your smartphone. It is everywhere from small villages to big metros and we are eyewitnessing it’s virtual presence everywhere from airline ticket booking to sending a charity fund online.

ad
Computer Security Software
Unfortunately, this very big web network and its associated technologies also have brought in their wake. Similarly, we are facing an increasing number of security threats at every moment. The most effective way to protect yourself from these threats and attacks is to be aware of standard cybersecurity practices. This article on “What is Computer Security?” presents an introduction to computer security and its major fundamentals.
It also pays off to seek business IT support and entrust your computer security software and overall cybersecurity to real experts. Outsourcing to an IT company for managed IT services or hiring an in-house IT professional can provide many advantages to your company. An IT specialist can safeguard your hardware and software systems, allowing you to focus on other areas of your business. You can save time, effort, and resources by having the company resolve computer security issues too.
| Read More: Managed IT Services Edison New Jersey For All Your Digital Security Concerns
ad
Impact of computer security breaches
Cybercriminals use highly sophisticated methods to victimize small businesses and even corporations. From phishing to malware, almost all businesses are at risk of cyberattacks. If you use a computer or any online platform to conduct business, there’s always a vulnerability or risk of a security breach.
Serious financial damage has been caused by security breaches on internet connected computers, but because there is no standard model for estimating the cost of an incident, the only data available is that which is made public by the organizations involved. “Several computer security consulting firms produce estimates of total worldwide losses attributable to virus and worm attacks and to hostile digital acts in general. The 2003 loss estimates by these firms range from $13 billion (worms and viruses only) to $226 billion (for all forms of covert attacks). The reliability of these estimates is often challenged; the underlying methodology is basically anecdotal.” Security breaches continue to cost businesses billions of dollars but a survey revealed that 66% of security staffs do not believe senior leadership takes cyber precautions as a strategic priority.
However, reasonable estimates of the financial cost of security breaches can actually help organizations make rational investment decisions. According to the classic Gordon-Loeb Model analyzing the optimal investment level in information security, one can conclude that the amount a firm spends to protect information should generally be only a small fraction of the expected loss (i.e., the expected value of the loss resulting from a cyber/information security breach).
Who are at risk?
As mentioned, anyone who uses a computer is at risk of a data or security breach. Because of the utilization of digital systems for production, data gathering, reporting, marketing, and sales, almost every sector or industry is affected.
The growth in the number of computer systems, and the increasing reliance upon them of individuals, businesses, industries, and governments means that there is an increasing number of systems at risk.
- Aviation
- Banking and Finance system
- Utilities & Equipments
- Consumer Products
- Large Corporations
- Automobiles
- Governments
- Energy Sector
- Medical Systems
- Financial systems
What is computer security?
Mainly, Computer security is the protection of computer systems and information from harm, theft, and unauthorized use or hacking of the system. It is the process of preventing and detecting bugs, serious virus threats and unauthorized activity on your computer system or damage caused to the hardware, software or data by the outside attack.
Often people confuse computer security with other related terms like information security and cybersecurity. One way to ascertain the similarities and differences among these terms is by asking what is being secured. For example,
- Computer Security means securing a standalone machine by keeping it updated and patched from any harm or unwanted and unauthorized activity
- Cybersecurity is defined as protecting computer systems, which communicate and collaborate over the computer networks
- Information security is securing information from unauthorized access, altering or modification & deletion
It’s important to understand the distinction between these words, though there isn’t necessarily a clear consensus on the meanings and the degree to which they overlap or are interchangeable.
So, Computer security can be defined as controls that are put in place to provide confidentiality, integrity, and availability for all components of computer systems. Let’s elaborate on the definition.
Components of system
Computers are becoming highly complex, with new features being added, updated, or enhanced every year, such as the operating system. However, the components of computer systems can also be vehicles for cybercriminals to reach their prey. So, it’s crucial to know the components of your computer system and find ways to protect and update them to prevent security breaches.
The components of a computer system that needs to be protected are:
- Hardware, the physical part of the computer, like the system memory and disk drive
- Firmware, permanent software that is etched into a hardware device’s nonvolatile memory and is mostly invisible to the user
- Software, the programming that offers services, like operating system, word processor, the internet browser to the user
The CIA Triad
Computer security is mainly concerned with three main areas:
- Confidentiality is ensuring that information is available only to the intended audience
- Integrity is protecting information from being modified by unauthorized parties
- Availability is protecting information from being modified by unauthorized parties
In simple language, computer security is making sure information and computer components are usable but still protected from people or software that shouldn’t access it or modify it.
Now moving forward with this ‘What is Computer Security?” article let’s look at the most common security threats.
Computer system threats
Computer security threats are possible dangers that can possibly hamper the normal functioning of your computer. In the present age, cyber threats are constantly increasing as the world is going digital. The most harmful types of computer security are:
Computer Worm
 A computer worm is a software program that can copy itself from one computer to another, without human interaction. The potential risk here is that it will use up your computer hard disk space because a worm can replicate in greate volume and with great speed.
A computer worm is a software program that can copy itself from one computer to another, without human interaction. The potential risk here is that it will use up your computer hard disk space because a worm can replicate in greate volume and with great speed.
Viruses
 A computer virus is a malicious program which is loaded into the user’s computer without the user’s knowledge. It replicates itself and infects the files and programs on the user’s PC. The ultimate goal of a virus is to ensure that the victim’s computer will never be able to operate properly or even at all.
A computer virus is a malicious program which is loaded into the user’s computer without the user’s knowledge. It replicates itself and infects the files and programs on the user’s PC. The ultimate goal of a virus is to ensure that the victim’s computer will never be able to operate properly or even at all.
Keylogger
 Also known as a keystroke logger, keyloggers can track the real-time activity of a user on his computer. It keeps a record of all the keystrokes made by using keyboard. Keylogger is also a very powerful threat to steal people’s login credential such as username and password
Also known as a keystroke logger, keyloggers can track the real-time activity of a user on his computer. It keeps a record of all the keystrokes made by using keyboard. Keylogger is also a very powerful threat to steal people’s login credential such as username and password
Botnet
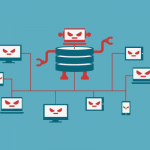 A botnet is a group of computers connected to the internet, that have been compromised by a hacker using a computer virus. An individual computer is called ‘zombie computer’. The result of this threat is the victim’s computer, which is the bot will be used for malicious activities and for a larger scale attack like DDoS.
A botnet is a group of computers connected to the internet, that have been compromised by a hacker using a computer virus. An individual computer is called ‘zombie computer’. The result of this threat is the victim’s computer, which is the bot will be used for malicious activities and for a larger scale attack like DDoS.
Rootkit
 A rootkit is a computer program designed to provide continued privileged access to a computer while actively hiding its presence. Once a rootkit has been installed, the controller of the rootkit will be able to remotely execute files and change system configurations on the host machine.
A rootkit is a computer program designed to provide continued privileged access to a computer while actively hiding its presence. Once a rootkit has been installed, the controller of the rootkit will be able to remotely execute files and change system configurations on the host machine.
Phishing
 Disguising as a trustworthy person or business, phishers attempt to steal sensitive financial or personal information through fraudulent email or instant messages. Phishing is unfortunately very easy to execute. You are deluded into thinking it’s legitimate mail and you may enter your personal information.
Disguising as a trustworthy person or business, phishers attempt to steal sensitive financial or personal information through fraudulent email or instant messages. Phishing is unfortunately very easy to execute. You are deluded into thinking it’s legitimate mail and you may enter your personal information.
These are perhaps the most common security threats that you’ll come across. Apart from these, there are others like spyware, wabbits, scareware, bluesnarfing, and many more. Fortunately, there are ways to protect yourself against these attacks.
Spoofing
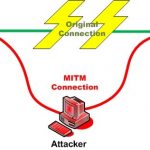 Spoofing is the act of masquerading as a valid entity through falsification of data (such as an IP address or username), in order to gain access to information or resources that one is otherwise unauthorized to obtain. There are several types of spoofing, including:
Spoofing is the act of masquerading as a valid entity through falsification of data (such as an IP address or username), in order to gain access to information or resources that one is otherwise unauthorized to obtain. There are several types of spoofing, including:
- Email spoofing, where an attacker forges the sending (From, or source) address of an email.
- IP address spoofing, where an attacker alters the source IP address in a network packet to hide their identity or impersonate another computing system.
- MAC spoofing, where an attacker modifies the Media Access Control (MAC) address of their network interface to pose as a valid user on a network.
- Biometric spoofing, where an attacker produces a fake biometric sample to pose as another user.
Computer Security Practices
A state of “computer security” is the conceptual ideal, attained by the use of the three processes: threat prevention, detection, and response. These processes are based on various policies and system components. There is much need for one to arm oneself with information and resources to safeguard against these complex and growing computer security threats and stay safe online. Some preventive steps you can take include:
- Stay up-to-date on the latest software and news surrounding your devices and perform software updates as soon as they become available
- Security by design, or alternately secure by design, means that the software has been designed from the ground up to be secure. In this case, security is considered the main feature.
- Avoid clicking on email attachments unless you know the source
- Change passwords regularly, using a unique combination of numbers, letters, and case types
- Use the internet with caution and ignore pop-ups, drive-by downloads while surfing
- Taking the time to research the basic aspects of computer security and educate yourself on evolving cyber-threats
- Perform daily full system scans and create a periodic system backup schedule to ensure your data is retrievable should something happen to your computer.
- User account access controls and cryptography can protect systems files and data, respectively.
- Firewalls are by far the most common prevention systems from a network security perspective as they can (if properly configured) shield access to internal network services, and block certain kinds of attacks through packet filtering. Firewalls can be both hardware- or software-based.
- Intrusion Detection System (IDS) products are designed to detect network attacks in progress and assist in post-attack forensics, while audit trails and logs serve a similar function for individual systems.
- “Response” is necessarily defined by the assessed security requirements of an individual system and may cover the range from simple upgrade of protections to notification of legal authorities, counter-attacks, and the like. In some special cases, complete destruction of the compromised system is favored, as it may happen that not all the compromised resources are detected.
- Secure your computer physically by:
- Installing reliable, reputable security and anti-virus software
- Activating your firewall, because a firewall acts as a security guard between the internet and your local area network.
Apart from these, there are many ways you can protect your computer system. Aspects such as encryption and computer cleaners can assist in protecting your computers and their files.
Unfortunately, the number of cyber threats is increasing at a rapid pace and more sophisticated attacks are emerging. So, having a good foundation in cybersecurity concepts will allow you to protect your computer against ever-evolving cyber threats.
If you have any suggestion/modification or any other concern related to the topic, please mention it in the comments section and we will get back to you.
ad


Comments are closed.