What Is Zero Trust Network Access?
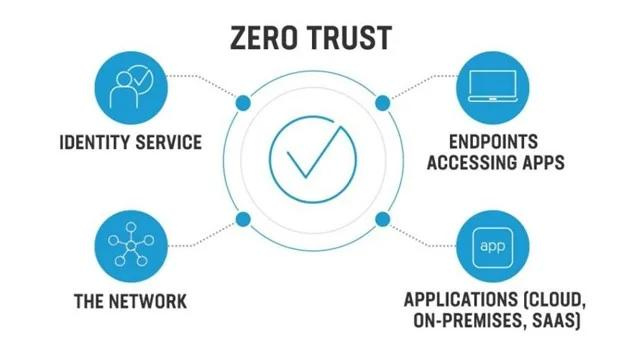
Zero Trust Network Access (ZTNA) is an IT security solution designed to offer secure remote access to an organization’s applications, data, and services through well-defined access control policies. ZTNA distinguishes itself from virtual private networks (VPNs) by providing access exclusively to designated services or applications, while VPNs allow access to an entire network. With the growing trend of users accessing resources remotely, whether from home or other locations, ZTNA solutions play a crucial role in bridging gaps present in other secure remote access technologies and methodologies.
ad
How does ZTNA work?
Access to specific applications or resources is granted only after users are authenticated by the ZTNA service. Once authenticated, ZTNA establishes a secure, encrypted tunnel to allow access to the designated application, providing an additional layer of security by hiding applications and services from visible IP addresses.
This approach makes ZTNAs similar to Software-Defined Perimeters (SDPs), as they use the ‘dark cloud’ concept to limit user visibility to authorized applications and services. This strategy also defends against lateral attacks, ensuring that even if an attacker gains access, they cannot scan and locate other services.
ZTNA Use Cases
ad
Authentication and Access – The main purpose of ZTNA is to offer highly specific access based on a user’s identity. Unlike IP-based VPNs that provide broad network access upon authorization, ZTNA allows limited, finely tuned access to particular applications and resources. ZTNA enhances security by implementing location- or device-specific access control policies, which can effectively block unwanted or compromised devices from reaching the organization’s resources. This stands in contrast to certain VPNs that grant employee-owned devices the same access privileges as on-premises administrators.
Holistic Control and Visibility – Because ZTNA does not inspect user traffic post-authentication, there could be potential issues if a malicious employee misuses their access or if a user’s credentials are lost or stolen. Integrating ZTNA into a Secure Access Service Edge (SASE) solution enables organizations to benefit from comprehensive security, scalability, and network capabilities necessary for secure remote access. Additionally, post-connection monitoring helps prevent data breaches, malicious activities, or compromised user credentials.
Benefits of ZTNA
ZTNA provides a solution for connecting users, applications, and data even when they are not located within the organization’s network, a scenario increasingly common in today’s multi-cloud environments where applications are based on microservices across multiple clouds and on-premises. Modern organizations require their digital assets to be accessible anywhere, anytime, from any device, serving a distributed user base.
ZTNA meets this requirement by offering granular, context-aware access to business-critical applications without exposing other services to potential attackers.
The ZTNA model, coined by Gartner, aims to eliminate the granting of excessive trust to employees, contractors, and other users who require only limited access. The model embodies the concept that nothing should be trusted until proven trustworthy, and importantly, trust must be revalidated whenever there is a change in connection details (such as location, context, IP address, etc.).
What is the difference between VPN and ZTNA?
There are several distinctions between VPNs and ZTNA. Primarily, VPNs are engineered to provide network-wide access, while ZTNAs grant access to specific resources and necessitate frequent reauthentication.
Some drawbacks of VPNs compared to ZTNAs include:
Resource utilization – As the number of remote users increases, the VPN’s workload may result in unexpectedly high latency and necessitate the addition of new resources to meet growing demand or peak usage times. This can also strain the IT organization’s manpower.
Flexibility and Agility – VPNs lack the granularity of ZTNA. Moreover, installing and configuring VPN software on all the end-user devices that need to connect to enterprise resources can be challenging. Conversely, it is much simpler to adjust or remove security policies and user authorization based on immediate business requirements using ZTNAs, which leverage ABAC (attribute-based access control) and RBAC (role-based access control) to streamline this process.
Granularity – Within a VPN perimeter, once a user gains access, they have access to the entire system. ZTNAs adopt the opposite approach, granting no access unless an asset – application, data, or service – is specifically authorized for that user. Unlike VPNs, ZTNAs provide continuous identity verification based on identity authentication. Each user and device undergo verification and authentication before being granted access to specific applications, systems, or other assets. VPNs and ZTNAs can be employed in conjunction with each other, such as to enhance security on a particularly sensitive network segment, providing an additional security layer in case the VPN is compromised.
How do you set up ZTNA?
Implementing ZTNA can be approached in two ways: endpoint initiated and service initiated.
In endpoint-initiated ZTNA architecture, users initiate access to an application from their endpoint-connected devices, similar to an SDP. A device-installed agent communicates with the ZTNA controller, which handles authentication and connects to the desired service.
Conversely, in service-initiated ZTNA, the connection is initiated by a broker between the application and the user. This requires a lightweight ZTNA connector to be positioned in front of the business applications, whether on-premises or in cloud providers. Once the outbound connection from the requested application authenticates the user or another application, traffic flows through the ZTNA service provider, isolating applications from direct access via a proxy. This approach doesn’t require an agent on end-user devices, making it more suitable for unmanaged or BYOD devices for consultant or partner access.
There are two delivery models for zero-trust network access: stand-alone ZTNA or ZTNA as a service.
In stand-alone ZTNA, the organization must deploy and manage all ZTNA elements, situated at the edge of the environment (cloud or data center) for brokering secure connections. While suitable for organizations hesitant to adopt cloud solutions, this approach adds to deployment, management, and maintenance burdens.
ZTNA as a cloud-hosted service allows organizations to leverage the cloud provider’s infrastructure for everything from deployment to policy enforcement. With this model, the organization acquires user licenses, deploys connectors in front of secured applications, and relies on the cloud provider or ZTNA vendor for connectivity, capacity, and infrastructure. This streamlines management and deployment, ensuring the optimal traffic path for lowest latency for all users.
ZTNA 2.0
Zero Trust Network Access 2.0 surpasses the constraints of traditional ZTNA solutions, offering secure connections to achieve enhanced security outcomes for businesses operating with hybrid workforces. ZTNA 2.0 provides:
- Genuine least-privileged access: Applications are identified based on App-IDs at Layer 7, facilitating precise access control at the application and sub-application levels, regardless of network constructs such as IP and port numbers.
- Continuous trust verification: Trust is continuously evaluated after granting access to an application, considering changes in device posture, user behavior, and application behavior. If any suspicious activity is detected, access can be immediately revoked.
- Ongoing security inspection: Thorough and continuous inspection is conducted on all traffic, including permitted connections, to thwart all types of threats, including zero-day threats. This is particularly crucial in scenarios involving the misuse of legitimate user credentials to launch attacks against applications or infrastructure.
- Data protection: Uniform data control measures are enforced across all enterprise applications, encompassing both private applications and Software as a Service (SaaS) offerings, under a single Data Loss Prevention (DLP) policy.
- Application security: Comprehensive security measures are consistently applied to all enterprise applications, spanning modern cloud-native applications, legacy private applications, SaaS applications, as well as applications utilizing dynamic ports and those employing server-initiated connections.
ZTNA 1.0 vs. ZTNA 2.0
Over the past 24 months, the most notable change in networking and security has been the transformation of work from a physical destination to a flexible activity performed from various locations. Hybrid work has become the standard, leading to our applications and users being spread across multiple locations, thus significantly increasing our vulnerability to cyberattacks. Concurrently, there has been a rise in the complexity and frequency of cyberattacks targeting this expanded attack surface.
| ZTNA Version | Features |
|---|---|
| ZTNA 1.0 |
|
| ZTNA 2.0 |
|
FAQ’s
What is ZTNA and how does it work?
ZTNA is a security solution for remote access. It verifies user identity before granting access to specific applications, ensuring secure connections through encrypted tunnels.
What are the top use cases for ZTNA?
ZTNA is used for precise access control and comprehensive security monitoring, especially for remote work environments.
What are the benefits of using ZTNA?
ZTNA offers secure remote access, granular access control, and continuous identity verification, enhancing overall security for organizations.
How does ZTNA differ from VPNs?
ZTNA provides specific access to applications, unlike VPNs which grant broader network access. ZTNA also offers continuous identity verification for stricter access control.
What are the key features of ZTNA 2.0 compared to ZTNA 1.0?
ZTNA 2.0 offers improved access control, continuous trust verification, and enhanced security measures for data protection and application security.
How can ZTNA be implemented?
ZTNA can be implemented either through endpoint-initiated access or service-initiated access, providing secure connections for remote users.
Conclusion
Zero Trust Network Access (ZTNA) is a critical security solution for modern remote work environments. With its granular access control and continuous verification features, ZTNA ensures secure connections and protects against cyber threats. As remote work becomes more prevalent, adopting ZTNA is essential for maintaining strong security measures and mitigating risks effectively.
ad


Comments are closed.