What is SFTP – Secure File Transfer Protocol | How It Works?
Secure File Transfer Protocol, SFTP implements FTP commands over a secure connection and is incorporated into SSH. It can replace FTP servers in most situations.
| What is SFTP?
Secure File Transfer Protocol (SFTP) is a secure variant of File Transfer Protocol (FTP) and a component of the SSH Protocol for facilitating data transfer and access through a Secure Shell (SSH) data stream. SSH File Transfer Protocol is also known as SFTP. It offers a safe connection for transferring files and traversing filesystems on both local and remote systems. SFTP encrypts data via an SSH connection, and WinSCP and SFTP clients can be used to transfer files. Typically, it can serve as a drop-in substitute wherever an FTP server is still required.
FTP, the File Communication Protocol, was a popular, unencrypted means of file transfer between two remote servers. Due to a lack of security, most contemporary software has deprecated it as of 2022, and it can only be used in legacy applications.
SFTP is generally preferable to FTP due to its inherent security features and ability to piggyback on an SSH connection. FTP is an unsecure protocol that should only be used in specific circumstances or on trusted networks.
This post will illustrate how to use SFTP’s interactive command line interface, despite the fact that Secure File Transfer Protocol is integrated into a variety of graphical programs.
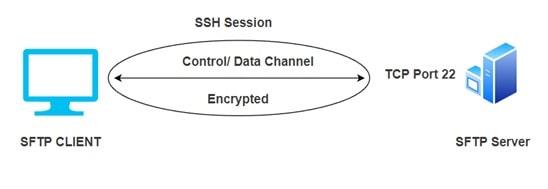
| How SFTP works?
SFTP utilizes a secure shell data stream to function. It establishes a secure connection and provides enhanced data transfer security. It employs a variety of encryptions to aid in the transfer of data and ensure that data being processed cannot be read. The SSH keys must be generated beforehand, which helps prevent fraudulent users from connecting to the server. The system employs a client-server design. Typically, the server hosts the data. Even if this server is located in a different location, the client can readily access the data by issuing a request. When a user clicks on a file, the request travels over the network before reaching the server. This data is then transmitted to the server that requested it. The user will finally obtain the file and modify it to their specifications. The SFTP protocol ensures that all transferred files are encrypted. The SSH keys provide the transfer of the public key to any accessible system.
Some of the information a system needs to configure for SFTP Client:
Server Hostname
Provide the server’s hostname or IP address.
Port Name
The client’s TCP port of choice when connecting
Ex: Port no – 22 or other
Security Protocol
Choose the protocol you wish to use to create a secure connection.
Ex: SFTP, FTP, SCP, or other
Username
Username by which the client wants to connect to the server
Ex: Username: Admin
Password
The password assigned to the user.
Ex: ******
To prevent password sniffing and the exposure of sensitive data in plain text, SFTP transfers files via SSH and encrypted FTP instructions. Since the server must authorize the client, SFTP defends against man-in-the-middle attacks.
| How to Connect with Secure File Transfer Protocol
Secure File Transfer Protocol employs the SSH protocol by default for authentication and to establish a secure connection. Because of this, the exact same authentication mechanisms as SSH are available.
Although you can authenticate with passwords by default, it is recommended that you generate SSH keys and send your public key to any system you need to access. This is far more secure and can save you time over time.
If you have not already set up SSH keys to access your server, please refer to this guide.
If you are able to connect to the system using SSH, you have met all of the prerequisites for using SFTP to manage files. Use the command below to verify SSH access.
![]()
If that works, exit back out by typing:
![]()
Now we can establish an SFTP session by issuing the following command:
![]()
You will connect to the remote system, at which point the prompt will change to SFTP.
If you are using a non-default SSH port (not port 22), you can initiate an SFTP session as follows:
![]()
This will establish a connection to the remote system using the specified port.
How to Transfer File by Using SFTP?
SFTP’s encryption is performed via an SSH connection. There are two methods for transferring files using Secure File Transfer Protocol:
- Using WinSCP
- Using SFTP Client
1. Using WinSCP
To transfer files using WinSCP, you must follow the instructions below.
- Download and install WinSCP.
- When the screen launches, click on New.
- Fill in the information in specified fields as below:
- File Protocol: SFTP
- Hostname: You can enter the hostname from where you need the data to be transferred
- Username and Password: The username and password for your account on that server should be specified.
- Port: The port is usually 22.
- A warning indicating you are about to connect to a remote machine may display. You can select Yes to dismiss this warning.
- Once this is complete, you will be connected to the specified server and a window with two windows will appear. One window will display all data on a server, while the other will display your Windows system files. You can drag and drop files from the server to the Windows machine or vice versa with relative ease.
2. Using SFTP Client
Here, you can utilize Cyberduck. You can download and launch this software, then select Open Connection from the menu. Similar to WinSCP, all details such as File protocol, hostname, username, and password may be entered, and data can be transferred between source and destination.
3. What is SFTP Port Number
SFTP port number is the SSH port 22. It is essentially an SSH server. The SFTP protocol cannot be begun until the user has logged in to the server via SSH. On servers, there is no specific SFTP port exposed. There is no need to configure additional holes in firewalls.
| SFTP Encryption
The importance of encryption in Secure File Transfer Protocol is significant. It secures data from hackers and other unauthorized individuals by transforming it into an unreadable format, so no one can access or alter it during transmission. After it reaches its destination, authorized users using the given key change the data back into a readable format. During the file transfer, the SSH Encryption technique is employed to safeguard the operation. It can be achieved in numerous ways:
Before initiating the file transfer, it is possible to encrypt the network and generate the password to log in to the network using the automatically formed pairs of private and public keys.
Alternatively, the manually produced private and public keys can be used to execute the authentication procedure, allowing the user to log in without a password.
SFTP applications:
- It is mostly used to communicate sensitive data between two sources in a secure manner, as well as to conduct audits and transmit data and reports between the company and regulatory bodies.
- SFTP facilitates the creation, import, export, and deletion of files and directories. This facilitates easy data access from wherever.
- Using an upgraded authentication procedure, it is also possible to share confidential files.
Advantages of SFTP
Below are the different advantages:
- Data security: Due to the prevalence of sensitive and personal data, data security is a major concern today. You desire complete security for your files; SFTP offers multiple methods for Secure Data Transfer. SSH File Transfer necessitates the use of keys or usernames and passwords to prevent unauthorized access.
- Speedy and Efficient: SFTP servers facilitate the transfer of huge files with ease and efficiency. Multiple files can be sent simultaneously from one server to another. Due to this, considerable time is saved. This strategy is superior than email and cloud storage. It enables the direct and timely exchange of documents, forms, and business-critical information with the customer.
- Fewer risks during data exchange: SFTP employs encryption, authentication using a public key, data integrity, and host authentication. All data is encrypted prior to transmission. This renders the data unreadable during transmission, and only the recipient can decrypt the data. The authentication with a public key ensures that no imposter uses the intended data. For authentication purposes, a username and password are required. The data is also examined to determine if it comes from a reliable source. In addition, clients and suppliers are validated before the link is established.
- Powers data accessibility: Accessibility-wise, SFTP provides a centralized area for storing all corporate files and allows you entire control and freedom over it.
- No hardware required: Using SFTP requires no additional hardware, such as servers or infrastructure; once you log into SFTP services, all amenities are immediately available for usage.
Conclusion
Secure file transfer protocol uses secure shell encryption to deliver and receive files securely. Then we listed SFTP client configuration information. SFTP is used for HIPAA compliance, which controls sensitive health information. SSH Encryption can be used to secure file transfers in many ways. Then we examined SFTP’s applications and advantages.
ad



Comments are closed.