What is an Endpoint Protection Platform?
An endpoint protection platform (EPP) is an all-encompassing software solution designed to safeguard network endpoints and, consequently, the entire network. Endpoints are often the most susceptible parts of a computing network. Ensuring their security is crucial for maintaining smooth business operations and protecting data. By definition, EPPs concentrate exclusively on threat prevention, integrating various defensive tools into a single framework.
What Is an Endpoint?
An endpoint refers to parts of a network where communications originate and/or are received. In this context, communications can include direct human input, computer-to-computer interactions (e.g., servers), or data from environmental sensors (e.g., IoT devices). Traditionally, desktop computers or other computing terminals are considered endpoints, while infrastructure like routers and cables are typically not.
Nowadays, many types of devices can function as endpoints, beyond just dedicated terminals. Examples of modern endpoints include:
ad
- Desktops
- Laptops
- Smartphones
- Smartwatches
- Point-of-Sale (POS) systems
- Internet of Things (IoT) devices
- Medical devices
- Servers
Origins and Purpose of EPPs
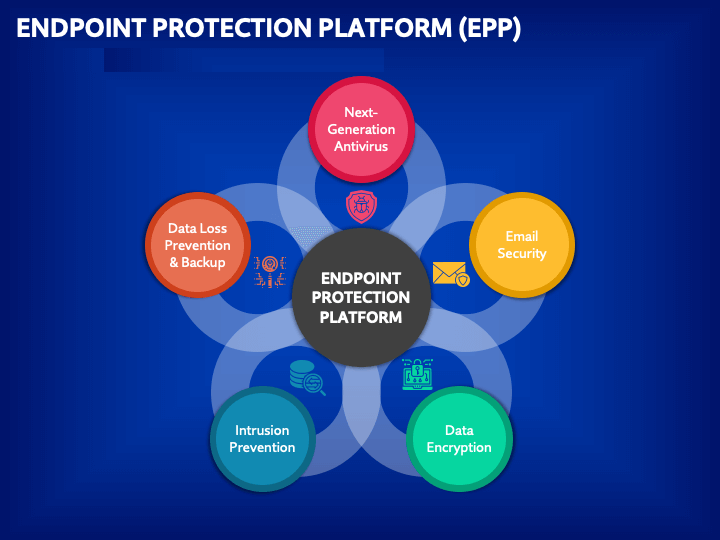
EPPs were developed to detect attacks that traditional endpoint security might miss, integrating tools like antivirus protection, data encryption, and intrusion prevention into a single cloud-managed system. This consolidation allows IT personnel to monitor all endpoints from one location, enabling more comprehensive and automated data sharing and analysis. This integration also facilitates complex threat analysis that wouldn’t be possible with isolated tools. Due to their cloud-managed nature, EPPs can leverage global threat data, enhancing overall threat prevention by benefiting from the experiences of other networks.
EPPs may also include endpoint detection and response (EDR) capabilities, aiding security personnel in responding to threats that bypass the system’s defenses. However, EDR is not a feature of all EPP platforms, so IT staff should consider whether this capability is included when selecting an EPP system.
Why Is Endpoint Security Via EPPs Important?
In a network setting, endpoints are typically seen as the most vulnerable part of any system. This vulnerability arises primarily from the personnel involved and the diverse types and large number of endpoints used to access a network. A system compromise can lead to potential cyber-attacks, which can be extremely costly in terms of both direct financial impact and the efforts required for remediation.
Individuals with varying levels of computer knowledge and cybersecurity training use computing systems that access a company’s network. These activities can occur in a wide range of settings, which may not be well-controlled or easily monitored by company IT staff. For instance, an employee with extensive IT security knowledge might avoid opening a suspicious email, while another, less security-conscious employee might unwittingly install “networkscrambler.exe” on their endpoint. Employees may use a desktop at the office or prefer working on a 5-year-old iPad via a coffee shop’s unsecured WiFi.
There could be ten employees or 10,000, each with their own personal and device profiles, engaging in a wide variety of activities daily. Each of these person/device combinations poses a potential (and likely unintentional) threat to the network.
The variety of different threats not only presents a problem but also creates a massive attack surface. While most employees may practice good data hygiene, a comprehensive EPP allows staff to monitor all endpoints simultaneously, preventing a single careless employee from compromising the network.
EPP vs. EDR
EPPs provide a comprehensive framework for IT personnel to protect endpoints and the overall network. Some EPPs also include endpoint detection and response (EDR) capabilities, allowing for threat detection and response after a network has been breached.
While many EPPs incorporate EDR functions, these are distinct features. Ideally, an EPP should prevent all threats, but breaches can still occur, necessitating a response plan and system. This must be balanced with considerations of system usability and cost, and IT staff might also explore other EDR options independent of their EPP.
Generally, having more tools in one’s cybersecurity arsenal is advantageous. However, IT staff must be properly trained in their use and the system must be effectively deployed. An unused or unknown capability is often equivalent to not having it at all.
How Attackers Evade Traditional Endpoint Security
The main driving force behind the development of endpoint protection platforms stemmed from the fact that attackers were adept at circumventing traditional solutions employed by SecOps teams. Essentially, attackers had surpassed the capabilities of traditional endpoint security measures, enabling them to linger undetected within networks for prolonged durations.
Ways Attackers Bypass Traditional Endpoint Security
Fileless Ransomware
Due to the absence of a detectable file, traditional endpoint security struggles to impede fileless ransomware delivery techniques. As indicated by a cybersecurity report from SecureWorld, fileless attacks surged by 18% in the first half of 2019 compared to the latter half of 2018. Only with an Endpoint Protection Platform (EPP) can you monitor behaviors to detect patterns indicative of fileless attack methods.
New Attack Techniques Available
Cybercriminals have either pilfered or developed advanced attack methods, which are readily accessible for purchase or openly shared on the internet and dark web. By employing these scripts and tactics, attackers can blend their activities seamlessly into normal network behavior, evading detection.
Outdated Endpoints
The threat landscape evolves rapidly, prompting security vendors to swiftly develop patches and updates to counter emerging threats. However, the pace of updates often surpasses the capabilities of SecOps teams, especially in the absence of robust patch management and automation. Moreover, endpoint agents frequently fail, leaving individual endpoints vulnerable. According to a 2019 Global Endpoint Security Trends report, 35% of endpoint breaches stem from existing vulnerabilities. Since endpoint protection platforms are typically cloud-based, they can remain continuously updated to shield endpoints from the latest threats.
Multiple Data Sources
Traditional endpoint security solutions operate relatively independently from the broader security stack. Consequently, it necessitates multiple systems to monitor activity at a single endpoint and track any suspicious behavior across the network during an investigation. Endpoint protection platforms consolidate data from all security solutions within the platform, providing a unified source of information for easy access and investigation of alerts.
Filtered Endpoint Data
Many endpoint security solutions filter out endpoint data deemed unrelated to a threat based on known behavior patterns and Indicators of Compromise (IOCs). With attackers employing more sophisticated techniques, they rely on endpoint data filtering to obfuscate their activities, thereby hindering SecOps from identifying new patterns. By continuously capturing endpoint activity data, organizations can discern these novel techniques and anticipate emerging threats.
FAQ’s
What exactly is an Endpoint Protection Platform (EPP)?
An EPP is a comprehensive software solution designed to safeguard network endpoints, thereby securing the entire network. It integrates various defensive tools into a single framework, focusing primarily on threat prevention.
Why are endpoints considered the most vulnerable parts of a computing network?
Endpoints are vulnerable due to the diverse types and large number of devices accessing the network, along with the varying levels of cybersecurity knowledge among users. This vulnerability poses a significant risk to network security and data protection.
How do Endpoint Protection Platforms (EPPs) contribute to network security?
EPPs consolidate defensive tools, allowing IT personnel to monitor all endpoints from a single location. They facilitate automated data sharing and analysis, enabling comprehensive threat detection and prevention, which wouldn’t be possible with isolated tools.
What role does Endpoint Detection and Response (EDR) play in EPPs?
EDR capabilities, included in some EPPs, aid in responding to threats that bypass the system’s defenses. While not all EPPs include EDR features, they provide an additional layer of security, enhancing the overall effectiveness of the platform.
Why is it crucial to continuously update endpoint security measures?
The threat landscape evolves rapidly, and outdated endpoints pose a significant risk to network security. Continuous updates ensure that endpoints are protected against the latest threats, reducing the likelihood of breaches and data compromises.
How do attackers evade traditional endpoint security measures?
Attackers often employ advanced techniques, such as fileless ransomware and sophisticated attack methods, to bypass traditional endpoint security. These methods enable them to remain undetected within networks for extended periods, posing a significant challenge to cybersecurity professionals.
What benefits do Endpoint Protection Platforms offer over traditional endpoint security solutions?
EPPs provide a comprehensive framework for protecting endpoints and the overall network. They offer centralized monitoring, automated threat detection, and integration with other security solutions, enhancing overall network security and reducing the risk of data breaches.
How can organizations ensure effective deployment and utilization of Endpoint Protection Platforms?
Organizations should ensure proper training for IT staff and effective deployment of EPPs to maximize their effectiveness. Additionally, regular monitoring and updates are essential to keep pace with evolving threats and maintain strong network security posture.
Conclusion
Endpoint Protection Platforms (EPPs) are essential for safeguarding network endpoints and ensuring overall security. By integrating defensive tools, EPPs empower IT teams to monitor and protect endpoints effectively. With continuous updates and proactive cybersecurity measures, organizations can defend against evolving threats and safeguard their networks and data.
ad


Comments are closed.