What Is HTTP Proxy
HTTP-proxy is a content filter. It scans Web traffic for viruses and other intrusions. It prevents HTTP server from attacks.
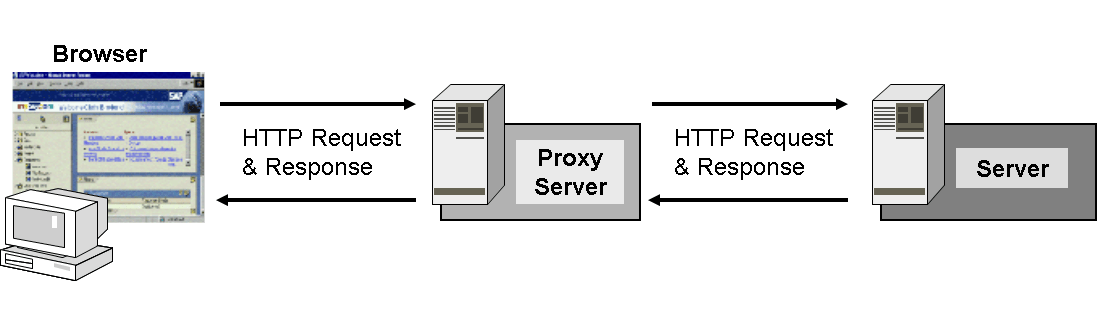
As both an HTTP Client and an HTTP Server, an HTTP Proxy provides security, management, and caching functionality. The HTTP Proxy forwards HTTP Client requests from a Web browser to the Internet and caches Internet content.
Proxy server benefits consist of:
ad
- As a precaution, identity anonymity is maintained.
- Increasing caching speeds
- Allowing access to restricted sites.
- Implementing access rules for particular websites.
- Permitting a website to send queries to external servers.
- Evading security measures.
- Bypassing Internet filtering to access content that is restricted.
What does HTTP stand for?
HTTP is an application-level protocol that facilitates file transfer over the World Wide Web. HTTP appears at the beginning of every URL or online address. It operates on the Transmission Control Protocol/Internet Protocol (TCP/IP) and Google’s QUIC protocol to make the web quicker and more efficient.
ad
HTTP enables web browsers to interface with web servers and transmit requests. Tim Berners-Lee, the inventor of the World Wide Web, proposed the HTTP protocol in 1989. HTTP/1.0 was stateless and performed each client request separately. This means that after a transaction is complete, the server and browser terminate their connection. Since then, it has evolved, with the most recent version, HTTP/3, utilising the QUIC protocol.
Since HTTP lacks intrinsic security features, websites have adopted HTTP Secure since 2010. (HTTPS). HTTPS adds the SSL protocol to HTTP in order to encrypt browser-to-server communication.
What does the term proxy mean?
Proxy refers to a person allowed to do an activity on behalf of another, and proxy servers provide this service online. A proxy server functions as a bridge between users and the Internet, preventing access to anyone outside the network. Regular Internet access via a web browser provides immediate website connection. A proxy, however, works as an intermediary that communicates with websites on behalf of users.
When computers connect to the internet, they utilize an IP address that assigns a return address to outgoing data. Similarly, a proxy, whether private or open, serves as another computer with its own IP address on the Internet. A user’s browser connects to the proxy, which then redirects the user’s traffic to the website they are visiting, receives the response, and returns it to the user.
How Does HTTP Proxy work?
Cybercriminals are a constant threat to businesses online, which is an unfortunate reality in today’s world. This is where an HTTP proxy comes in handy, because it can filter out any suspicious activity over your connection. An HTTP proxy server quickly blocks any potential attacks from external networks by regularly inspecting web traffic for malware.
Before forwarding web traffic to an internal web client, the HTTP proxy examines its origin. This reduces the likelihood of potentially harmful content entering your network and allows buffer overflow attacks to be avoided.
You can tailor the HTTP proxy server’s ruleset to your specific needs. Companies can configure the ruleset for a variety of purposes, which will be discussed shortly.
How are HTTP Proxies Utilized?
HTTP proxy servers adhere to the same operational principle as other proxy servers. In this regard, in order to comprehend what an HTTP proxy is, we will define a proxy server.
A proxy/proxy server is an intermediary that all web traffic flows through. Web traffic refers to the web requests generated by a user’s computer and the content transmitted in response from the web server.
Typically, proxies modify web requests by concealing the original IP address and assigning a new IP address. As described below, certain proxies, such as HTTP proxies, change the content sent by web servers. What is an HTTP proxy then?
HTTP Proxy Brief Explanation
Configured on a computer or web browser, an HTTP proxy functions as a gateway. The IP address of the proxy is user-defined; if the user does not specify, the IP address defaults to a number assigned by the operating system. The HTTP proxy intercepts Hypertext Transfer Protocol (HTTP) communications and operates as follows:
You will type a webpage into your browser as the user. Upon pressing ‘Enter,’ a web browser generates a web request, which is separated into data packets and transmitted over the Transmission Control Protocol (TCP). The TCP data packets are not delivered to the web server directly. Instead, they reach the HTTP proxy, which conceals the original IP address by assigning its own IP address to the data packets before forwarding them to the destination website.
Even though HTTP proxies are not based on the HTTPS protocol, they can access HTTPS websites. Due to their usage of a two-way communication channel, they can access the Secure Sockets Layer (SSL).
A tunnel is created between the client (browser) and the web server by an HTTP proxy. After then, it establishes the connection on the client’s behalf, which increases anonymity because direct communication between the browser and web server is severed. In addition to supporting anonymity, HTTP proxies filter HTTP and HTTPS-sent material.
There are two HTTP proxy types, namely the HTTP-client proxy and the HTTP-server proxy. The former safeguards your computer or network at home or work by screening content; only authorized items can be downloaded. A HTTP-server proxy, on the other hand, permits the majority of HTTP connections sent by clients to reach the server, but prevents malicious attempts to upload or delete files to or from the webserver.
Utilizations of HTTP Proxies
HTTP proxies serve the following functions:
To make a connection anonymous by concealing its real IP address For filtering information received via HTTP or HTTPS to enhance safety.
1. Anonymize connections
As stated previously, an HTTP proxy conceals the real IP address. It differs from other proxies in that the user selects the IP address to be used by the proxy. The anonymity provided by HTTP proxies means a website cannot determine the client’s true IP address.
2. Filter content
Both HTTP-client and HTTP-server proxies filter the content that reaches them. They prohibit the storage of unauthorized files on the server or user’s PC. Thus, they defend against potential malware, spyware, and ransomware attacks.
3. Enhance safety
The HTTP proxy can be configured to inspect the HTTP and HTTPS headers to determine the origin of the content. This procedure ensures that websites known to contain malicious content are denied access, so protecting your computer. HTTP proxies serve as a firewall in this aspect. Notably, a header is a part of a data packet that carries information about the material being transmitted (its properties), the source website, and the file’s size.
In addition, HTTP proxies enhance security by examining the protocol for irregularities. It is governed by a set of rules, i.e., requests for comments (RFC) standards, which define what is typical. A web server, for instance, is intended to take requests and not send them. Therefore, when it initiates communication sessions with a host, this behaviour is anomalous. Similarly, an extra-long header is an abnormality, therefore an HTTP proxy would block any request or content with such a header.
HTTP proxies provide multiple functions, including increasing security, screening files and content, and anonymizing a connection. Following a few instructions will allow you to configure your browser or machine as an HTTP proxy.
HTTP Proxy Advantages and Limits
Advantages of HTTP Proxy
As previously stated, you can configure the HTTP proxy server’s rules to achieve your objectives. Depending on the settings, an HTTP proxy can assist you with:
-
Security – Protocol anomaly detection rules can be configured to identify and deny suspicious packets, protecting your web server from external network attacks.
-
Privacy – For various security reasons, some people choose to use a proxy to hide their true IP address. An HTTP proxy, like a regular proxy, can mask your IP address.
-
Content restrictions – Businesses can limit the content that enters their network. The HTTP proxy can be configured to limit content based on the domain or path name, file name, or an extension in the URL.
-
Bypass target website restrictions – This is especially important for web scraping and web crawling. HTTP proxies are used to generate HTTP request headers that include information about the browser making the request. If you want to learn more, we’ve identified the top five HTTP headers for web scraping.
Limitations
However, data caching might result in information misuse, especially if the cache is compromised, as it retains users’ data and login passwords. Other HTTP proxy usage restrictions include:
Possible compatibility and configuration problems with regional networks
Setup and maintenance expenses for the proxy server
Conclusion
An HTTP proxy server can help your business in a variety of ways, including protecting your network from external attacks, shielding your IP address, restricting unwanted content, and assisting you with web scraping projects.
We have a blog post that can help you decide whether SOCKS5 proxies are secure enough for your business needs if you want to learn about other types of proxies or compare SOCKS proxy vs. HTTP proxy.
ad



Comments are closed.