What is Fileless Malware?
Fileless malware is a type of malicious software that exploits legitimate programs to infect computers. It operates without relying on files, making it difficult to detect and remove since it leaves no trace. Cyber adversaries are well-aware of organizations’ defense strategies and are developing increasingly sophisticated, targeted malware to evade them. This creates a race against time, with the newest hacking techniques proving to be the most effective. Fileless malware has been successful in evading all but the most advanced security solutions.
Although fileless malware became mainstream in 2017, many of its attack methods have existed for some time. Early examples of such malware include Frodo, Number of the Beast, and The Dark Avenger. Recent high-profile fileless attacks include the Democratic National Committee hack and the Equifax breach.
ad
What makes fileless infections so dangerous is their effectiveness in remaining undetected. Claims that fileless malware is “undetectable” are not entirely accurate; they mean that fileless attacks often go unnoticed by traditional endpoint security solutions like antivirus and whitelisting. The Ponemon Institute suggests that fileless attacks are ten times more likely to succeed than file-based attacks.

How Does a Fileless Attack Happen?
Fileless attacks, falling under the broader category of low-observable characteristics (LOC) attacks, operate stealthily to avoid detection by most security solutions and hinder forensic analysis. While not conventional viruses, fileless malware functions similarly by operating in computer memory rather than relying on files or direct installation on a machine. Many of these attacks exploit Microsoft Windows PowerShell, a legitimate tool used for administration tasks, allowing adversaries extensive access within the Windows environment.
ad
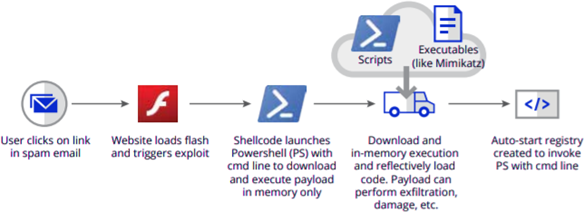
The diagram provided illustrates the process of a fileless attack, typically initiated through social engineering tactics like phishing emails. Such attacks aim for lateral movement within the network, seeking access to valuable data. To remain undetected, fileless malware embeds itself within trusted applications or the operating system itself, exploiting security systems’ trust models.
Crucially, fileless attacks bypass traditional antivirus and malware defenses by executing commands through the command line, a method often unnoticed by automated sensors. While these scripts could be identified by a trained analyst, pinpointing them for investigation remains a challenge.
Types of Fileless Malware Attacks
Fileless malware attacks typically fall into two main categories: memory code injection and Windows registry manipulation.
Memory Code Injection
Involves concealing malicious code within the memory of legitimate applications, often critical to essential processes. Exploiting vulnerabilities in programs like Flash and Java, or through browsers, attackers gain access to a system, executing code within authorized processes. Phishing campaigns are also common methods for initial access.
Windows Registry Manipulation
Entails using a malicious link or file to exploit a trusted Windows process. Upon interaction, such as clicking a link, the attacker leverages the Windows process to write and execute fileless code directly into the registry.
Both methods enable fileless malware to evade traditional detection tools like antivirus software, as they operate within authorized processes or manipulate trusted system components rather than relying on malicious applications.
Top 5 Fileless Malware Attacks
Fileless malware is gaining traction primarily because it can bypass traditional antivirus technology, enabling attackers to propagate it more efficiently, catching conventional cybersecurity measures off guard.
The top five fileless malware attacks include:
- Frodo
- Number of the Beast
- The Dark Avenger
- Poweliks
- Duqu 2.0
How Can You Defend against Fileless Attacks?
As cybersecurity measures advance to close off vulnerabilities, the window of opportunity for fileless attacks diminishes. One effective defense against fileless infections is maintaining up-to-date software, particularly Microsoft applications, which now offer enhanced security features through the Microsoft 365 suite. Additionally, Microsoft has bolstered its Windows Defender package to detect anomalous activity originating from PowerShell.
However, the key to effectively thwarting fileless attacks lies in adopting an integrated strategy that covers the entire threat lifecycle. By implementing a multi-layered defense approach, organizations can gain an upper hand against attackers by thoroughly investigating each stage of an attack—preparation, execution, and aftermath.
Two crucial components of this strategy include:
- Comprehensive visibility and monitoring: This involves identifying attack techniques, monitoring activities within scripting engines like PowerShell, aggregating threat data, and observing user behaviors.
- Active system control: This entails the ability to halt unauthorized processes, remediate compromised processes, and isolate infected devices.
Successfully mitigating fileless attacks demands a holistic approach that can adapt and respond swiftly with appropriate actions as needed.
How to Protect against Specific Types of Fileless Threats?
Reflective Self-Injection
Reflective loading involves loading a portable executable (PE) directly from memory instead of from disk. A specially crafted function or script can achieve reflective loading of a PE without registering it as a loaded module in the process, allowing actions to be performed without leaving traces. PowerShell is commonly used to execute these crafted scripts. This event signifies a fileless attack where a PowerShell script attempts to inject a PE into the PowerShell process itself.
Reflective EXE Self-Injection
Reflective loading entails loading a PE directly from memory rather than from disk. A crafted function or script can reflectively load an executable (EXE) without registering it as a loaded module in the process, enabling actions to be performed stealthily. PowerShell is frequently utilized for executing such crafted scripts. This event indicates a fileless attack where a PowerShell script tries to inject an EXE into the PowerShell process itself.
Reflective DLL Remote Injection
Reflective loading involves loading a PE directly from memory instead of from disk. A crafted function or script can reflectively load a DLL without registering it as a loaded module in the process, allowing actions to be executed covertly. PowerShell is commonly used for executing these crafted scripts. This event suggests a fileless attack where a PowerShell script attempts to inject a DLL into a remote process.
Malicious Code Execution Using DotNetToJScript Technique
This event indicates an attempt to execute malicious shellcode using the DotNetToJScript technique, which is utilized by prevalent fileless attacks like CACTUSTORCH. DotNetToJScript attack vectors enable loading and execution of malicious .NET assemblies (DLL, EXE, etc.) directly from memory using .NET libraries exposed via COM. Similar to other fileless attack techniques, DotNetToJScript does not write any part of the malicious .NET DLL or EXE to the computer’s hard drive.
FAQ’s
How does fileless malware differ from traditional malware?
Fileless malware operates without relying on files, making it difficult to detect and remove since it leaves no trace on the hard drive. Traditional malware, on the other hand, typically involves the creation and execution of files on the system.
Why are fileless attacks particularly dangerous?
Fileless attacks are dangerous because they can evade traditional detection methods such as antivirus software by operating directly in computer memory. This makes them difficult to detect and remove, allowing attackers to remain undetected while carrying out malicious activities.
What are some examples of fileless malware attacks?
Some examples of fileless malware attacks include Frodo, Number of the Beast, The Dark Avenger, Poweliks, and Duqu 2.0. These attacks have been successful in evading traditional security measures and have caused significant damage to organizations.
How can organizations defend against fileless attacks?
Organizations can defend against fileless attacks by maintaining up-to-date software, particularly Microsoft applications, which often serve as targets for these attacks. Additionally, implementing a multi-layered defense approach that includes comprehensive visibility and monitoring, as well as active system control, can help detect and mitigate fileless attacks effectively.
What is reflective loading, and how is it used in fileless attacks?
Reflective loading involves loading a portable executable (PE) directly from memory instead of from disk. In fileless attacks, attackers use reflective loading to inject malicious code into legitimate processes without leaving traces on the hard drive, making detection more challenging for traditional security measures.
What is the DotNetToJScript technique, and how is it used in fileless attacks?
The DotNetToJScript technique is used in fileless attacks to execute malicious .NET assemblies (DLL, EXE, etc.) directly from memory using .NET libraries exposed via COM. This technique allows attackers to execute malicious code without writing any part of the code to the computer’s hard drive, making detection more difficult for traditional security measures.
Conclusion
Fileless malware presents a formidable challenge to cybersecurity, as it evades traditional detection methods and operates stealthily in computer memory. To defend against such threats, organizations must prioritize software updates, deploy comprehensive monitoring tools, and exercise proactive system control measures. By adopting a holistic approach to cybersecurity and remaining vigilant against emerging attack techniques, organizations can effectively mitigate the risks posed by fileless malware.
ad


Comments are closed.