Remote code execution-RCE: What is RCE Attack and how to prevent it
A dangerous computer vulnerability. It lets an attacker remotely launch malicious code on a local network or the Internet. Physical access isn't needed. An RCE vulnerability can lead to system control loss and sensitive data theft.
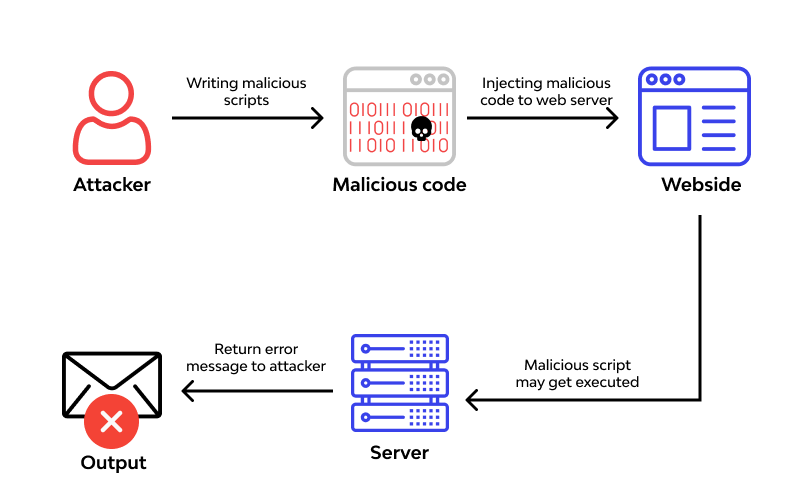
Remote code execution is always done by a tool that runs on its own. Trying to run code from a distance by hand would be, at best, nearly impossible. Most of the time, these attacks are written into an automated script.
One type of security flaw that can affect web applications is know as remote code execution, and it is quite common. On a server that is susceptible to this kind of vulnerability, an attacker has the ability to run any code they want with the privileges of the system if the server possesses the appropriate flaw. After the server has been compromised to a sufficient degree, an attacker may be able to access any and all information stored on it, including databases that contain information that clients who are unaware of the attack have provided.
ad
In this article I will explain everything in detailed info about RCE, vulnerabilities and how to detect and prevent it.
What is RCE (Remote Code Execution)?
When a user’s input is injected into a file or string, and then the complete package is executed on the parser of the programming language, a technique known as remote code execution can be utilized to reveal a type of vulnerability that is susceptible to being exploited. The individual responsible for the development of the web application does not demonstrate conduct like this in any way. It is possible for a Remote Code Execution Attack to progress into a full-scale attack, which would compromise not just the web application but also the webserver. RCE could potentially lead to the escalation of privileges, the pivoting of the network, and the establishment of persistent access. Because of this, the severity of RCE is always considered HIGH or CRITICAL. You should also take into consideration the fact that practically all programming languages come with a variety of utilities for evaluating code.
When you let user inputs to obtain access to functions that are evaluating code in the same programming language, you increase the likelihood that a code evaluation will take place. Either on purpose or unintentionally, the developer may place user-controlled input inside one or more of the mathematical functions of the programming language. This type of security measure can be implemented for the purpose of gaining access to the mathematical functions of the programming language. This course of action should not be pursued since it is not prudent. The very act of using code evaluation is seen as malevolent by a lot of people.
ad
Why do attackers launch RCE attacks?
RCE vulnerabilities can be exploited by attackers since they provide a purpose. Finding a remote code execution vulnerability (RCE) is extremely important to the organization if the engagement is a penetration test because it can lead to a wide variety of other security issues or vulnerabilities. If the company is under attack by a hacker with a black hat, and the hacker is successful in locating and exploiting RCE, then the company faces a significant threat of losing both its integrity and its confidentiality. The use of RCE as a vector for exploiting vulnerabilities is among the worst possible outcomes for a business. Therefore, even in isolated environments, RCE vulnerabilities are regarded as “CRITICAL” 99% of the time. This is due to the fact that once an attacker is inside the system, they can escape and attack the internal networks regardless of whether the system is isolated or not.
How Does RCE Attack Work?
Most of the well-known RCE vulnerabilities are caused by a few basic problems that can be traced back to the beginning. The following looks at how Remote Code Execution is grouped by where it starts.
Dynamic Code Execution
Dynamic Code Execution is by far the most common basic reason why a code execution attack happens. Many programming languages are set up so that they can take code from another language and run it right away. This idea is great because it takes care of a lot of hard problems. Still, an attacker with bad intentions can use this idea to gain RCE access and capabilities.
Usually, how quickly code is made depends on what the client gives. Usually, the code has the information that was remembered about a certain structure. When a bad guy knows that a powerful code age will use certain information, he or she could make a large code as a way to get into the application and break it. If the clients’ contributions aren’t looked at, the code will be run on its goal.
When you take the time to look closely, you can see that dynamic code execution is behind two types of RCE-based attacks: direct and indirect.
- Direct
When dealing with a direct unique tribute execution example, the attacker knows that their feedback will be used to make code. - Indirect
In an odd way, it’s worried about the powerful code age with client inputs. Most of the time, at least one layer is added to the input from the client. A portion of the layers might be answerable for changing the contribution before it winds up with dynamic code age. Also, dynamic code age might be a later effect and not how the information is used right away. That is the reason it may not be clear to the client that is giving the info that will fill in as a structure block in a code scrap that would be executed distantly. - Deserialization
Deserialization is a great way to describe how things are right now. During deserialization, no powerful code changes should happen. This happens sometimes when the serialised object contains simple information fields or other objects of a similar type. When the parts of the article are put in order, it makes things more confusing. Deserialization would also use dynamic code execution to some degree.
It might seem like only strong dialects are affected by how works are put together. Assuming this is true, the question would be very narrow. Even so, this situation is also very useful in static dialects. With the static language, it’s harder to do, but it’s still not possible.
When this idea is put into action, it sometimes has to deal with the intermediary capacities that come from de-serialization. With dynamic code age, it is possible to age objects at runtime. This implies that if the information that will be deserialized is made in a solicitation made distantly, a malevolent assailant could commandeer and adjust it. When it’s part of the deserialization process, well-written code bits could also be used to shorten the time it takes for the powerful code to do its job.
Memory Safety
Another simple reason for RCE attacks has to do with memory or API security. Memory health has to do with keeping code from accessing important parts of memory that it didn’t set up. It’s normal to think that if memory security isn’t good, information could be accessed by people who shouldn’t be able to. In any case, the working framework and equipment depend on memory to store executable code. In the memory, information about how code is run is kept. Accessing this piece of the memory could prompt ACE and RCE. In this way, what are a portion of the reasons for memory wellbeing issues?
- The imperfections of the product’s plan
Imperfections in the product configuration are a type of memory wellbeing weakness that happen when a planning mistake is made in a certain hidden part. Sometimes, the missing piece is a compiler, a translator, a virtual machine, or even a working part of the framework or a library. There are a number of flaws in this class. A small part of the whole. - Buffer Overflow
The term “buffer overflow” can be used to describe a simple and well-known way to break memory security. This assault takes advantage of a specific plan blemish or a bug to keep in touch with the memory cells that are situated toward the finish of the memory cushion. The support would get gotten back from an authentic call to public API. But “cradle” only means a starting point. A “threat” is used to record the actual memory locations of an article or program counter. Their separation from the cradle is notable or can undoubtedly be speculated. An attacker who wants to figure out relative positions might find it helpful to look at the code when it is made available or to troubleshoot the whole program while it is running.
This means that a cradle flood would make it possible to change the partially unavailable memory. The cradle might be found in the location space of one more machine and it will be changed by calling a distant API. This will make admittance to the memory of the remote machine. There are many ways to make an RCE double-dealing with this kind of access. There is a general feeling that an RCE-based attack is possible, if there is a cushion flood weakness. This means that code owners are expected to fix their support floods as soon as possible, before an RCE attack happens.
- Equipment Design Flaws
Memory health attacks can also be caused by mistakes in how the equipment is made. They don’t happen as often as programming attacks and are harder to spot. But this kind of attack has a big effect on the structure.
Examples of RCE vulnerabilities
RCE could sometimes lead to major disaster, and the world has seen this happen quite a few times. Here are five recent examples of how cybercriminals could use an RCE loophole to take advantage of the victim sites or end users.
ETERNALBLUE
WannaCry was the first big ransomware attack in 2017. The WannaCry virus spread by taking advantage of a weakness in the Server Message Block Protocol (SMB). This flaw made it possible for an attacker to run malicious code on machines that were vulnerable. This allowed ransomware to access and encrypt important files.
Log4j
Log4j is a popular Java logging library that is used by many services and programs on the Internet. In December 2021, multiple Remote Code Execution (RCE) vulnerabilities were found in Log4j. These vulnerabilities let attackers use vulnerable applications to run cryptojackers and other malware on servers that had been compromised.
CVE-2021-44228
The problem, which was found in Log4J Shell, set off a chain of events. What this means is that the 44228 hole led to the discovery of two new holes, 45105 and 45046. The problem stayed with Apache and spread to different versions of Log4j. Since log4j is a Java Library, it was used in millions of applications, so the vulnerability got to them too.
Using this hole, threat actors were able to run their code remotely without having to log in first. The malicious code only needed to make a fake LDAP server for things to work. The process of taking advantage of it was easy and quick, so many people did it, and the top web services in the world were hurt.
CVE-2021-1844
This bug in Apple’s operating systems affected a wide range of Apple devices and users all over the world. With the help of a URL that was controlled from the outside, cybercriminals were able to run malicious payloads on any device that had been compromised. All major Apple operating systems were affected, including iOS, macOS, Safari, and watchOS.
CVE-2020-17051
This problem happened on MS Windows and was caused by a flaw in NFS version 3, which is a version of a communication protocol we all know. By taking advantage of this flaw, attackers could use a compromised NFS server connection to send a payload to an unsecured endpoint and run it however they wanted.
CVE-2019-8942
The security flaw had a big effect on WordPress and made it different from how it used to be. In 2019, the number 8942 was found in WordPress 5.0.0. Hackers could use it to add malicious code to the WordPress directory of the target site by using an image with PHP code in its Exif meta-data. They could then run the code and change the victim site.
CVE-2018-8248
With the well-known Microsoft Excel RCE loophole, bad guys could get the compromised computer to run malware. Attackers could not only take full control of the device they were after, but they could also take away the user’s admin rights. So, hackers could change, add, remove, or move data or applications in any way they wanted by taking advantage of this vulnerability.
The Impact of a Vulnerability That Caused By Remote Code Execution
RCE attacks are developed with the intention of accomplishing a wide variety of objectives. The primary distinction that can be made between RCE and any other exploit is that it can involve any combination of information leak, denial of service, and the execution of remote code.
Among the most significant effects of an RCE attack are the following:
- Initial Access: Most RCE attacks start with a flaw in a public-facing application that lets the attacker run commands on the machine underneath. This lets attackers get a foothold on a device so they can install malware or reach other goals.
- Information leakage: RCE attacks can be used to install malware that steals data or to directly run commands that take data from a vulnerable device and send it somewhere else.
- Denial of service: An RCE vulnerability lets an attacker run code on the system where the vulnerable application is running. This could give them a way to mess up the way this or other programmes on the system work.
- Cryptomining: Malware called cryptomining or cryptojacking uses the computer power of a device that has been compromised to mine cryptocurrency. RCE vulnerabilities are often used to install and run cryptomining malware on devices that are vulnerable.
- Ransomware: It is a type of malware that locks a user out of their files until they pay a fee to get back in. A device with an RCE vulnerability can also be used to install and run ransomware.
Even though these are some of the most common effects of RCE vulnerabilities, an RCE vulnerability can give an attacker full access to and control over a compromised device, making it one of the most dangerous and important types of vulnerabilities.
Identifying And Easing an RCE Attack
RCE attacks can take use of a wide variety of vulnerabilities, which makes it challenging to defend against them using a singular strategy. The following are some examples of best practices for identifying and preventing RCE attacks:
Input Sanitization: Use a “zero-trust” strategy and always clean user input before using it. Whitelists, blacklists, and escape sanitization are all parts of a thorough process of sanitization. This will help stop many attempts to inject code or change the way data is stored. Also, network segmentation can help keep any code that does get through from doing too much damage.
Also, if you can, don’t use functions that evaluate code and don’t let users change content that has already been parsed.
Security Updates: Organizations often don’t act on the latest information about threats or apply patches and updates when they should. Because of this, attackers will usually also try to take advantage of old holes. Keeping your system and software up-to-date with security patches as soon as they become available is a great way to stop many attackers.
Memory Management: RCE attackers can also take advantage of memory management flaws, such as buffer overflows. Secure Memory Management Applications need to go through a process called vulnerability scanning in order to discover buffer overflow and other vulnerabilities. This will allow these mistakes to be found and fixed.
Traffic Monitoring: RCE attacks, as their name suggests, take place over the network. An attacker takes advantage of insecure code and uses it to get initial access to corporate systems. Traffic Inspection RCE attacks take place over the network. An company ought to implement network security solutions that are able to prevent the attempted exploitation of susceptible applications and that are able to detect an attacker’s takeover of remote control of corporate systems.
Access Control: An RCE attack gives an attacker a foothold on the enterprise network, which they may then expand on to accomplish their ultimate goals. This is accomplished through the use of RCE backdoors. An organization can limit an attacker’s ability to move around the network and take advantage of their initial access to corporate systems by implementing network segmentation, access management, and a zero trust security policy. These are the three components of a zero trust security strategy.
Firewalls can detect and prevent attempts to exploit RCE vulnerabilities via injection or buffer overflow attacks because these types of assaults are detectable. Putting apps in a secure location behind a firewall helps to cut the danger that applications pose to the organization to a great extent.
RCE – Video Presentation
FAQ
What is a remote code execution vulnerability?
When web applications have Remote Code Execution (RCE) vulnerabilities, an attacker can run any code on the web server that hosts the web application. Log4Shell, an RCE flaw in Apache Log4j, is a good example of remote code execution.
How dangerous is an RCE vulnerability?
If an attacker is able to execute an RCE vulnerability in a web application, they can run any code and send commands to the web server. For example, the attacker can use an RCE flaw to install a web shell on the web server and continue the attack from there.
How to detect remote code execution vulnerabilities?
Dynamic application security testing (DAST) tools are the best way to detect remote code execution vulnerabilities in web applications. They offer the best protection, and some of them can prove that the vulnerability is real and not a false positive.
ad


Comments are closed.