What is Hash-based Message Authentication Code (HMAC)?
Ensuring the security of data and information exchanged over the internet is paramount in the development of apps and web platforms.
A crucial method for verifying integrity is through hash-based message authentication codes (HMAC), which employ a cryptographic process involving a message, a secret key, and a hash function.
The primary objective of HMAC is to safeguard data integrity, preventing unauthorized alterations. If any tampering occurs, HMAC facilitates the detection of such changes efficiently.
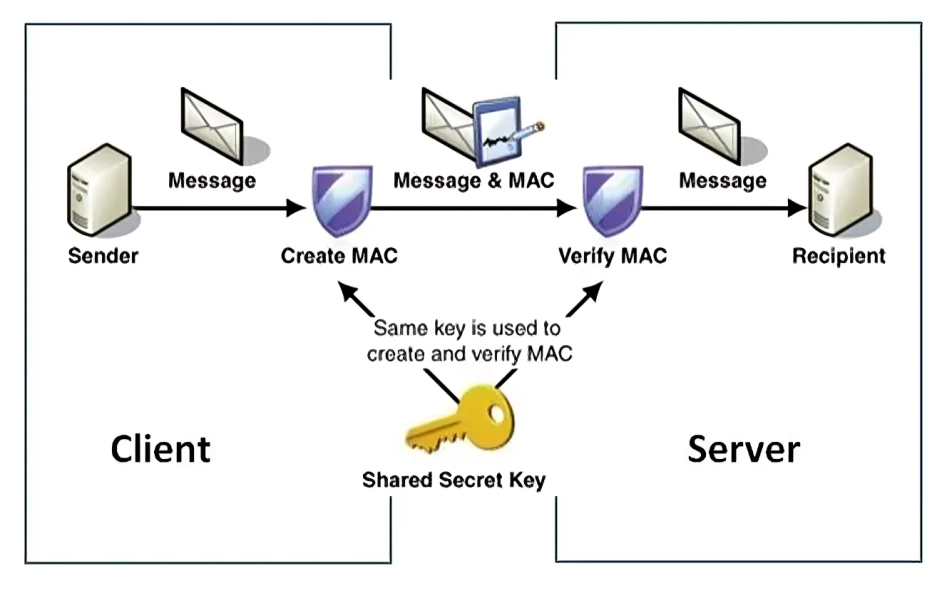
How HMAC works
ad
HMAC, a message-based authentication code, employs a hash function alongside a cryptographic key. This key, unique to both server and client, is provided by HMAC.
The functionality of HMAC relies on three key components:
- The message: This constitutes the data subject to authentication or verification, ensuring its secure storage and transmission.
- Secret keys: These keys are exclusive to authorized parties, used in generating the HMAC value.
- Cryptographic hash function: Through hashing, input data (message and key) transforms into a distinct output (HMAC value). This process is pivotal for maintaining message integrity, as HMAC values cannot be reversed to reveal the original message or key.
HMAC operates as a symmetric key algorithm, utilizing the same secret key for both HMAC value creation and verification.
The goals of HMAC
HMAC ensures the integrity and security of messages, shielding them from external interference.
During transmission, there’s a risk of unauthorized parties intercepting and corrupting data, often with the aim of breaching secure platforms. HMAC mitigates this risk by hashing messages and combining them with secret keys.
Upon reception, the recipient can verify the message’s accuracy by employing the same secret key to digest and authenticate it. By recalculating the hash using the identical secret key, the recipient can detect any alterations introduced by attackers.
A matching hash and transmitted HMAC value indicate the message’s integrity remained intact during transmission. However, a mismatch signals a problem—whether due to transmission errors or malicious interception by hackers.
This capability helps thwart hackers from infiltrating secure systems, as recipients can reject tampered messages identified during transmission.
Why HMAC is important
Protecting your data from interference is paramount, and being able to easily detect any tampering is equally important. The HMAC process ensures data security and integrity, safeguarding it against attacks.
Upon completion of the HMAC process, the message undergoes permanent hashing, ensuring it can only be accessed and decrypted with the correct secret key. This process effectively reduces the risk of security breaches, including message tampering, replay attacks, and man-in-the-middle attacks.
Key benefits of incorporating HMAC into your app development efforts include:
- Ensuring secure communications: By utilizing HMAC to authenticate messages, you can trust that your apps and services exchange data securely. This approach significantly reduces the likelihood of sensitive data interception.
- Enhancing compliance: Compliance with standards such as GDPR can be simplified by employing cryptographic algorithms like HMAC. This ensures that your app interacts only with trusted services, facilitating compliance efforts.
- Seamless integration: HMAC, being a widely adopted algorithm, is supported across various programming languages and can seamlessly integrate into your existing workflows, simplifying the integration process.
The drawbacks of HMAC
While HMAC is effective in preserving data integrity, it’s not exempt from drawbacks and limitations.
A significant limitation is its dependence on a secret key. If this key falls into unauthorized hands, message integrity could be compromised. Therefore, it’s crucial to implement robust processes for securely storing and managing secret keys.
Moreover, HMAC has limitations in its ability to counter certain types of attacks. While it provides some defense against replay attacks, it doesn’t entirely prevent them. In scenarios like denial-of-service attacks, social engineering attacks, and side-channel attacks, HMAC’s capability is limited to detecting message tampering. Consequently, it’s advisable to complement HMAC with additional protections and protocols to ensure comprehensive app security.
Implementing HMAC
Implementing HMAC involves three main steps:
- Selecting a hash function (such as SHA-256 or SHA-512) to compute the message.
- Generating a randomly chosen secret key, the length of which depends on the required level of platform security.
- Combining the message and secret key using the chosen hash function to produce an HMAC value.
This HMAC value is transmitted and verified using the same hash function. A match between the transmitted and verified values indicates message authenticity, while a mismatch signals tampering.
In essence, HMAC serves as a robust security layer for companies handling sensitive data. It acts as a vital safeguard against attackers, offering a clear indication of data compromise.
FAQ’s
What is HMAC and why is it important in app development?
HMAC, or hash-based message authentication code, plays a crucial role in ensuring the security and integrity of data exchanged over the internet. It employs cryptographic techniques to verify the authenticity of messages, protecting them from unauthorized alterations.
How does HMAC work to safeguard data integrity?
HMAC works by combining a message with a secret key using a hash function, generating a unique HMAC value. This value is transmitted alongside the message and can be used to verify its integrity upon reception. If the HMAC value matches the recalculated hash, the message remains unaltered.
What are the benefits of using HMAC in app development?
Incorporating HMAC into app development offers several advantages. It ensures secure communication by authenticating messages, enhances compliance with regulations like GDPR, and facilitates seamless integration into existing workflows.
What are the limitations of HMAC?
While HMAC is effective in preserving data integrity, it relies on a secret key, making it vulnerable if the key is compromised. Additionally, HMAC has limitations in countering certain types of attacks, such as denial-of-service and social engineering attacks.
How can HMAC be implemented in app development?
Implementing HMAC involves selecting a hash function, generating a secret key, and combining them with the message to create an HMAC value. This value is then transmitted and verified using the same hash function, ensuring message authenticity.
What measures can be taken to mitigate the drawbacks of HMAC?
To mitigate the drawbacks of HMAC, it’s essential to implement robust processes for securely storing and managing secret keys. Additionally, complementing HMAC with additional security protocols can help address its limitations in countering certain types of attacks.
Conclusion
HMAC stands as a crucial tool for securing data integrity in app and web development. Despite its reliance on secret keys and limitations, it plays a vital role in protecting data from unauthorized alterations. By ensuring secure communication and facilitating compliance, HMAC offers a robust defense against breaches. With careful implementation and augmentation with additional security measures, organizations can leverage HMAC to fortify their digital ecosystems and safeguard sensitive information effectively.
ad


Comments are closed.