What Is a Fast Flux Network?
The idea behind a fast-flux network is to enable botnets to rapidly switch from one Internet Protocol (IP) address to another, utilizing compromised hosts to facilitate this movement.
What is fast flux in cybersecurity? Fast-flux networks involve botnets changing IP addresses frequently, sometimes every few minutes. This constant switching, using compromised hosts as proxies, allows cybercriminals to conduct activities like phishing, malware distribution, and other attacks without easily being detected.
ad
Another term for a fast-flux network is a “flux domain.” This technique involves cybercriminals using botnets to rotate IP addresses while concealing a legitimate domain name behind the scenes.
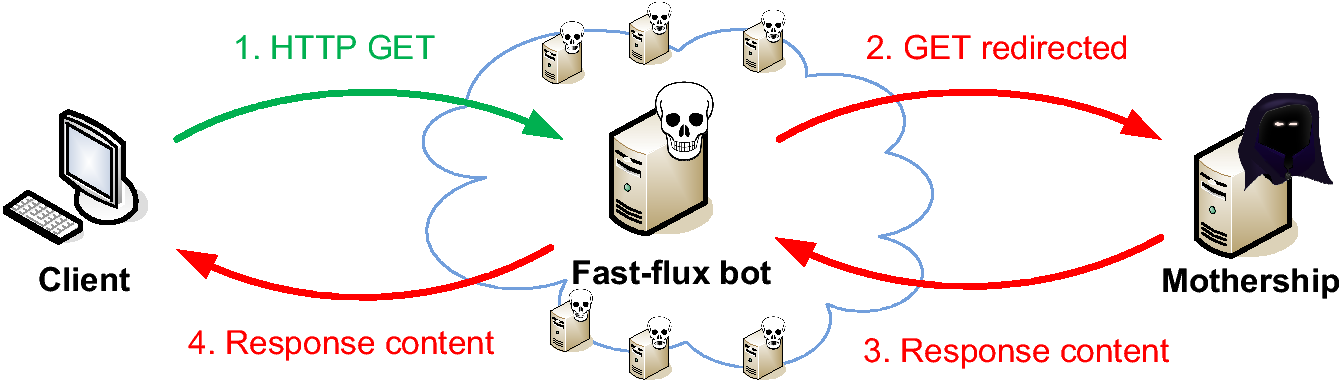
How Does Fast Flux Work?
Fast-flux networks are like shell games, constantly shuffling a deck of IP addresses that all point to the same deceptive domain name.
ad
These domains are often clever imitations of legitimate sites, like banks or retailers. Attackers create these “typosquats” by slightly misspelling the real domain name, hoping to trick users into visiting. Unsuspecting users might land on a cleverly designed phishing site hosted by the attackers, unknowingly giving away their credentials or other sensitive information.
While the fake website itself stays the same, the IP address behind it is constantly on the move. Botnets, armies of compromised computers, rapidly switch between various IP addresses linked to the malicious domain. Each address is only active for a short time before being replaced by another, making it difficult to pinpoint the source and take down the operation.
Types of Fast-Flux Networks
Fast-flux networks come in two main varieties: single-flux and double-flux. While the criminal’s overall goal remains the same (tricking you!), the technical details differ.
Single-Flux Shuffle
Imagine a deck of cards, each card an IP address. In a single-flux network, many compromised computers (nodes) constantly shuffle this deck. Each node registers its IP with the Domain Name System (DNS) for the malicious domain. But just like a card game with a short attention span, these IPs only last 3-5 minutes before being swapped out for fresh ones. This rapid rotation makes it hard to pinpoint the source and shut down the operation. Think of it as whack-a-mole for authorities – whack one IP, another pops up.
The malicious domain itself often resides on a heavily fortified server, making direct takedown even trickier for the good guys.
Double-Flux Frenzy
Double-flux takes the single-flux approach and cranks it up to eleven. Here, not just the IP addresses, but also the DNS servers themselves are constantly changing. Imagine multiple decks of cards being shuffled simultaneously! This double layer of flux makes tracing the attack’s origin incredibly difficult, like chasing smoke in the wind.
Criminals often leverage “zombie computers” – compromised machines turned into remote-controlled puppets – in double-flux networks. These zombies act as an extra layer of obfuscation, further shielding the attacker’s true location. Think of it as a smoke bomb followed by a maze – authorities are left bewildered and disoriented.
How a Fast-Flux Network Can Be Used as a Platform for Malicious Activities
Fast-flux networks are a cybercriminal’s toolbox, enabling a variety of nasty attacks – and they’ve been around for over 15 years, causing trouble since 2007. Researchers from the Honeynet Project first identified this technique, and ever since, the race has been on to understand, detect, and ultimately prevent its havoc.
Here’s how fast-flux fuels cybercrime:
Malware Delivery Disguised
Imagine a fast-flux network as a shell game, constantly shuffling IP addresses. Hackers use this to hide malicious “droppers” – programs designed to bypass antivirus and install malware on unsuspecting users’ devices. When you connect to a fast-flux domain, you might unknowingly download malware disguised as a legitimate program.
Command and Conquer
Fast-flux networks often work hand-in-hand with a command-and-control (C2) server. This server acts as the hacker’s headquarters, issuing commands to compromised devices and collecting stolen data. The rotating IP addresses and domain make it hard to track the C2 server, allowing the attacker to maintain control and siphon information from infected machines.
Fast-Flux Detection and Monitoring Techniques
While prevention is always ideal, avoiding every compromised domain online can be a challenge. Here’s how organizations can fight back against fast-flux networks:
Focus on Defense, Not Just Detection:
The best defense is a good offense… well, a good defense! Since fast-flux networks are notoriously slippery, prioritizing measures to prevent users from reaching compromised domains in the first place is crucial.
Unmasking the Deception:
Fast-flux thrives on its ability to mislead investigators. The constant shifting of IP addresses and domains makes tracing the source a frustrating maze. Here’s how to break the illusion:
- Machine Learning (ML) to the Rescue: Machine learning algorithms can be trained to analyze network traffic and DNS patterns, spotting anomalies that might indicate a fast-flux network lurking beneath the surface.
- Mapping the Domain Landscape: By analyzing the geographic distribution of domain servers, security professionals can identify suspicious patterns. Rapidly changing server locations can be a red flag for a fast-flux network in action.
- Fast-Flux Monitors: Real-Time Guardians: Specialized tools can continuously monitor network activity and identify fast-flux and double-flux behavior in real-time. They analyze factors like network footprint, activity patterns, and time-to-live indexes to expose the hidden network manipulation.
By combining these techniques, organizations can significantly improve their ability to detect and ultimately thwart fast-flux attacks.
How to Stop Fast-Flux Attacks
Fast-flux networks exhibit a high degree of resilience, making them challenging to detect and dismantle once identified. Initially elusive, these networks often operate under a common domain name. While the domain name may be subject to takedown efforts, the network persists. However, without a functional domain, the network becomes inert.
The most effective strategy for organizations to thwart a fast-flux network is to pinpoint its domain name and initiate takedown procedures. By accomplishing this, the incessant rotation of IP addresses becomes inconsequential. With no accessible domain for users to connect to, the network loses its capacity to exploit individuals. Swift identification and removal of fast-flux domains are crucial steps in neutralizing the threat posed by fast-flux networks.
FAQ’s
What is the concept of fast flux in cybersecurity?
Fast-flux networks involve botnets rapidly changing IP addresses, sometimes every few minutes, to conduct various malicious activities like phishing and malware distribution while using compromised hosts as proxies to evade detection.
What is meant by a “flux domain” in the context of fast-flux networks?
A flux domain refers to the technique in which cybercriminals utilize botnets to rotate IP addresses while concealing a legitimate domain name, facilitating malicious activities while masking their operations.
How does fast flux work?
Fast-flux networks continuously shuffle IP addresses, akin to a shell game, all pointing to the same deceptive domain. Attackers create clever imitations of legitimate sites, directing unsuspecting users to phishing sites hosted on compromised hosts. While the fake website remains constant, the IP address behind it is constantly changing, making detection and shutdown challenging.
What are the types of fast-flux networks?
Fast-flux networks come in single-flux and double-flux varieties. In single-flux networks, compromised computers shuffle IP addresses, while in double-flux networks, both IP addresses and DNS servers constantly change, complicating detection efforts further.
What are some techniques for detecting and monitoring fast-flux networks?
Organizations can employ machine learning algorithms, analyze domain server distribution, and utilize specialized monitoring tools to detect fast-flux behavior in real-time, thereby enhancing their ability to identify and thwart such attacks.
How can organizations stop fast-flux attacks?
The most effective strategy for organizations is to identify and take down the domain associated with the fast-flux network. By doing so, the network loses its ability to exploit users, rendering the continuous rotation of IP addresses inconsequential and neutralizing the threat posed by fast-flux networks.
Conclusion
Fast-flux networks present a formidable challenge in cybersecurity, employing rapid IP address rotation to conduct malicious activities while evading detection. Despite their elusive nature, organizations can improve their defenses by employing advanced detection techniques and swiftly targeting associated domains. By disrupting the operational capabilities of these networks, cybersecurity resilience can be strengthened, mitigating their impact on users.
ad


Comments are closed.