A Guide to Email Authentication Protocols: SPF, DKIM, DMARC, and BIMI Explained
Email authentication is a technological method for preventing phishing and forgery. On the uncharted roads of email marketing, email authentication serves as both judge and executioner. Why do we require it? And how do you do it? This important guide will teach you more.
Email has become an essential part of our day-to-day lives, but it is also a common target for cybercriminals who use techniques such as email spoofing and phishing email attack to steal confidential information or spread malware. While email has become an integral part of our lives, it is also a common target for cybercriminals. Email authentication protocols have been developed to combat the risks posed by these threats.
These protocols verify the identity of the sender of an email and ensure that the email message has not been altered while it is being transmitted. SPF, DKIM, DMARC, and BIMI are the four email authentication protocols that are utilized the most frequently, and in this article, we will provide an in-depth introduction to each of these protocols. We will walk you through the process of protecting your email from being spoofed or compromised by explaining how each protocol functions, why it is essential, and how to implement it.
ad
What is email spoofing?
Cybercriminals use email spoofing to generate and send email messages with a false “From” address. In email spoofing, the attacker manipulates the email header to make the message appear to have been sent from a different email account than the one used to send the email.
Email spoofing can be used for various malicious purposes, such as phishing attacks, spreading malware, and stealing private information. A cybercriminal, for example, may send an email that appears to be from a legitimate bank or social media site, instructing the receiver to click on a link and enter their login credentials or personal information.
ad
Because the attacker can make the email look very similar to a genuine email, email spoofing can be difficult to detect. Email authentication methods such as SPF, DKIM, DMARC, and BIMI, on the other hand, can help prevent email spoofing by verifying the sender’s identity and ensuring that the email message was not tampered with during transmission.
| More: Top online frauds everyone should aware of
How Email Spoofing Works?
The aim of email spoofing is to fool users into thinking the email is from someone they know or can trust—usually a colleague, vendor, or brand. Using that confidence, the attacker requests information or other action from the recipient.
As an illustration of email spoofing, an attacker could send an email that appears to be from PayPal. The message informs the user that their account will be suspended if they do not select a link, log in to the site, and change their password. If the user is duped and enters credentials, the attacker now has the credentials to authenticate into the targeted user’s PayPal account, possibly stealing money from the user.
More sophisticated cyberattacks target financial workers and rely on social engineering and online reconnaissance to trick a targeted user into sending millions of dollars to an attacker’s bank account.
A spoofed email message appears genuine to the user, and many attackers will use elements from the official website to make the message more credible. Here’s an illustration of email spoofing with a PayPal phishing attack:
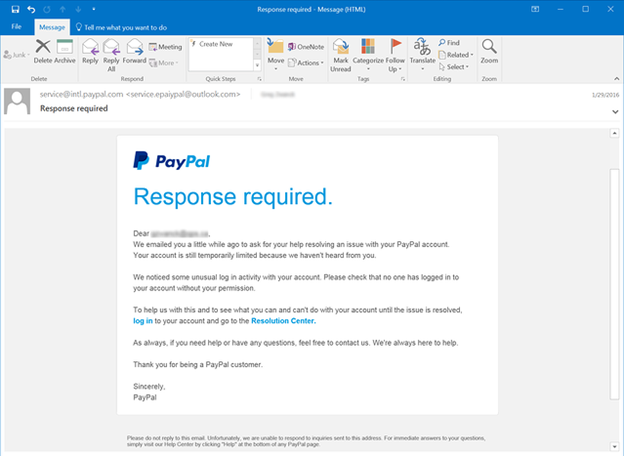
When a user sends a new email message using a standard email client (such as Microsoft Outlook), the sender’s address is immediately entered. However, an attacker can send messages programmatically using basic scripts in any language that configure the sender address to any email account of choice. Email API endpoints enable a sender to specify the sender address whether or not the address exists. Outgoing email servers can’t tell if the sender’s address is genuine.
The Simple Mail Transfer Protocol is used to receive and route incoming emails. (SMTP). When a user selects “Send” in an email client, the message is first routed to the client’s configured outgoing SMTP server. The SMTP server recognizes the target domain and forwards the message to the domain’s email server. The communication is then routed to the correct user’s inbox by the recipient’s email server.
The IP address of each server is logged and included in the email headers for each “hop” an email message makes as it travels across the internet from server to server. Although these headers reveal the true route and sender, many users fail to check them before engaging with an email sender.
An email’s three main components are:
- The sender’s email address
- The location of the recipient
- The email’s main text
The Reply-To box is another component that is frequently used in phishing. This field can also be configured by the sender and used in a phishing attempt. The Reply-To address instructs client email software where to send a response, which can vary from the sender’s address. Again, neither the email servers nor the SMTP protocol verifies whether this email is genuine or forged. It is the user’s responsibility to recognize that the response is being sent to the incorrect receiver.
| More: Types of servers and how they work
What is email authentication?
Email authentication is a procedure that verifies the sender’s identity and ensures that the email message was not tampered with during transmission. Email authentication protocols protect email users from getting spoofed or fraudulent emails that appear to be from a legitimate source but are actually sent by an unauthorized party. These protocols use various methods to validate emails, such as verifying the sending address, adding a digital signature to the email header, and encrypting and decrypting the message with cryptographic keys. Email users can be confident that the communications they receive are genuine and from a trusted source by employing email authentication protocols.
Why is email verification required?
There are several reasons why email authentication procedures must be followed:
From a brand point of view
Your business can use email authentication to:
Prevent From Email Spoofing
Email spoofing is a common tactic used by cybercriminals to impersonate a genuine sender and trick the recipient into revealing private information or clicking on a malicious link. Email authentication methods aid in the prevention of email spoofing by verifying the sender’s identity and ensuring that the email message was not tampered with during transmission.
Protect Your Brand Reputation
If your domain is used to send spam or fraudulent emails, it can harm your brand’s image and erode customer confidence. You can safeguard your brand image and customer trust by following email authentication protocols.
Enhance Email Deliverability
Email providers use email authentication methods to filter out spam and phishing emails, as well as to determine whether an email should be delivered to the recipient’s inbox or marked as spam. You can improve your email deliverability rates and ensure that your communications reach their intended recipients by following email authentication protocols.
Regulatory Compliance
Certain business regulations, such as HIPAA or GDPR, may require email authentication protocols to be followed. Noncompliance with these laws may result in legal consequences such as fines and legal liability.
Email authentication procedures must be followed to ensure the security and integrity of email communication, as well as to protect brand image, improve email deliverability, and maintain regulatory compliance. Email authentication has become a contemporary requirement. Cybercrime, like highway robbery, is a lucrative industry, and everyone is a target.
However, email authentication is more than just protection. These methods improve email deliverability by making them more trustworthy.
A triple-authenticated name is more likely to be delivered to inboxes and less likely to be routed to spam folders.
From a consumer point of view
Email authentication protocols are essential for the following reasons:
They help to minimize spam
According to Statista, approximately half of all emails sent are junk, and people despise it. Spam is by definition unwanted. Many customers embrace anything that keeps their inboxes from becoming clogged with useless, irrelevant, and annoying spam. Spammers, on the other hand, are known to be inventive. They’re often very good at making their emails appear – at least at first glance – to be the genuine, relevant material that people have signed up for.
Email authentication makes it much simpler to weed out spam and provide audiences with a much more fulfilling email experience by verifying that you exist, that you are who you say you are, and proving this to the client.
They make avoiding phishing simpler
Phishing and other forms of social engineering frequently depend on forged sender information. Email authentication protocols make such forgeries much more difficult to pass, and much simpler to detect if they do.
Authentication protocols provide a safer experience for customers and safeguard brands from the reputational damage connected with phishing scams.
What is the process of email authentication?
Email authentication entails a variety of methods for validating the origin of an email as well as the domain ownership of message transfer agents (MTAs) engaged in the transfer or modification of an email.
Simply put, emails are sent from a specific name or subdomain. Email authentication protocols are rules that can be found in the DNS (domain name system) entries for these sending domains. To authenticate an email, the sending and receiving mail servers communicate with one another, double-checking procedures in the DNS for confirmation.
While each protocol is different, it generally functions as follows:
- The sender/domain owner creates authentication criteria for emails sent from or on behalf of its domains.
- The sender configures the sending email servers and broadcasts the DNS records with the rules.
- Mail servers that receive emails use written guidelines to authenticate messages from the sender.
- The communication is then delivered, quarantined, or rejected by the receiving email server based on the published rules.
In addition to verifying legitimate senders, email authentication protocols aid in the establishment of IP addresses and domain reputations, allowing malicious senders to be recognized more easily.
Types of email authentication protocols
The Simple Mail Transfer Protocol (SMTP) is the standard foundation upon which email is constructed. It is what is used to transmit and receive messages. However, SMTP lacks a method for validating a sender’s identity, making it vulnerable to scammers and phishing.
Email authentication protocols arose in the early 2000s as a means to improve SMTP security and combat the rise of email spam. SPF and DKIM were the first commonly used methods. DMARC quickly followed as a strategy to confirm and extend SPF and DKIM.
BIMI results in a method for recipients to visibly verify the authenticity of an email by displaying a logo in the inbox. However, BIMI is the latest in the list of protocols that mainly helps with branding and is the payoff for having a solid email authentication strategy.
These four email authentication protocols provide a standardized way for email clients such as Gmail, Outlook, and Apple Mail to validate the identity of senders rather than using separate, proprietary methods to authenticate email.
So, while email authentication may appear complex, technical, and even a little messy… these protocols do provide some standardization. Email marketers should be grateful that we don’t have to follow different rules for each mailbox provider.
Let’s take a deeper look at SPF, DKIM, DMARC, and BIMI.
1. SPF Protocol (Sender Policy Framework)
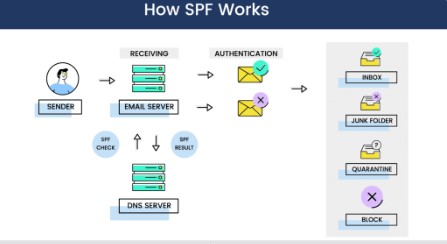
The Sender Policy Framework, or SPF, is an email authentication protocol that gives a DNS record that specifies which IP addresses or hostnames are authorized to send email from a domain.
SPF is a DNS TXT entry that allows the receiving mail server to verify that an email purporting to be from a specific domain is connected to an authorized IP address. The receiving server accomplishes this by consulting the DNS entry for the bounce or return-path domain. This is compared to the rules in the SPF record to guarantee a match.
An SPF protocol example
Let us now put our theories aside and look at a real record. If you looked up our domain, you would discover the following information:
download.zone. 14400 TXT v=spf1 include:_spf.google.com ~all
Without SPF, mailbox providers are much more likely to label messages as spam.
In some instances, email service providers (ESPs) manage SPF implementation automatically. Because the ESP may provide the IP address and the return route. However, if you transmit a lot of emails, you should probably avoid using a shared IP address. A dedicated IP address allows you to manage the sender’s reputation. Keep in mind that if you are using a shared IP address, your SPF record may need to be updated when you swap ESPs.
One disadvantage of SPF is that it will not function when emails are forwarded. If your brand is highly reliant on email word-of-mouth (getting your audience to forward your message), there’s a good chance the SPF will fail validation and never reach anyone beyond your list.
2. DKIM Protocol (DomainKeys Identified Mail)
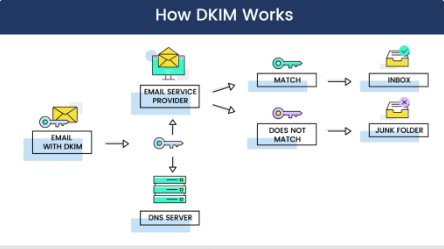
The DKIM email authentication protocol is the result of two methods created to prevent email forgery. In 2004, Yahoo combined its “DomainKeys” with Cisco’s “Identified Internet Mail.”
DomainKeys Identified Mail, or DKIM, employs an encrypted secret known as a digital signature. This signature is added to email headers to help verify the sender and associate communication with a particular domain. DKIM must also be configured within the sender’s DNS entry.
Consider DKIM to be a watermark or fingerprint that is distinctive to an email sender. Unlike SPF, DKIM signatures continue to function when an email is copied.
DKIM is powered by two credentials. Administrators create a public key on the DNS record as well as a private key that mail servers transporting the email to the recipient use to validate authenticity. The secret key is the DKIM signature in the email header.
The digital signature instructs the MTA or receiving mail server on where to find details on the public key for email authentication. Finally, the public key is used to validate the encrypted key in the DKIM signature. This demonstrates a link between the email and the sending domain, where the public key is stored.
Despite how safe all of this appears to be, hackers can still obtain DKIM keys and use them to impersonate a sender. As a result, it is suggested that DKIM keys be changed a few times per year.
According to a 2015 article on CircleID.com, some ESPs may exchange DKIM signatures among customers. That’s bad because a tainted digital signature could affect a large number of businesses at once. Hopefully, this problem is no longer as widespread as the report claims. However, if your ESP is giving your DKIM signature, it’s a question worth asking.
If you need to make your own digital signature, there are DKIM generators that can help you create these email authentication records. You can also learn more about DKIM signatures and see a sample record on our blog.
3. DMARC Protocol (Domain-based Message Authentication, Reporting, and Conformance)
PayPal actually led a group in developing DMARC technology to improve 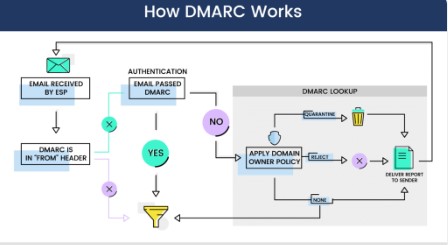
current email authentication methods. Cybercriminals frequently spoof PayPal by using bogus emails. Several other significant brands, as well as large mailbox providers, quickly adopted the method.
Technically, DMARC is a policy that mail servers on the receiving end refer to before sending an email. When authentication fails, DMARC assists in determining how to handle the communication.
This policy, also known as Domain-based Message Authentication, Reporting, and Conformance, is another DNS entry. It indicates whether a sending domain uses SPF, DKIM, or both protocols for authentication. Because it provides a common framework that uses both protocols, DMARC is often characterized as a way to get the most out of SPF and DKIM.
For many people, missing an essential, legitimate email is worse than allowing spam into their inbox. Real emails may fail DKIM and SPF authentication for a variety of causes. As a result, mailbox providers may allow emails to pass if they do not pass the test but appear to originate from a legitimate sending domain. DMARC clarifies what to do.
A DMARC policy enables senders to build a framework that outlines email authentication methods and specifies how to handle messages that violate the policy. Domain owners have three choices for dealing with emails that fail DMARC validation:
The three DMARC p= rules are:
- p=none: Take no action. Treat the communication as if there was no DMARC validation. This policy also aids in gaining a grasp of the email stream while not interfering with the flow.
- p=quarantine: Accept the email but send it to the junk or spam folder instead of the primary inbox. Alternatively, isolate the suspicious communication for further investigation.
- p=reject: Disable email transmission to any folder. The sender will be informed as to why the communication was not delivered.
A DMARC policy that rejects unvalidated emails is the strongest, but it can cause emails from a domain to cease flowing if SPF and DKIM fail for some reason.
One advantage of adopting a DMARC policy is that senders receive regular DMARC reports, which include the following information:
- Which servers and third parties are sending emails to your chosen domain?
- The proportion of emails that satisfy DMARC.
- What servers or third parties are delivering emails that failed DMARC?
- What steps do receive mail servers perform in response to unauthenticated emails?
DMARC is still far from ideal. It, like SPF, may fail during email sending. DMARC may also be difficult for senders to set up, and worries about stopping the flow of valid emails discourage stringent policies.
However, if your organization is successful in setting up and implementing a successful DMARC policy, you will have an effective way to stop most phishing emails that try to spoof your sending domain.
4. BIMI (Brand Indicators for Message Identification)
BIMI is the most recent email authentication system. Unlike the other standards, BIMI produces something that your subscribers can see in their inboxes. When properly configured, BIMI shows a brand-designated logo next to messages in the inbox.
The BIMI logo indicates that an email can be trusted because it indicates that other email authentication techniques are in place. It informs subscribers that communication is genuine. This adds an extra layer of security because, even if scammers manage to deliver a phishing email, it will not show a logo.
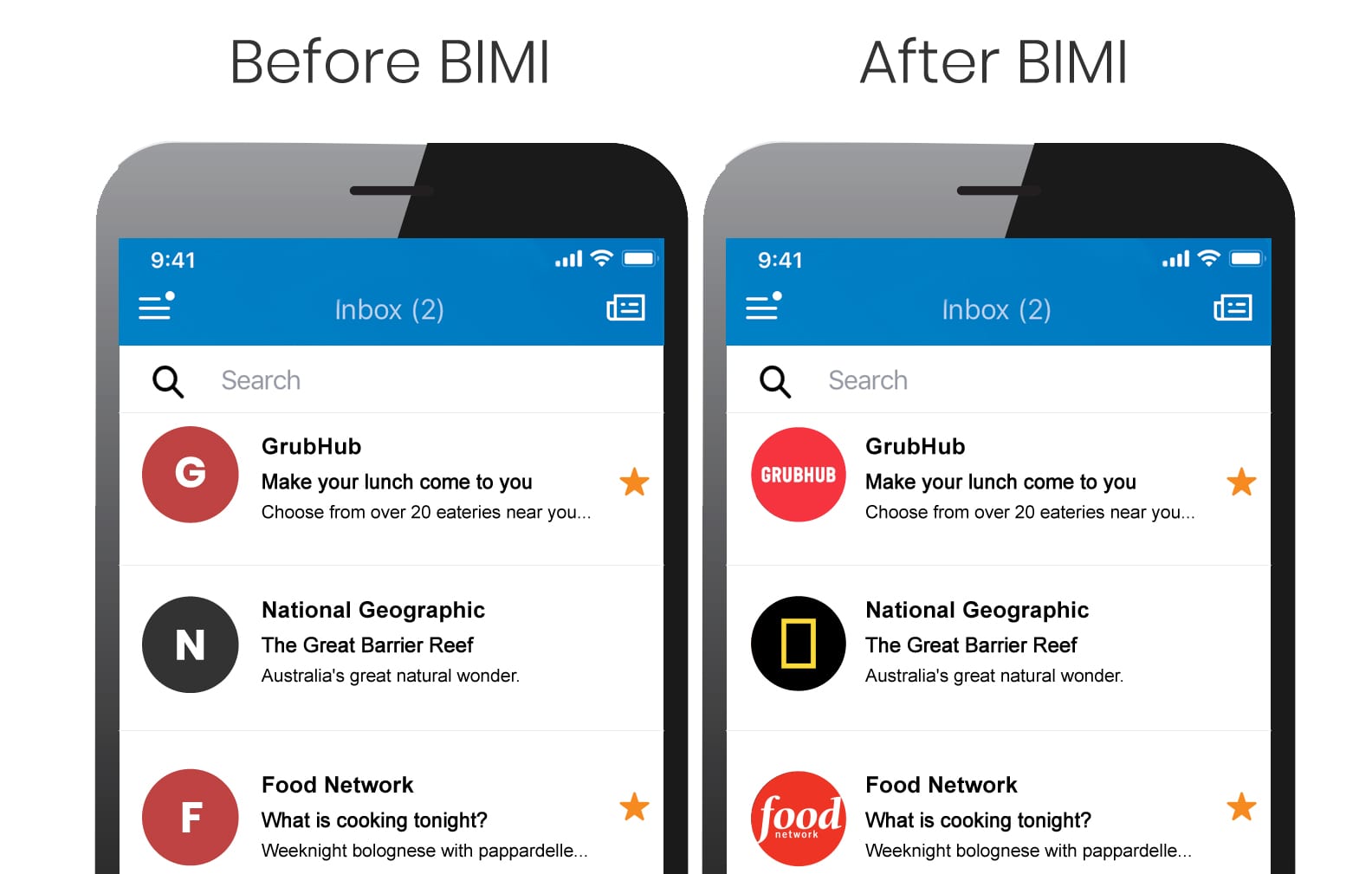
To get mailbox providers to show the BIMI logo, you must have a fully functional DMARC policy in place with SPF and DKIM records set up. In some respects, BIMI is the payoff for pursuing other email authentication methods.
BIMI, like the other protocols, is a TXT entry linked to a domain’s DNS. However, before you can insert a BIMI record, you must first have a correctly formatted logo.
Compatible BIMI logos are SVG files in the form of a perfect square that can be cropped into a circle. They require a solid foundation and should be distributed over HTTPS. BIMI logo images should be small, no larger than 32kb. Finally, to satisfy standards, your logo must be a registered brand.
The use of BIMI for email verification is growing. So far, only a few mailbox providers allow the display of BIMI logos. This includes Yahoo, the Australian email client Fastmail, and Verizon platforms such as AOL and Netscape.
In 2020, Google will start a Gmail pilot program for BIMI. Gmail will formally begin supporting BIMI in July 2021. That’s significant because a sizable percentage of your list is probably using Gmail. It definitely makes the time and work spent setting up email authentication protocols seem worthwhile.
Implementing BIMI should eventually increase subscriber trust in the source of your emails.
Some facts
- Over 90% of cyber-attacks begin with email communication.
- Every day, 3.1 billion domain-spoofing emails are sent.
- Since 2016, email spoofing and hacking have cost the global economy an estimated $26 billion.
- The FBI recorded 467,000 successful cyber-attacks in 2019, with email accounting for 24% of them.
- The typical scam defrauded users of $75,000
- An attacker posing as city manager Steve Kanellakos duped the Canadian City
- Treasure into transferring $98,000 from taxpayer money.
- Mattel was duped into sending $3 million to a Chinese account, but it was able to recover the funds after the defrauded finance executive confirmed that the email message was not sent by the CEO, Christopher Sinclair.
- The Crelan bank in Belgium was duped into sending €70 million to the assailants.
ad



Comments are closed.