What is Address Resolution Protocol (ARP)?
The Address Resolution Protocol (ARP) is a protocol or procedure designed to establish a connection between a dynamic Internet Protocol (IP) address, which can change, and a fixed physical machine address, also referred to as a media access control (MAC) address, in a local-area network (LAN). This mapping process is essential because IP and MAC addresses have different lengths, necessitating translation to enable systems to recognize and communicate with each other. The most commonly used IP version is IPv4, which uses 32-bit addresses, while MAC addresses consist of 48 bits. ARP facilitates the conversion of 32-bit IP addresses to 48-bit MAC addresses and vice versa.
The Open Systems Interconnection (OSI) model, developed in the late 1970s, provides a layered approach to understanding the workings of a networking system. This model visualizes network operations, helping IT teams identify the impact of each layer on specific applications, devices, or software within the network. It also clarifies which IT or engineering professional is responsible for managing each layer.
ad
The MAC address operates within the data link layer, which is responsible for establishing and terminating connections between physically connected devices to facilitate data transfer. On the other hand, the IP address corresponds to the network layer, responsible for forwarding data packets through various routers. ARP bridges the gap between these layers.
What Does ARP Do and How Does It Work?
When a new computer joins a local area network (LAN), it is assigned a unique IP address for identification and communication.
ad
Data packets destined for a specific host machine arrive at a gateway, a network hardware component that facilitates data flow between different networks. The gateway requests the ARP program to find a MAC address corresponding to the given IP address. The ARP cache maintains a list of IP addresses and their associated MAC addresses. While the ARP cache is dynamic, network users can also configure a static ARP table containing IP-MAC address pairs.
ARP caches are present on all operating systems within an IPv4 Ethernet network. Whenever a device requires a MAC address to send data to another device on the LAN, it checks its ARP cache first to determine if the IP-to-MAC address mapping already exists. If the mapping is found, a new request is unnecessary. However, if the translation has not been previously established, a request for network addresses is sent, and ARP resolves the mapping.
The size of an ARP cache is intentionally limited, and entries typically remain in the cache for only a brief period. Regular purging is conducted to free up space. This design enhances privacy and security, preventing cyber attackers from stealing or spoofing IP addresses. Unlike MAC addresses, which are static, IP addresses are subject to frequent updates.
During the purging process, unused addresses are removed, as well as any data associated with unsuccessful attempts to communicate with computers not connected to the network or those that are powered off.
What Are the Types of ARP?
There are four types of Address Resolution Protocol:
- Proxy ARP
- Gratuitous ARP
- Reverse ARP
- Inverse ARP
Proxy ARP
Proxy ARP is a method in which a proxy device within a particular network responds to an ARP request for an IP address that doesn’t belong to that network. The proxy has knowledge of the destination of the traffic and provides its own MAC address as the destination.
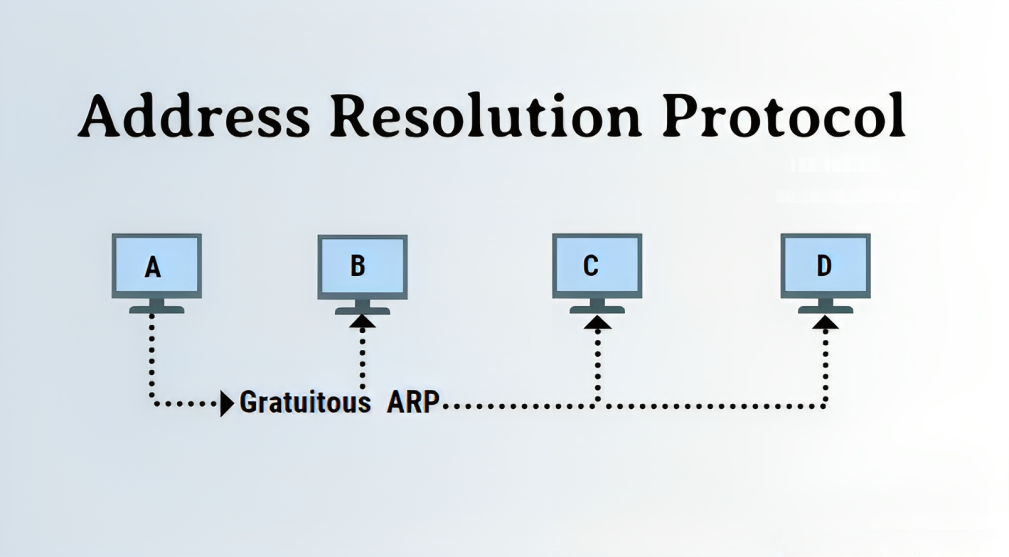
Gratuitous ARP
Gratuitous ARP serves as an administrative procedure, enabling a host on a network to independently announce or update its IP-to-MAC address association. Unlike conventional ARP, Gratuitous ARP is initiated without any ARP request for translating an IP address to a MAC address.
Reverse ARP (RARP)
Host machines lacking knowledge of their own IP address can utilize the Reverse Address Resolution Protocol (RARP) for the purpose of self-discovery.
Inverse ARP (IARP)
While ARP uses an IP address to locate a MAC address, Inverse ARP (IARP) operates in the opposite direction, using a MAC address to discover the corresponding IP address.
What is ARP in Networking Useful For?
ARP serves a critical function by translating the software address (IP address) of a host or computer on the network into its hardware address (MAC address). Without ARP, a host would be unable to discover the hardware address of another host. Within the LAN, a table or directory is maintained, correlating IP addresses to the MAC addresses of various devices, encompassing endpoints and routers within the network.
This table or directory isn’t manually managed by users or IT administrators. Instead, the ARP protocol dynamically generates entries as required. When a user’s device lacks the hardware address of the intended host, it broadcasts a message to all hosts on the network requesting this address. Once the correct destination host receives the request, it replies with its hardware address, which is then stored in the ARP directory or table.
If ARP support is unavailable, manual entries can be added to this directory.
What Is ARP Spoofing/ARP Poisoning Attack?
ARP spoofing, also recognized as ARP poison routing or ARP cache poisoning, represents a form of malicious attack. In this tactic, a cybercriminal deliberately sends false ARP messages to a targeted LAN. The aim is to link their MAC address with the IP address of a legitimate device or server within the network. By establishing this connection, the attacker reroutes data from the victim’s computer to their own system instead of the intended recipient.
The dangers of ARP spoofing lie in its potential to facilitate the transmission of sensitive information between computers without the victims being aware. Moreover, ARP spoofing opens doors to various other types of cyberattacks, such as:
Man-in-the-Middle (MTM) Attacks
A man-in-the-middle (MITM) attack is a form of covert eavesdropping. In this attack, a cybercriminal intercepts, modifies, and reroutes messages between two unsuspecting parties. The objective is to steal sensitive information. The attacker may manipulate the communication between one or both parties, employing sophisticated software that mimics various communication styles, making MITM attacks challenging to detect and thwart.
The process begins when malware infiltrates a victim’s web browser. The attacker is primarily interested in the data shared by the victim, including sensitive information like usernames, passwords, and account details exchanged in online conversations.
Once the attacker gains control, they establish a proxy connection between the victim and a legitimate website, often using a deceptive, lookalike site. This proxy setup enables them to intercept data flowing between the victim and the genuine website. Cybercriminals often exploit this method, particularly in the context of online banking and e-commerce websites, to pilfer personal and financial information.
Denial-of-Service Attacks
A denial-of-service (DoS) attack is a tactic employed by cybercriminals to inundate systems, servers, and networks with excessive traffic, rendering them inaccessible to users. A more extensive variation of this attack is the distributed denial-of-service (DDoS) attack, which leverages a significantly larger number of sources to flood a system with traffic.
These types of attacks exploit known vulnerabilities in network protocols. When a vulnerable network is subjected to a substantial volume of packets, it can become overwhelmed, resulting in service unavailability.
Session Hijacking
Session hijacking takes place when a cyberattacker acquires a user’s session ID, thereby seizing control of the user’s web session and impersonating the user. Armed with the session ID, the attacker gains the ability to carry out any authorized tasks or activities on the network that the user can perform.
Authentication is the process wherein a user seeks access to a system or attempts to log in to a secure website or web service. The session ID is usually stored in a browser cookie, and during session hijacking, the attacker intercepts the authentication process in real-time, enabling their intrusion.
FAQ’s
What exactly is the role of ARP in networking?
ARP, or the Address Resolution Protocol, plays a pivotal role in networking by connecting dynamic IP addresses to fixed MAC addresses within a local-area network (LAN). This connection is essential for seamless communication between devices with different address lengths.
Can you explain the purpose of ARP in simple terms?
Certainly! ARP is like a translator in a network. It helps in matching the unique identity numbers of devices (IP addresses) with their physical addresses (MAC addresses), enabling them to communicate effectively.
How does ARP work practically in a network setting?
When a new device joins a LAN, it gets a unique IP address. Whenever data is sent to a specific device, a gateway asks ARP to find the matching MAC address for the given IP. ARP keeps a list of these matches in a cache, dynamically updating it as needed for smooth communication.
Are there different types of ARP? If so, what sets them apart?
Yes, there are several types of ARP. Proxy ARP responds to IP requests from devices outside the network. Gratuitous ARP is like an independent update for IP-to-MAC associations. Reverse ARP helps in self-discovering unknown IP addresses, and Inverse ARP does the opposite by finding an IP based on a MAC address.
How significant is ARP spoofing in the realm of cybersecurity?
ARP spoofing is a malicious attack where false ARP messages are sent to link the attacker’s MAC address with a legitimate IP address in the network. This manipulation allows the attacker to redirect data, compromising network integrity.
What measures can be taken to prevent ARP spoofing or mitigate its impact?
Preventing ARP spoofing involves implementing security measures such as using static ARP tables, setting up intrusion detection systems, and regularly monitoring network activities to detect suspicious behavior. It’s also essential to educate network users about potential security threats.
How is session hijacking related to ARP and what risks does it pose in a network?
Session hijacking occurs when an attacker steals a user’s session ID, assuming the user’s identity. This can be related to ARP as it may happen during the authentication process, where session IDs are stored in cookies. The risks include unauthorized access to sensitive data and misuse of user privileges.
What practical steps can be taken to protect against session hijacking and other related cyber threats?
Protecting against session hijacking involves employing secure encryption, implementing strong session management practices, and regularly updating and patching systems. Additionally, employing secure cookies and employing robust encryption techniques can also aid in bolstering network security against such threats.
Conclusion
ARP plays a crucial role in enabling seamless communication within networks by linking IP and MAC addresses. Understanding the OSI model, types of ARP, and potential cyber threats like ARP spoofing and session hijacking is key to maintaining network security. By implementing preventive measures, users can better protect their networks and thwart potential cyber threats.
ad


Comments are closed.