An Overview of Packet Switching on Computer Networks
Some computer network protocols use packet switching to deliver data across a local or long-distance connection. Frame Relay, IP, and X.25 are examples of packet switching protocols.
What is packet switching in a computer network?
The transmission of individual bits of data from one network to another is an example of packet switching. Transferring data using these data chunks or “packets” enables a faster and more efficient process.
When a user sends a file across a network, the file will typically be transferred in a series of smaller data packets rather than in a single contiguous chunk. For illustration’s sake, a file that is 3 megabytes in size will be broken up into packets, each of which will have a packet header that contains information such as the origin IP address, the destination IP address, the total number of packets in the data file, and the sequence number.
Types of Packet Switching In a Network
The following are two approaches to packet switching:
- Datagram Packet Switching
- Virtual Circuit Switching
Datagram Packet Switching
With Datagram Switching, the datagram is what we call the packet. “Connectionless Packet Switching” or “Datagram Packet Switching” Each packet is individually routed by network devices based on the destination address contained in each packet.
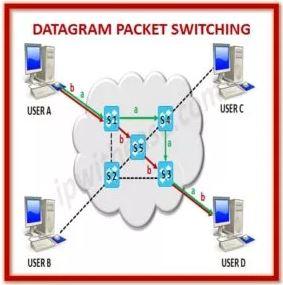
- Each packet is handled as if it were an island unto itself.
- It is at the network layer that datagram packets are switched.
- Because the packet switch does not keep track of the current connection state, this is referred to as “connectionless packet switching.”
- Paths can change in Datagram packet switching.
- The intermediate nodes are in charge of making routing decisions in order to move the packets forward.
- In this way, datagrams that are part of the same message can take various routes to their final destination.
- All packets are reassembled on the receiving node to restore the message to its original form.
- Packets can also be dropped or lost due to a lack of resources.
- Datagrams are typically reordered or lost datagrams are requested before being passed on to the application in most protocols by the upper-layer protocol.
Virtual Circuit Switching
Switching based on connections is also known as virtual circuit switching. Circuit switching and datagram packet switching are both present in this switching. Data packets are first assembled and then sequentially numbered in this form of packet traveling. They are now ready to follow a predetermined route, one at a time. Since all data packets are sent sequentially, the address information isn’t necessary.
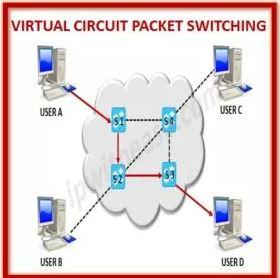
- Setup and dismantling are also included in the process.
- In a circuit-switched network, the allocation of resources is done during the initial setup phase. In datagram networks, the allocation of resources is done on demand.
- Like a datagram network, the data is sent in packets, with the destination address included in each packet’s header.
- When a user connects to a Virtual network, all packets follow the same path established during the initial connection.
- The data link layer is typically where this switching is implemented.
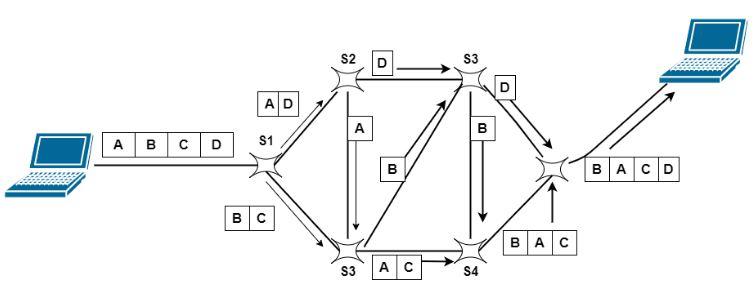
How Packet Switching Works?
Packet switching divides data into segments that are packaged in specially formatted units known as packets. Network switches and routers are typically used to route these from the source to the destination. The data is then reassembled at the destination.
Each packet contains address information that identifies the sending and receiving computers. Network switches and routers use these addresses to determine how to best transfer the packet between hops on the path to its destination. If necessary, free apps such as Wireshark can capture and display the data.
What Exactly Is a Hop?
A hop is a segment of the full path between the source and the destination in computer networking. When communicating over the internet, for example, data is routed through a series of intermediate devices such as routers and switches rather than flowing directly over a single wire. Each device causes data to bounce between point-to-point network connections.
The hop count is the total number of devices that a given data packet passes through. In general, the more hops data packets must travel to reach their destination, the longer the transmission delay.
Ping and other network utilities can be used to determine the hop count to a specific destination. Ping sends out packets with a field reserved for the hop count. When a capable device receives these packets, it modifies the packet and adds one hop to the hop count. Furthermore, the device compares the hop count to a predetermined limit and discards the packet if it is too high. This action prevents packets from bouncing around the network indefinitely due to routing errors.
The Benefits and Drawbacks of Packet Switching.
Packet switching is an alternative to the circuit switching protocols that were previously used for telephone networks and, in some cases, ISDN connections.
When compared to circuit switching, packet switching has the following advantages and disadvantages:
Benefits
- Because of the flexibility in routing smaller packets over shared links, the overall network bandwidth is used more efficiently.
- Packet switching networks are frequently less expensive to build because less equipment is required.
- Reliability. If a packet does not arrive at its destination as expected, the receiving computer detects that one packet is missing and requests that it be resent.
- Packet switching provides automatic rerouting if any node along the path fails.
Drawbacks
- Longer message delivery times due to the time required to package and route packets. Delays are not significant in many applications, but in high-performance applications such as real-time video, additional Quality of Service (QoS) technology is frequently required to achieve the required performance levels.
- The use of shared physical links creates the possibility of network security risks. Protocols and other related elements in packet traveling networks must comply with the necessary security safeguards.
- Latency can be unpredictable. Read more about the difference between latency and bandwidth.
Packet Traveling @ YT
ad


Comments are closed.