What is SSL/TLS Handshake?
Whenever we browse a website, make an online purchase, or check our email, data is exchanged between our devices and remote servers. This raises the important question of how we can ensure the security of our data from potential eavesdropping. The answer lies in encryption protocols like SSL/TLS.
SSL (Secure Sockets Layer) and its successor, TLS (Transport Layer Security), are security protocols designed to establish an encrypted connection between a client (such as your web browser) and a server (the website you are accessing). This encrypted connection ensures that data can be transmitted securely.
ad
Let’s take a closer look at the SSL/TLS handshake process and the sequential steps involved in ensuring secure internet connections.
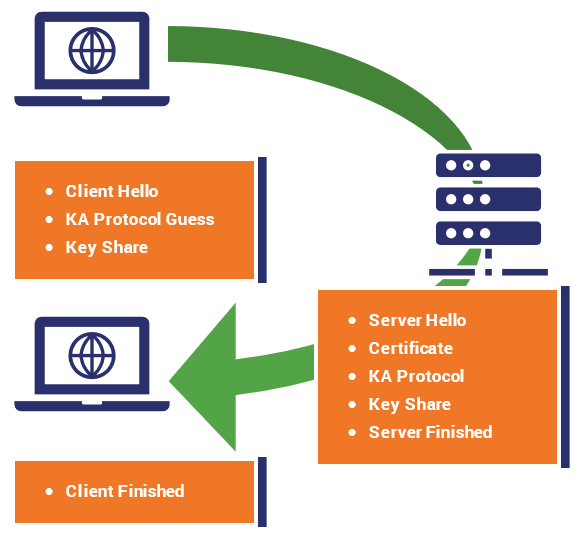
An Overview of the SSL/TLS Handshake
The SSL/TLS handshake is a procedural sequence facilitating mutual authentication, encryption standard agreement, and the creation of a secure conduit for data transmission between two parties, typically a client and a server.
ad
This process can be likened to an intricate digital choreography characterized by rapid, intricate communication. To elucidate this handshake, let’s examine its steps methodically:
- Introduction (ClientHello): Upon initiating a secure website request, your browser dispatches a “ClientHello” message to the server, containing crucial details like supported SSL/TLS versions and cipher suites.
- Server’s Response (ServerHello): In return, the server issues a “ServerHello” message, specifying the highest SSL/TLS version and cipher suite agreed upon by both parties.
- Server’s Credentials: The server provides its digital certificate, validated by a Certificate Authority (CA), analogous to an identification document affirming its legitimacy.
- Client’s Verification and Key Generation: Your browser authenticates the server’s certificate. Once confirmed, it utilizes the server’s public key to encrypt a ‘premaster secret’ – a unique session key – and transmits it back to the server.
- Establishing a Secure Connection: The server decrypts the premaster secret using its private key. Consequently, both server and client derive the session key, instrumental for symmetric encryption of all subsequent communication.
Key Components of the SSL/TLS Handshake
Now that we’ve delineated the fundamental steps of the SSL/TLS handshake, let’s delve into the fundamental concepts and technologies underpinning this process:
Asymmetric Encryption
This entails utilizing a pair of keys – one public and one private – for encryption purposes. Data encrypted with the public key can only be decrypted with the corresponding private key, ensuring secure data transmission.
Symmetric Encryption
This employs a single shared key for both encryption and decryption operations. Symmetric encryption offers swifter processing compared to asymmetric encryption. Within the SSL/TLS handshake, asymmetric encryption is utilized to securely exchange the symmetric session key between parties.
Digital Certificates
These electronic credentials bind a public key to an entity, such as a website or organization, facilitating secure authentication on the internet. Digital certificates are issued by Certificate Authorities (CAs).
Cipher Suites
A cipher suite comprises a set of algorithms defining the cryptographic parameters for an SSL/TLS session. This encompasses key exchange methods, encryption ciphers, and hash functions.
Session Keys
Temporary symmetric keys, known as session keys, are generated by both the client and server for each session. All data transmitted during the session is encrypted using these keys, enhancing security.
Mutual TLS
Mutual TLS (mTLS) entails both the client and server authenticating each other using digital certificates. This offers heightened security compared to standard one-way TLS authentication. In mTLS, the client must possess its own certificate and key pair.
Putting it All Together
The SSL/TLS handshake amalgamates these technologies to establish a securely encrypted session:
- Digital certificates validate the server’s identity.
- Asymmetric encryption facilitates the secure exchange of the symmetric session key.
- Cipher suites furnish encryption algorithms.
- Session keys encrypt the data flow between the parties.
📚 Also Read: Step-by-Step Guide for Installing Comodo SSL/TLS Certificate in Tomcat
Why the SSL/TLS Handshake Matters
An uninterrupted SSL/TLS handshake facilitates encrypted data transmission, safeguarding our digital realm. It ensures secure online commerce, communication, and connectivity by:
- Verifying the authenticity of the connected site, preventing impersonation.
- Encrypting all exchanged data throughout the session.
- Guaranteeing that no third party can intercept or alter the information while it traverses the internet.
Devoid of the SSL/TLS handshake, our sensitive information would be vulnerable to exposure online.
Conclusion
In the digital sphere, the SSL/TLS handshake plays a vital role in securing online activities. By establishing encrypted connections, verifying server authenticity, and protecting data transmissions, it ensures privacy and security. Through technologies like encryption, digital certificates, and session keys, it shields sensitive information from threats. Without it, online interactions would be vulnerable. Therefore, the SSL/TLS handshake is indispensable for safeguarding digital transactions and maintaining trust online.
ad


Comments are closed.