What is a Smurf Attack?
A Smurf attack, a variant of distributed denial of service (DDoS) attack, disrupts computer networks by exploiting vulnerabilities in the Internet Protocol (IP) and Internet Control Message Protocols (ICMP).
ad
What Is the History of Smurf Attacks?
The Smurf attack originated as code authored by renowned hacker Dan Moschuk, alias TFreak. One of the initial instances of employing this method occurred in 1998, targeting the University of Minnesota. This attack induced a cyber traffic bottleneck that extended to the Minnesota Regional Network, a statewide internet service provider (ISP). Consequently, computers throughout the state experienced shutdowns, network deceleration, and incurred data losses.
What Are the Types of Smurf Attacks?
What is the meaning of smurfing? The explanation varies depending on the types of DDoS attacks encountered, typically categorized as basic or advanced smurf attacks.
ad
Basic Smurf Attack
In a basic smurf attack, the assailant inundates the target network with numerous ICMP request packets. These packets contain falsified source addresses sent to the network’s broadcast address, compelling every device on the network receiving the request to respond to the spoofed source. This generates a substantial volume of traffic, eventually leading to the incapacitation of the target system.
Advanced Smurf Attack
An advanced smurf attack initiates similarly to a basic attack. However, the echo requests are engineered to configure sources to respond to additional third-party victims. This capability allows attackers to simultaneously target multiple victims, resulting in the slowdown of larger networks and the targeting of broader victim groups and extensive sections of the internet.
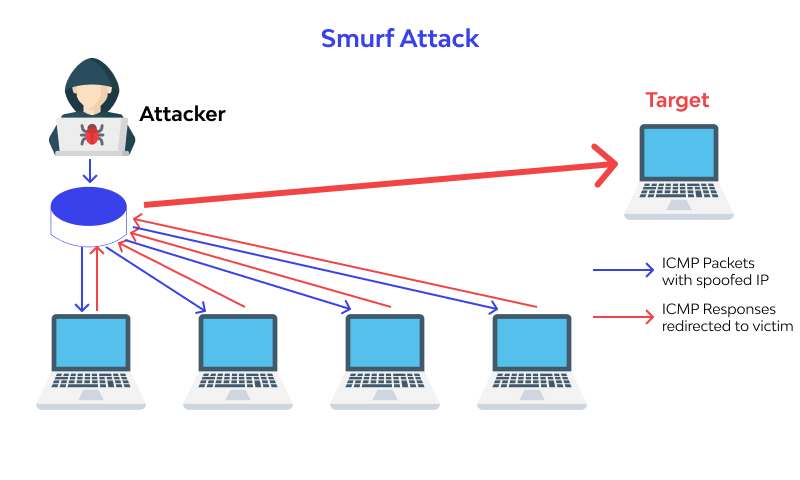
How a Smurf Attack Works
Initially, the malicious program generates a network packet with a falsified IP address, a tactic called “spoofing.” Contained within the packet is an ICMP ping message, soliciting responses from network nodes upon reception. These responses, or “echoes,” are then directed back to various network IP addresses, establishing a perpetual cycle. When coupled with IP broadcasting, which disseminates the malicious packet to all IP addresses within a network, the Smurf attack swiftly triggers a complete denial of service.
Smurf Attack Transmission and Effects
Accidentally downloading the Smurf Trojan can occur from an unverified website or through an infected email link. Typically lying dormant until activated remotely, many Smurf Trojans are bundled with rootkits, facilitating hackers in establishing backdoors for easy system access. One effective countermeasure against a Smurf attack involves disabling IP broadcast addressing on all network routers. Since this function sees rare usage, deactivating it prevents the attack from overwhelming a network.
If a Smurf DDoS attack manages to succeed, it can effectively incapacitate company servers for extended periods, resulting in substantial revenue loss and customer dissatisfaction. Additionally, such attacks might serve as a camouflage for more nefarious activities like intellectual property theft. Addressing Smurf and similar DDoS assaults demands a robust prevention strategy capable of monitoring network traffic for anomalies, such as unusual packet volume, behavior, and signatures. Many malware bots exhibit distinct characteristics, and employing the appropriate security service can preemptively thwart a Smurf or any other DDoS attack.
📚 Also Read:What is Active Defense?
How to Protect Yourself
While the term “Smurf Attack” may sound whimsical, it presents genuine threats when servers become overwhelmed. Disabling IP broadcasting and utilizing reliable detection tools are key measures to mitigate the likelihood and impact of such attacks.
Here are a couple of steps for Smurf attack mitigation:
- Ensure the blocking of directed broadcast traffic entering the network.
- Configure hosts and routers not to respond to ICMP echo requests.
A related variant to the Smurf attack is the Fraggle attack, which operates similarly but employs UDP packets instead of ICMP echo requests to the direct broadcast address. Mitigating the Fraggle attack involves the same process as for the Smurf attack.
Conclusion
Smurf attacks, originating from code by hacker TFreak in 1998, remain a potent threat to computer networks. These attacks exploit vulnerabilities in IP and ICMP protocols, causing disruptions and data loss. Understanding their transmission, effects, and mitigation strategies is crucial for network security. By disabling IP broadcasting, deploying detection tools, and staying informed about variants like Fraggle attacks, proactive defenses can be established against Smurf attacks in the digital age.
ad


Comments are closed.