What is Role-Based Access Control (RBAC)?
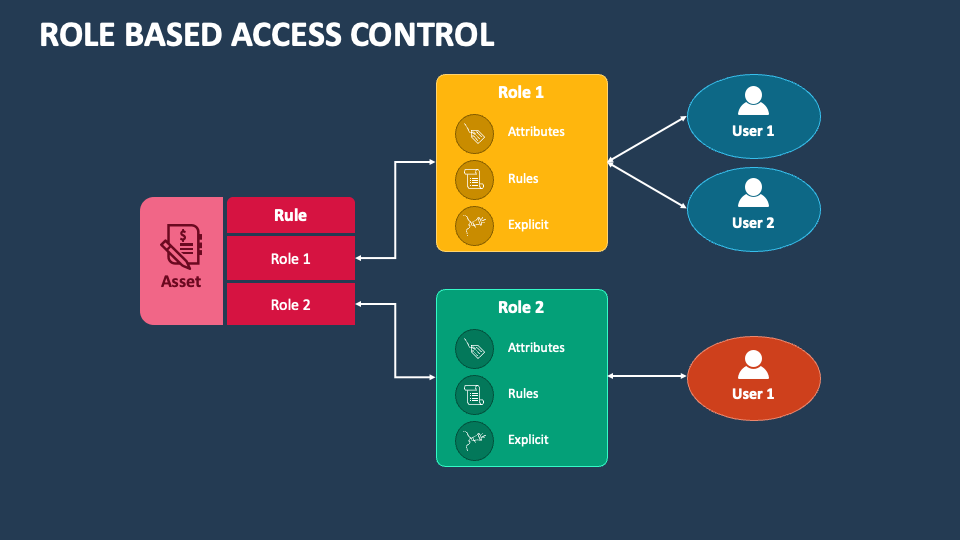
Role-based access control (RBAC) systems allocate access and actions based on an individual’s role within the system. All individuals assigned to a particular role share the same set of rights. People in different roles have distinct rights.
ad
What is Role-Based Access Control (RBAC)?
Role-based access control (RBAC) limits network access based on an individual’s role within an organization, becoming a primary method for advanced access control. In RBAC, roles determine the levels of access employees have to the network.
Employees are granted access only to the information necessary for their job duties. Access can depend on various factors such as authority, responsibility, and job competency. Additionally, access to computer resources can be restricted to specific tasks like viewing, creating, or modifying files.
Consequently, lower-level employees typically do not have access to sensitive data unless it is required for their responsibilities. This approach is particularly useful for managing access when there are many employees, third-parties, and contractors, making close monitoring challenging. Implementing RBAC helps secure your company’s sensitive data and critical applications.
ad
Why Does a System Need RBAC?
Every company has sensitive documents, programs, and records. If protected too strictly, your company’s operations can come to a halt. If left open, catastrophic security issues may arise.
This is where role-based access control (RBAC) comes in.
RBAC allows you to grant access to those who need it while blocking those who don’t. Changes are made based on a person’s role rather than individual attributes, and these changes can be implemented quickly by modifying role-based access.
For IT professionals, understanding the intricacies of RBAC is essential. In 2004, the American National Standards Institute adopted RBAC principles as an industry consensus standard. You’ll likely need to implement RBAC or justify why it may not be suitable for your company.
📚 Also Read: What Is Network Access Control (NAC)?
How Do Roles Work Within RBAC?
In an RBAC system, roles determine authorization, making it crucial to define them properly. Improperly defined roles can hinder large groups within your company from performing their tasks.
Roles can be defined by:
- Authority: Senior management needs access to files that interns should never see.
- Responsibility: A board member and a CEO might have similar authority but are responsible for different core functions.
- Competence: A skilled worker can handle sensitive documents without errors, whereas a novice might make critical mistakes, necessitating tailored access levels.
Roles can also have overlapping responsibilities and privileges. For instance, someone with the role of “project manager” might also function as a “team leader” or “resource allocator.” A role hierarchy defines a person who possesses the attributes of multiple other roles, meaning one role can encompass many others.
What Are Role-Based Access Control Permissions?
Permissions define what people can access and do within the system. Think of permissions as the rules that align with the roles you have established.
Your permissions should cover:
- Access: Who can open a specific drive, program, file, or record? Who shouldn’t even know these things exist? Access controls limit what people can see.
- Reading: Who can view these documents, even if they can’t modify them? Some roles may have the ability to reference materials without making changes.
- Writing: Who can edit documents? Does someone need to approve the changes, or are they permanent? Permissions will define this.
- Sharing: Who can download a document or send it as an email attachment? Some users may be able to reference materials but not share them.
- Finances: Who can charge money or offer refunds? Permissions might include the ability to handle charges and refunds, set up credit accounts, or cancel payments.
It’s essential to remember that permissions follow roles, not the other way around. Determine what each role should do and then apply permissions accordingly.
Don’t allow employees to demand permissions outside the scope of their current role. Altering permissions on an individual basis can quickly make the system unmanageable.
Benefits of Role-Based Access Control
Managing and auditing network access is crucial for information security. Access should be granted on a need-to-know basis. With hundreds or thousands of employees, security is more effectively maintained by limiting unnecessary access to sensitive information based on each user’s defined role within the organization. Additional benefits include:
- Reducing administrative work and IT support: RBAC minimizes the need for paperwork and frequent password changes when an employee is hired or changes roles. Instead, roles can be added and switched quickly, implemented globally across operating systems, platforms, and applications, and reduces potential errors in assigning user permissions. This time-saving aspect is one of the economic benefits of RBAC. Additionally, RBAC facilitates the integration of third-party users by assigning them predefined roles.
- Maximizing operational efficiency: RBAC provides a streamlined, logical approach. Rather than managing lower-level access control, roles can be aligned with the organizational structure, enabling users to perform their jobs more efficiently and independently.
- Improving compliance: Organizations must adhere to federal, state, and local regulations. An RBAC system helps companies meet statutory and regulatory requirements for privacy and confidentiality, as IT departments and executives can manage how data is accessed and used. This is particularly important for healthcare and financial institutions, which handle sensitive data such as PHI and PCI data.
RBAC vs. ABAC: Which Is Better?
Before diving into the specifics of implementing a role-based access control (RBAC) model, it’s worth discussing an alternative: attribute-based access control (ABAC). ABAC is one of the most well-known models that companies consider and can be useful in certain settings.
ABAC, or attribute-based access control, greatly expands your role options. Instead of focusing on job titles, seniority, and similar attributes, you can consider:
- User types: Security clearances, financial knowledge, or citizenship status can influence the roles you create.
- Time of day: Restrict access to documents during the night when work should stop. Limit edits during periods when supervisors aren’t available. Block access to materials on weekends.
- Location: Ensure documents are accessed only on campus or within the country, for instance. Restrict access from home if appropriate.
This system relies on policies to enforce security rather than static permission types. Balancing these factors can be more complex due to the increased number of variables. Depending on your security needs, ABAC could be a smart choice for your organization.
Best Practices for Implementing RBAC
Introducing RBAC into your organization requires careful planning to avoid confusion and workplace disruptions. Here are some initial steps to consider:
- Assess Current Status: Compile a comprehensive list of all software, hardware, and applications with security measures in place, including passwords. Additionally, identify any physical security measures such as locked server rooms. Determine who currently has access to these resources to gain insight into your existing data security landscape.
- Identify Current Roles: Even without a formal roster, discuss and document the responsibilities of each team member. Ensure that organizing roles does not stifle creativity or disrupt the current organizational culture.
- Draft a Policy: Document any changes in a policy accessible to all current and future employees. Even with the use of an RBAC tool, a clear policy outlining the new system helps prevent potential issues.
- Implement Changes: Once you understand the current security status and roles, and have written a policy, proceed with making the necessary adjustments.
- Continuous Adaptation: Expect that the initial implementation of RBAC may require adjustments. Regularly evaluate roles and security measures to ensure effectiveness. Prioritize both the efficiency of creative processes and the security of your systems.
FAQ’s
What exactly does RBAC do?
RBAC controls access to system resources based on the roles assigned to users. It ensures that users have access only to the information necessary for their job duties, improving security and efficiency.
How does RBAC differ from other access control models?
RBAC differs from other access control models by focusing on predefined roles rather than individual user attributes. It simplifies access management by assigning permissions based on roles, making it easier to control access to system resources.
What are the main advantages of implementing RBAC?
The main advantages of RBAC include reducing administrative work and IT support, maximizing operational efficiency, and improving compliance with regulatory requirements. It helps organizations manage access to sensitive data more effectively and ensures that employees have appropriate access to system resources.
How can I implement RBAC in my organization?
Implementing RBAC requires careful planning and consideration of current roles and access levels within the organization. It involves assessing the current status, identifying roles, drafting a policy, and making necessary changes to the system.
Is RBAC suitable for all organizations?
While RBAC is a widely used access control model, it may not be suitable for all organizations. The choice between RBAC and other access control models depends on the specific needs and security requirements of the organization.
Conclusion
Role-based access control (RBAC) is pivotal in modern information security. By assigning access based on predefined roles, RBAC minimizes security risks and boosts operational efficiency. Despite the need for careful implementation, its benefits in reducing administrative tasks, maximizing efficiency, and enhancing compliance make it indispensable in safeguarding data and ensuring system integrity amidst evolving cyber threats.
ad


Comments are closed.