What is a honeypot and how does it work?
A honeypot is a certain method to entice someone to something. Just like Winnie-the-Pooh, hackers find it difficult to resist the attraction of a honeypot. While criminals may use honeypots to ensnare victims, detectives and cybersecurity teams also employ them to catch criminals and hackers. Keep reading to understand more about honeypots and their workings.
What is a honeypot?
ad
A honeypot is a virtual trap or decoy created to mimic a genuine element of a system, network, or any digital setting. These honeypots are deployed to divert cybercriminals from actual digital resources, and they can imitate software, server structures, or even an entire network convincingly to deceive cybercriminals.
Honeypot meaning
Although cybersecurity teams utilize honeypots as instruments to entice hackers and other wrongdoers into environments they can supervise and manage, the fundamental concept of a honeypot extends beyond this. A honeypot can encompass anything or any place that draws a specific type of individual.
ad
How honeypots work
Honeypots operate similarly to bait used to attract hackers or criminals, much like how honey can draw bears. In cybersecurity, honeypots are simulated digital assets or environments deliberately crafted to entice cybercriminals. These assets mimic legitimate computer systems, containing sensitive data and posing as insecure targets.
Typically, honeypots feature a subtle security vulnerability enticing enough to pique the interest of cybercriminals, diverting their attention away from the actual secure systems.
For instance, within a bank’s IT security framework, a honeypot system might resemble the bank’s network to outsiders or hackers. This strategy safeguards the genuine network by redirecting malicious activities.
Once hackers engage with the honeypot, security teams can monitor their actions, enabling analysts to comprehend hacker methods and motivations. This insight aids in detecting and thwarting cybercrime while assessing the effectiveness of security measures.
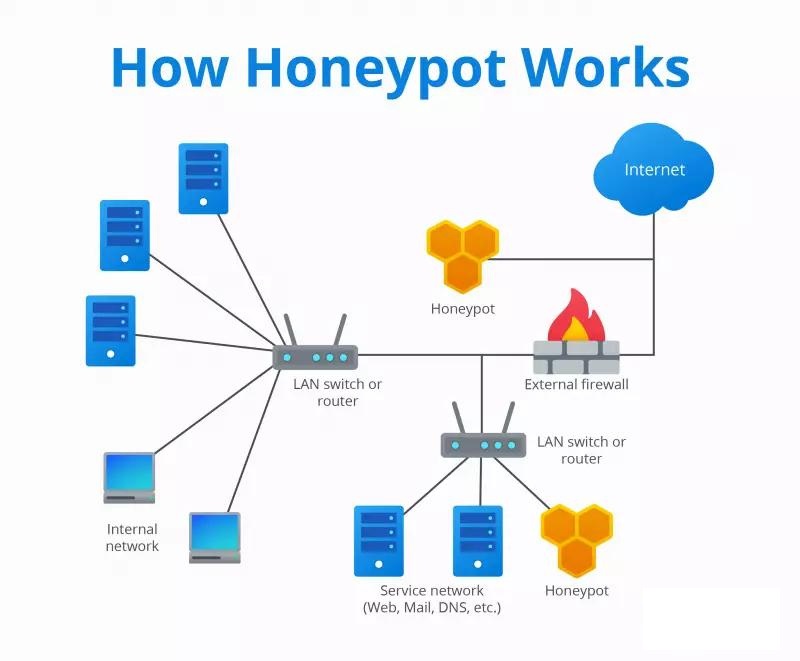
Honeypots are valuable for detecting and thwarting external attempts to breach internal networks. Placing a honeypot outside an external firewall attracts, deflects, and analyzes traffic for defensive purposes.
What are honeypots used for?
Honeypots are vital tools used by cybersecurity teams to protect valuable digital assets and develop effective strategies against hackers. They serve specific purposes in both research and operational contexts.
Research honeypots: In research, honeypots enable administrators to study hacker activity, gaining insights into digital threats and uncovering system vulnerabilities that might otherwise remain undetected. For example, setting up honeypots to attract fake traffic helps identify any real activity, indicating potential cybercriminal activity.
Production honeypots: In production environments, honeypots are deployed within networks to act as decoys, diverting hackers’ attention from genuine assets and reducing the risk of infiltration.
While hackers may use tactics similar to honeypots, such as watering hole attacks that lure unsuspecting users into disclosing personal data or downloading malware, “honeypot” in cybersecurity predominantly refers to defensive measures employed by security teams rather than offensive strategies used by hackers.
Types of honeypots
Just as there are diverse cyberthreats and types of hackers, there are various types of honeypots used to gather intelligence on these threats.
Here are five common types of honeypots:
- Email Honeypots (also known as spam traps) are fake email addresses created to attract and intercept spam emails. They help prevent spammers from targeting legitimate email addresses with malicious content and are used to study spamming activities.
- Database Honeypots contain fabricated and vulnerable datasets to attract attackers who breach firewalls. These honeypots monitor the frequency and nature of attacks targeting databases.
- Malware Honeypots mimic software applications and APIs (Application Programming Interfaces) to attract and capture malware attacks. They help identify API weaknesses and assist in developing anti-malware solutions.
- Spider Honeypots are designed to ensnare automated crawlers, such as malicious bots and ad-network crawlers, as they navigate the web looking for accessible web pages and links.
- HoneyBots represent a new type of honeypot developed by university researchers. Unlike traditional honeypots, HoneyBots can engage with hackers, mimicking legitimate systems to enhance their believability and gather valuable insights.
The Benefits of using honeypots
- Honeypots are effective tools for detecting threats by attracting hackers into a controlled environment where their activities can be monitored closely.
- They provide valuable data on cyberattacks, including insights into hacker behavior, tools, techniques, and new attack methods, helping security teams better understand the workings of cyber threats.
- Because honeypots only interact with genuine hacker activities, they generate fewer false positives when monitoring cybersecurity incidents. Additionally, they are typically self-sufficient and require minimal monitoring, making them cost-effective and low-maintenance solutions.
The dangers of honeypots
- Honeypots are primarily designed to gather attack data, which confines their effectiveness to monitoring hacking activities and identifying vulnerabilities.
- However, certain characteristics of honeypots may inadvertently alert knowledgeable hackers, enabling them to bypass these traps more easily.
- Moreover, if not adequately secured, honeypots can actually expand the organization’s attack surface, offering hackers an additional entry point into the system or network.
High-Interaction vs. Low-Interaction Honeypots
In the context of honeypot security, one distinction is between high-interaction and low-interaction honeypots:
High-interaction honeypots are fully functional decoys that closely emulate real IT systems or applications. They allow attackers to interact extensively with them, providing a full array of privileges and access. While high-interaction honeypots yield comprehensive insights into attackers’ techniques, they are more complex to set up and maintain.
On the other hand, low-interaction honeypots simulate specific aspects of IT environments by implementing selected applications or services, offering attackers limited interaction opportunities. These honeypots are easier to deploy, require fewer resources, but provide less realistic and detailed information compared to high-interaction honeypots.
Physical vs. Virtual Honeypots
Another significant difference among types of honeypots is the classification between physical and virtual:
A physical honeypot is an actual IT device or system connected to a network, possessing its own IP address. Physical honeypots can provide a higher level of realism but are less common due to their cost implications.
In contrast, a virtual honeypot emulates an operating system or application within a virtual machine. Virtualization enables IT teams to rapidly create and deploy new honeypots, though it does not facilitate the capture of attacks that exploit physical vulnerabilities.
What is the difference between a honeypot and a honeynet?
The main difference between a honeypot and a honeynet is that a honeynet consists of multiple interconnected honeypots, forming a larger-scale deception environment compared to a single honeypot. However, the core purpose of both remains unchanged: to collect and capture data on hackers, and they share the same basic functionality for this purpose.
What Are the Real-World Applications of Honeypots?
Honeypots are among the most effective defenses that IT teams and organizations can deploy against malicious actors. Here are several real-world scenarios illustrating the use of honeypots in cybersecurity:
- Government and Military: Government and military entities leverage honeypots to divert attackers away from critical targets. Honeypots play a crucial role in safeguarding vital infrastructure such as power grids and communication networks.
- Financial Industry: Given their high-profile status as targets, financial institutions benefit significantly from using honeypots. They can effectively detect and thwart fraudulent financial activities or attempts to steal customer data using honeypot technology.
- Intellectual Property Protection: Businesses reliant on safeguarding intellectual property employ honeypots to distract and isolate attackers seeking to compromise valuable IP assets.
Conclusion
Honeypots are powerful tools in cybersecurity, offering proactive threat detection and insights into attacker tactics. Despite potential risks, effective deployment involves clear objectives, robust security measures, and continuous monitoring. With proper management, honeypots can significantly bolster an organization’s defense against cyber threats.
ad


Comments are closed.