What is a digital certificate and why it’s so important?
A digital certificate is a file or electronic password that uses cryptography and the public key infrastructure (PKI) to confirm the legitimacy of a device, server, or user.
Organizations can employ digital certificate authentication to ensure that only trustworthy devices and users can connect to their networks. Another frequent application for digital certificates is to verify the legitimacy of a website to a web browser, often known as a secure sockets layer or SSL certificate.
A digital certificate contains identifiable information such as a user’s identity, company, or department, as well as the Internet Protocol (IP) address or serial number of a device. To validate its authenticity, digital certificates contain a copy of the certificate holder’s public key, which must be matched to a corresponding private key. Certificate authorities (CAs) provide public key certificates, which are used to authenticate the identity of the requesting device or user.
What exactly is a digital certificate, and why are they important?
A digital certificate is a certificate issued by a Certificate Authority (CA) to validate the certificate holder’s identity. The CA creates an encrypted digital certificate that includes the applicant’s public key and other identification information. A digital certificate is used to associate a public key with a specific person or business.
A digital certificate is an electronic file that authenticates the identity of a website, individual, company, user, device, or server by being linked to a cryptographic key pair. It’s also referred to as a public key certificate or an identification certificate. The certificate includes the subject, which serves as the identity component, as well as a digital signature.
A website, individual, company, device, user, or server’s identification and safe encryption are both ensured by digital certificates. They form the basis for implementing Public Key Infrastructure (PKI) security.
A trustworthy third party issues a digital certificate that validates the sender’s identity to the receiver and the receiver’s identity to the sender.
How Are Digital Certificates Used?
Digital certificates can be used to protect websites, devices, web servers, signatures, code, software, email, and other resources. Furthermore, digital certificates can aid in the encryption of data, the activation of HTTPS in the URL bar, the proof of a website’s legality, compliance with PCI standards, the improvement of SEO ranks for websites, and the strengthening of a brand’s identity.
Some applications for a digital certificate include the ones listed below:
- The security of debit card and credit card transactions depends on digital certificates. Digital certificates are typically incorporated on debit and credit cards to guarantee secure interactions with banks and merchant accounts.
- To protect broadband service from theft and modification, computer hardware manufacturers include digital certificates into cable modems.
- The technology of digital certificates is extensively used by digital payment firms to authenticate their ATMs, point-of-sale systems, and kiosks.
- Digital certificates, particularly SSL certificates, are used by websites to encrypt browser-server communications and to demonstrate their authenticity.
- Professional Email service providers also utilize digital certificate technology to secure emails and to distinguish one user from another and to sign documents electronically. Here, the email will be digitally signed by the sender, and the recipient will confirm the signature.
Process off issuing a digital certificate
There are three parties involved in the creation of a digital certificate: the end user, the registration authority, and the certificate authority. The end user submits a request for a digital certificate to the registration authority (RA), which subsequently assists the certificate authority (CA) in creating the certificate. Registration authorities serve as an intermediary between end-users and certificate authorities. It also assists certificate authorities in their daily operations.
Services of the Registration Authority:
- Accepting and verifying the details of new user’s registration.
- User key generation.
- Backups and recovery of key.
- Certificate cancellation.
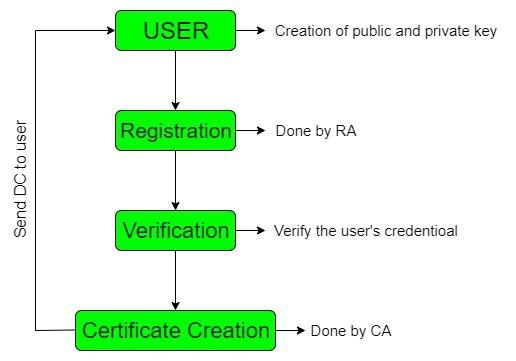
Creation of a Digital Certificate:
Step 1: involves key generation by either the user or the registration authority. The produced public key is transmitted to the registration authority, while the private key is kept secret by the user.
Step 2: The registration authority then registers the user.
Step 3: is the verification performed by the registration authority, in which the user’s credentials are validated. It also verifies whether the user sending the public key has a corresponding private key.
Step 4: At this point, the registration authority sends the information to the certificate authority, which generates the digital certificate, distributes it to the users, and stores a copy for itself.
Digital Signatures vs. Digital Certificates
Consider the following example: Alice wishes to send Bob a digitally signed communication. First, Alice generates a pair of keys, one public and one private. She retains her private key but distributes her public key. Alice composes a message, signs it with her private key, and sends it to Bob. When Bob receives Alice’s digitally signed message, he obtains her public key and uses it to validate Alice’s digital signature. If Bob is able to correctly verify Alice’s digital signature with her public key, he has reason to think that the message was created and delivered by Alice and was not altered in transit. However, there is one significant flaw in the scenario stated above. A cybercriminal can intercept Alice’s digitally signed message and replace it with another message signed with a different private key while revealing the associated public key. When Bob receives what he believes to be Alice’s public key and uses it to verify the message, everything appears to be alright, despite the fact that the original message has been discarded. This lack of authentication is addressed by digital certificates, which not only validate the owner’s identity but also ensure that the owner genuinely has the public key. Alice could simply attach a digital certificate to her message and transmit it both to Bob, who would decode the message using the CA’s public key.
Types of Digital Certificates
On the internet, three types of digital certificates are used to authenticate web servers and web browsers:
1. SSL/TLS certificate:
The server has a TLS/SSL certificate installed so that the information sent between the server and the browser is encrypted. The server can be any kind of server that needs authentication to encrypt and decrypt data, like an LDAP server, a web server, an app server, or a mail server. When a website has a TLS certificate, the URL will start with HTTPS instead of just HTTP. TLS certificates can be single domain, multi-domain, wildcard SSL, or both single domain and multi-domain wildcard SSL. Learn how to register a new domain name.

Single Domain SSL: A single domain SSL only provides strong encryption for a single domain or subdomain. It costs a reasonable amount of money and works well for blogs, forums, and single domain websites. This certificate works for both the www and non-www versions of a website, such as www.domain.com and domain.com.
Multi-Domain SSL: A Multi-Domain SSL certificate, also called a SAN SSL certificate, can be used to secure multiple domains and subdomains at a low cost, and it can be installed on more than one server. The certificate can protect up to 250 different domains (depending on the provider). Here is an example of an SSL certificate for more than one domain.
- www.domain1.com
- blog.domain.com
- smail.domain2.com
- spayment.subdomain1.domain2.com
Wildcard SSL: A Wildcard SSL certificate is best for protecting the first level of subdomains related to a main domain. As per CAB/forum standards, all subdomains will have the same level of encryption (SHA-2). You don’t have to pay anything extra to add as many subdomains as you want to the wildcard SSL certificate. Check out the example of wildcard SSL below.
- *.domain2.com (Primary domain)
- blog.domain2.com (subdomain)
- mail.domain2.com (subdomain)
- payment.domain2.com (subdomain)
- autodiscover.domain2.com (subdomain)
Multi Domain Wildcard SSL: A multi-domain wildcard certificate is the best way to secure different levels of wildcard domains and subdomains, which need to be secure with strong encryption. A single wildcard SSL can protect one main domain and its subdomains, but a multi-domain wildcard can protect different wildcard domains and their subdomains. The example below shows how multi-domain wildcard SSL certificates work, where different levels of domains can secure their subdomains.
- *.domain1.com
- *.subdomain1.domain2.com
- *.a1.subdomain2.domain3.com
- *.a2.subdomain.mydomain.com
2. Code Signing Certificate:
Code Signing Certificate verifies who the publisher is and makes sure the code is correct. There are two types of validation for a code signing certificate: organization validation and extended validation (EV Code Signing certificate). If we talk about the EV Code Signing certificate, then EV Code signing with the help of the Microsoft Smart Screen filter builds the publisher’s reputation. Usually, a developer signs code with a private key, and users use a public key to check the identity of the publisher. Code Signing certificates are not used by many well-known brands.
Comodo Code Sign: A Comodo Code Signing certificate is a branded certificate that verifies the code and lets users know that the code came from the original source. A timestamp will also make sure that your code is always valid, even if the certificate itself is no longer valid. It makes more people want to download software and makes sure that the code can’t be changed because it is signed.
Comodo EV Code Sign: With Microsoft SmartScreen filter technology, the Comodo EV Code Signing certificate builds the reputation of the immediate publisher. Distributors can easily share software code on platforms that are not their own. Comodo carefully checks the existence of a business with third-party sources as well. Download warnings are taken care of by the Comodo EV Code Sign certificate. To prevent hacking, a private key is kept on a separate piece of hardware.
DigiCert Code Signing Certificate: The DigiCert Code Signing certificate can sign code for drivers, software, and applications. The certificate proves that the code has not been changed and came from the original source. DigiCert checks business presence with registered business documents and third-party databases as part of organization validation. Users won’t get a warning that says “Unknown Publisher” when they try to download the software. The code-signing certificate works on more than one platform (Java, Adobe AIR, Office, and VBA, MS Authenticode, Windows phone).
3. Client Certificate
A client certificate is a file that proves to the server that the client is who it says it is. The client certificate doesn’t send or receive any data. A client certificate is also called an email certificate because the person who sends the email signs it, and the person who receives it verifies the digital signature. Under Extended Key Usage details in the browser, the Client Authentication (1.3.6.1.5.5.7.3.2) is shown as the client certificate OID.
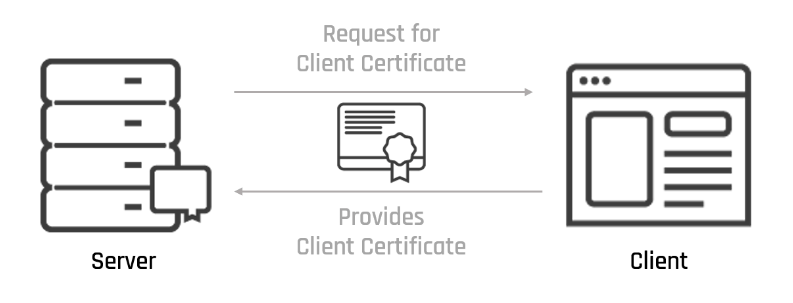
When a user wants to get into a secure database, the user’s client certificate has to go through two-factor authentication.
Who Are Authorized to Issue A Digital Certificate?
Digital certificates are given out by organizations called “certificate authorities.” They will sign the certificates to prove that the organization that asked for the certificate is real and valid. The main job of the certificate authority is to manage the verification of domain control. Certificate authorities are very important to the public key infrastructure process and to keeping the internet safe.
Only authorized CAs, including Symantec, Comodo, GoDaddy, GlobalSign, DigiCert, StartCom, Entrust, Verizon, Trustwave, Secom, Unizeto, Buypass, and others, are permitted to issue any sort of SSL digital certificate.
In addition to SSL digital certificates, there are also client certificates and code signing certificates, which are used to identify one person to another, a person to a device or gateway, or one device to another within a company. Code signing certificates are used to sign software or programmed code that is downloaded over the internet.
A Digital certificate contains:
- Name of certificate holder.
- Serial number used to uniquely identify a certificate, the individual or entity recognized by the certificate, and the certificate itself.
- Expiry date of the digital certificate
- Copy of the public key of the certificate holder.
(Used to read messages and digital signatures that have been encrypted) - Digital Signature of the organization that gave out the certificate.
Along with the digital signature and the message, a digital certificate is also sent.
Digital certificate is also sent with the digital signature and the message.
The Advantages of Using a Digital Certificate
Certificate-based authentication provides numerous advantages that make it a vital component of any modern cybersecurity approach. Among the advantages are:
Integrity: With digital certificates, it is impossible to tamper with the message in transit, either intentionally or unintentionally, because any effort would be detected immediately.
Confidentiality: By allowing two parties to interact privately across a public network, digital certificates address what has arguably become the internet’s largest problem: the fact that it was not developed with privacy in mind.
Identification: Digital certificates clearly identify the communication parties and demonstrate that they are who they claim to be.
Easy to manage: Digital certificates, unlike other authentication techniques, are simple to handle and can be easily exported from a central location to various devices to support multi-user and multi-device situations.
Simple to implement: Because digital certificates do not require any additional hardware, they are simple and inexpensive to implement.
Cost effective: Certificate authorities issue digital certificates. The CA must thoroughly verify a company before issuing a certificate, so hackers can’t fool users. Digital certificates provide encryption at a low cost. Most digital certificates cost $100 or less annually.
Conclusion: By identifying the owner of the public key and making it available to all parties that need to validate it, digital certificates assist overcome the security restrictions of digital signatures. There are various types of digital certificates available today, and they all play a crucial part in any comprehensive cybersecurity plan.
ad



Comments are closed.