What is Traffic Shaping?
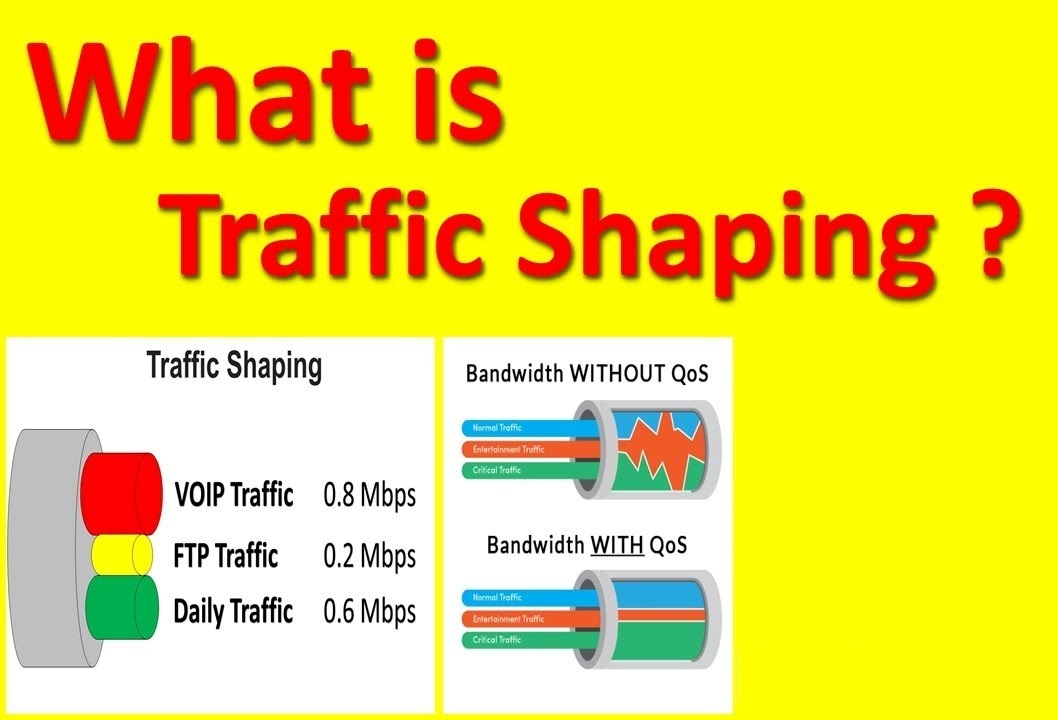
Traffic shaping, also known as packet shaping, involves restricting the bandwidth usage of specific applications to guarantee optimal performance for essential applications.
ad
What is Traffic Shaping?
The implementation of traffic shaping allows organizations to enhance network performance by managing the volume of data entering and leaving the network. Traffic undergoes classification, queuing, and routing based on network policies. In essence, traffic shaping governs the network by slowing down the transmission of packets deemed less critical, ensuring that priority applications experience timely delivery.
Through effective bandwidth management, organizations can safeguard the performance and quality of service for their crucial applications and business-related traffic.
Why is Traffic Shaping Important?
ad
Every network possesses a limited bandwidth, emphasizing the importance of traffic shaping through effective bandwidth management as a crucial tool. This approach ensures the optimal performance of critical applications and the timely delivery of time-sensitive data.
Traffic shaping stands out as a potent and adaptable method to guarantee quality of service and provide defense against distributed denial-of-service (DDoS) attacks that exploit bandwidth. It serves to safeguard networks and applications by mitigating the impact of traffic surges, controlling abusive user behavior, and thwarting attempts to overwhelm network resources through network attacks.
How Does Traffic Shaping Work?
The initial step in establishing an effective traffic shaping system involves classifying the various types of traffic present on the network.
For instance, an organization may prioritize video conferencing traffic to and from its main communication platform to ensure seamless communication, irrespective of network congestion. In such a scenario, other types of traffic might be given lower priority. During these instances, packets are temporarily stored in a buffer until they can be forwarded without exceeding the predetermined and configured rate.
Once the classification system is configured, the traffic shaping device (typically an Application Delivery Controller) takes charge of overseeing the bandwidth entering and leaving the network.
What are the Benefits of Traffic Shaping?
Traffic shaping is instrumental in ensuring the effective functioning of essential business applications and data by securing the necessary bandwidth for them. Ultimately, traffic shaping plays a pivotal role in achieving higher performance, improved Quality of Service (QoS), reduced latency, maximized available bandwidth, and enhanced return on investment (ROI).
Utilizing a network traffic-shaping device or program offers various advantages:
- Enhances network traffic without the need for costly bandwidth expansion.
- Identifies abnormal bandwidth usage to prevent network congestion.
- Blocks the IP addresses of potential attackers.
- Supports compliance with contract service level agreements (SLAs).
- Improves the performance of applications.
- Ensures high transmission quality for critical applications.
- Guarantees end customers receive designated service tiers.
- Aligns with best practices for Internet traffic management.
- Optimizes bandwidth allocation and prioritizes resource consumption for higher-priority applications by limiting unnecessary traffic.
- Meets network firewall requirements.
- Mitigates issues such as jitter, delays, and packet loss caused by excessive network interface traffic, particularly for real-time voice streams.
What are the Challenges and Limitations of Traffic Shaping?
The need for accurate network information and the potential for network security breaches are among the drawbacks associated with traffic shaping. Other disadvantages include:
- Difficulty: Implementation can pose challenges due to technical complexities, especially in large networks with diverse traffic patterns. It requires a comprehensive understanding of network protocols and data flow patterns.
- Infrastructure Cost: Traffic shaping demands sophisticated hardware and software. For small and medium-sized enterprises, these solutions, such as premium routers and advanced network management software, can be relatively expensive.
- Possibility of Inequitable Bandwidth Distribution: Improper handling of traffic shaping can lead to an uneven distribution of bandwidth. This may result in some users or applications having insufficient resources while others receive more bandwidth than necessary.
What are the Traffic Shaping Methods?
Rate Limiting
Relying solely on a threshold is insufficient for controlling the volume of calls or messages within a specific time frame. Fixed or sliding window counters, such as micro-policers for specific interfaces or subscribers, offer alternative options. A fixed window counter divides time into segments, allowing a specific number of messages per interval. If the limit is reached at the beginning of the interval, new messages are discarded. However, if messages are sent toward the end of the interval, they may be processed in the following time slot, potentially leading to traffic peaks.
Leaky Bucket
In traffic shaping, the leaky bucket algorithm gradually releases delayed packets for transmission, offering a more effective solution than outright packet drops, despite potential increases in latency. This algorithm transforms sporadic flows into steady ones, with the critical variables being bucket size and drain rate. The drain, or leak, acts as the system’s regulator, setting the bucket size based on anticipated burst size and the drain rate at the incoming flow’s average rate. Overflowing buckets are either rejected or given lower priority.
Token Bucket
Employed for shaping large amounts of data traffic, the token bucket algorithm is valued for its simplicity and ability to handle aggregated traffic. It’s important to note that specific implementations may use varying terminology, and understanding the fundamental concept differs from comprehending the limitations imposed by actual implementations. Unlike leaky buckets, token buckets allow for varied or bursty flows, lacking policies for priority or disposal. To prevent potential network domination, a Composite Shaper combining a Token Bucket and a Leaky Bucket may be necessary.
Bandwidth Throttling
In traffic shaping, policy rules, data classification, queuing, Quality of Service (QoS), and other techniques ensure adequate network bandwidth for time-sensitive applications. Bandwidth throttling regulates incoming traffic, controlling the outbound flow through rate restriction. Typically measured in bits per second (bps) for traffic shaping, the committed information rate (CIR) buffers any non-essential traffic exceeding the average bit rate.
Packet Prioritization
Traffic shaping focuses on packets leaving the interface, not entering it. As an IP packet exits an interface, the network device uses various techniques to identify its associated application. Based on this information, the interface decides whether to retain or discard packets until a specified bandwidth limit is reached.
Class-Based Shaping (CBQ)
This approach allows network specialists to shape traffic based on classes, enabling configuration on a per-traffic class basis. Class-based shaping supports a hierarchical policy map structure, letting users define average or peak rates for shaping, maximizing available bandwidth. If bandwidth is available, data can surpass the configured rate, allowing for the placement of traffic shaping in a primary policy map and additional QoS features in a secondary policy map.
Hierarchical Token Bucket (HTB)
An effective classful queuing technique, HTB manages various traffic types, permitting excess bandwidth sharing among flows of the same class. HTB enables per-flow bitrate guarantees and prioritization for specific flows, aiming to replace Linux’s CBQ qdisc with a simpler and more logical approach. Both CBQ and HTB enable users to control outbound bandwidth on a particular link, simulating various networks and slower lines with a single physical link.
Weighted Fair Queuing (WFQ)
A flow-based queuing method in QoS, WFQ prioritizes interactive traffic to speed up response times and equitably distributes remaining bandwidth among high-bandwidth flows. WFQ ensures efficient packet transmission for interactive traffic, stabilizing network congestion between different flows. Unlike fair queuing (FQ), WFQ allows schedulers to define the fraction of the link’s capacity for each flow, offering a more flexible and precise approach.
Real-World Examples of Traffic Shaping
Depending on the preferences and objectives of the network administrator, traffic shaping can find application in various network scenarios. Real-world instances of traffic shaping are elucidated below:
- When the need arises to regulate network traffic, traffic shaping proves invaluable. The network might face congestion during peak traffic hours or experience underutilization during off-peak hours, depending on the time of day.
- In the realm of enterprise networks, traffic shaping may be employed to diminish or defer bandwidth for non-essential services such as social media or gaming. Simultaneously, it can allocate greater bandwidth to critical business applications like email or video conferencing.
- An Internet Service Provider (ISP) network can leverage traffic shaping as a tool to govern client bandwidth usage. This involves restricting P2P traffic during busy periods or times of heightened demand.
- Similarly, within a cloud network, traffic shaping may involve blocking or delaying traffic for free or basic customers who pay less or nothing for lower bandwidth and higher latency. In contrast, premium customers, who pay more for increased bandwidth and lower latency, receive prioritized traffic.
- Enhancing customer satisfaction and loyalty, ensuring equitable service quality for all clients, maintaining employee productivity and efficiency, and meeting SLAs or compliance requirements are all outcomes achieved through this strategy.
- Prioritizing VoIP calls for clear audio quality, ensuring smooth video streaming, minimizing latency for online gaming, giving precedence to critical business applications, managing ISP data caps or implementing throttling during peak hours, and adhering to SLAs by prioritizing specific traffic or meeting latency and jitter requirements are illustrative examples of these applications.
- Traffic shaping can be implemented at various points within the network, whether at specific servers or networked devices or at the network gateway where traffic enters or exits.
- To regulate data flow and ensure optimal performance in the context of web hosting, traffic shaping can be implemented at the server level. For instance, in cloud hosting scenarios where resources are distributed across multiple servers, traffic shaping aids in controlling data flow and ensuring seamless operations.
FAQ’s
What is Traffic Shaping?
Traffic shaping, also known as packet shaping, involves restricting the bandwidth usage of specific applications to ensure optimal performance for essential applications.
Why is Traffic Shaping Important?
Traffic shaping is crucial because it allows organizations to manage network performance by controlling the volume of data entering and leaving the network. It ensures optimal performance for critical applications and timely delivery of time-sensitive data.
How Does Traffic Shaping Work?
The process begins with classifying various types of traffic on the network. For example, an organization may prioritize video conferencing traffic to ensure seamless communication, storing other types of traffic in a buffer until it can be forwarded without exceeding the configured rate.
What are the Benefits of Traffic Shaping?
Traffic shaping is instrumental in achieving higher performance, improved Quality of Service (QoS), reduced latency, maximized available bandwidth, and enhanced return on investment (ROI). It also optimizes resource consumption for higher-priority applications and meets network firewall requirements.
What are the Challenges and Limitations of Traffic Shaping?
Challenges include the need for accurate network information, potential security breaches, technical complexities in large networks, and the cost of sophisticated hardware and software. Improper handling may lead to inequitable bandwidth distribution.
What are the Traffic Shaping Methods?
Methods include Rate Limiting, Leaky Bucket, Token Bucket, Bandwidth Throttling, Packet Prioritization, Class-Based Shaping (CBQ), Hierarchical Token Bucket (HTB), and Weighted Fair Queuing (WFQ).
Can Traffic Shaping be Used in Real-World Scenarios?
Absolutely. Real-world examples include regulating network traffic during peak hours, prioritizing bandwidth for critical business applications in enterprise networks, limiting P2P traffic in ISP networks, and blocking or delaying traffic for free users in cloud networks.
Where Can Traffic Shaping be Implemented?
Traffic shaping can be implemented at various points within the network, including specific servers or networked devices and at the network gateway where traffic enters or exits.
How Does Traffic Shaping Improve Customer Satisfaction and Loyalty?
By ensuring fair service quality, prioritizing critical applications, and meeting SLAs, traffic shaping contributes to customer satisfaction, loyalty, and overall positive experiences.
Can Traffic Shaping Help with VoIP and Video Streaming Quality?
Absolutely. Traffic shaping prioritizes VoIP calls for clear audio quality, ensures smooth video streaming, and minimizes latency for online gaming, contributing to an improved user experience.
Conclusion
Traffic shaping stands as a crucial strategy for optimizing network performance in the face of bandwidth limitations. Despite challenges, its benefits, including improved Quality of Service and reduced latency, highlight its significance. Real-world applications demonstrate its adaptability, reaffirming its role in ensuring reliable and efficient network performance. As a vital tool for network administrators, traffic shaping continues to evolve in addressing the complexities of modern data flow.
ad


Comments are closed.