What is a Ping of Death?
The Ping of Death (POD) is a type of denial-of-service (DoS) attack that takes advantage of weaknesses in how Internet Control Message Protocol (ICMP) packets are fragmented. Through the transmission of improperly formatted or excessively large ICMP packets, assailants can induce crashes, freezes, or reboots in the systems of their targets.
ad
How Does a Ping of Death Attack Work?
The Ping of Death attack exploits vulnerabilities in the ICMP protocol and IP fragmentation. Here’s a concise breakdown of its operation:
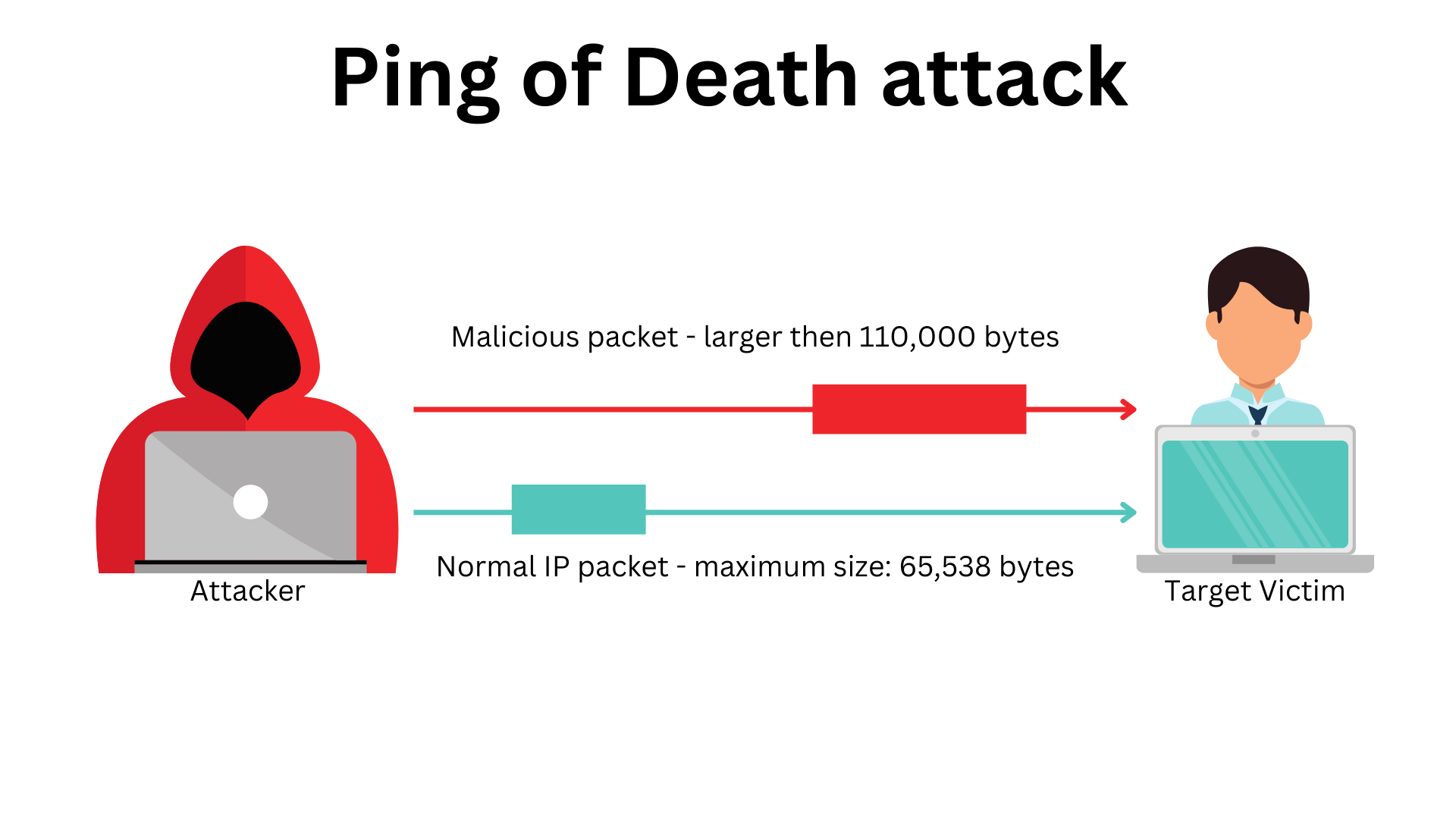
- The attacker dispatches an ICMP (ping) packet surpassing the maximum size limit of 65,535 bytes.
- Prior to transmission, the attacker’s system divides this oversized packet into smaller fragments.
- Upon reception, the targeted system endeavors to reconstruct these fragments into the original, larger packet.
- However, the reassembly process fails due to the packet exceeding the maximum allowable size, leading to system crashes or freezes.
Critical to this attack is the absence of size information in fragmented packets, leaving the receiving system unaware of potential size breaches until too late.
ad
This method can be executed using easily accessible tools and can affect a range of operating systems and devices, including routers, firewalls, and servers. Vulnerability levels vary among systems depending on their packet reassembly handling mechanisms.
History and Discovery of the Ping of Death
The Ping of Death was first presented in 1996 by a group of security researchers. It gained widespread notoriety when it was used to crash machines running Windows 95 and Windows NT operating systems.
At the time, it also affected many router and firewall vendors. The Ping of Death highlighted inherent weaknesses in the TCP/IP suite’s handling of fragmented packets.
After its discovery, the Ping of Death vector was widely shared online and became exploited by attackers to take down victims’ systems. It exemplified the rising threat that denial-of-service and similar attacks posed in the late 1990s as Internet adoption began to grow rapidly.
Preventing Ping of Death Attacks
There exist several strategies to prevent or lessen the impact of Ping of Death attacks:
- Patching Systems: Manufacturers have issued patches for operating systems and network devices, enhancing packet reassembly and fragmentation management. Consistently updating and patching systems remains among the most effective defenses.
- Firewall ICMP Blocking: Network perimeter firewalls can be configured to halt all incoming ICMP packets, thus obstructing pings from reaching vulnerable systems. However, this approach may also impede legitimate diagnostic pings.
- Minimize Fragmentation: Modifying the Maximum Transmission Unit (MTU) on networks can diminish the necessity for fragmentation. Attackers depend on fragmentation to obscure packet sizes.
- Intrusion Detection Systems (IDS): Network and host-based IDS can identify abnormal fragmentation patterns and thwart oversized ICMP packets. Customized signatures enable the detection of Ping of Death and other fragmentation-based exploits.
- Packet Size Validation: Conducting checks on packet sizes during reassembly can forestall buffer overflow or errors when fragments surpass predetermined limits. Discarding oversized packets helps mitigate the risk.
Ping of Death in Cloud Environments
With the widespread integration of cloud computing and virtualization, the Ping of Death has evolved into a threat vector within these environments.
- Targeting Hypervisors: Malicious actors can aim at the virtualization hypervisor, responsible for managing guest virtual machines (VMs), by sending malformed pings to its management interfaces. This could result in DoS scenarios affecting multiple hosted VMs.
- Cross-VM Attacks: Crafted ping packets can breach VM isolation boundaries, affecting neighboring VMs hosted on a compromised hypervisor.
- Cloud Instance Flooding: Instances or containers in the cloud equipped with public IP addresses may be inundated with high volumes of Ping of Death payloads, depleting resources.
- Cloud Network Saturation: Cloud-based network infrastructure components, such as load balancers, can face bandwidth saturation due to the influx of large ping packets, leading to high traffic volumes.
FAQ’s
What is the Ping of Death (POD) attack and how does it work?
The Ping of Death is a type of denial-of-service (DoS) attack exploiting vulnerabilities in how Internet Control Message Protocol (ICMP) packets are fragmented. Attackers send improperly formatted or oversized ICMP packets, causing system crashes, freezes, or reboots in their targets.
What is the history behind the Ping of Death attack?
The Ping of Death was first introduced in 1996 by security researchers and gained notoriety for its ability to crash machines running Windows 95 and Windows NT. It exposed weaknesses in the TCP/IP suite’s handling of fragmented packets and became widely exploited by attackers, highlighting the growing threat of denial-of-service attacks in the late 1990s.
How can Ping of Death attacks be prevented?
Several prevention strategies include patching systems with updated software to enhance packet reassembly and fragmentation management, configuring network firewalls to block incoming ICMP packets, minimizing fragmentation by adjusting the Maximum Transmission Unit (MTU), employing Intrusion Detection Systems (IDS) to detect abnormal fragmentation patterns, and validating packet sizes during reassembly to mitigate risks.
How has the Ping of Death evolved in cloud environments?
In cloud environments, the Ping of Death has adapted to target hypervisors, enabling attackers to disrupt multiple hosted virtual machines (VMs). Additionally, cross-VM attacks exploit VM isolation boundaries, while cloud instances may be flooded with Ping of Death payloads, depleting resources. Cloud network saturation can also occur due to high volumes of large ping packets targeting infrastructure components like load balancers.
What makes the Ping of Death particularly dangerous in modern networks?
The Ping of Death remains a significant threat due to its ability to exploit fundamental weaknesses in network protocols and infrastructure components. With the proliferation of cloud computing and virtualization, attackers have found new vectors to execute these attacks, posing serious risks to both traditional and cloud-based systems.
Conclusion
The Ping of Death (POD) attack, born in the late 1990s, remains a persistent threat in today’s network landscape, particularly in cloud environments. As it exploits weaknesses in ICMP packets and IP fragmentation, its danger persists despite cybersecurity advancements. Organizations must remain vigilant, employing robust defenses like patching, firewall configurations, and intrusion detection. Collaboration and ongoing research are crucial to stay ahead of evolving threats and safeguard critical network infrastructure.
ad


Comments are closed.