What is a Perimeter Firewall?
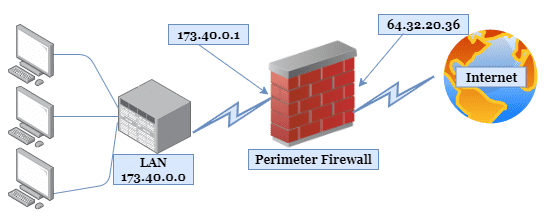
A perimeter firewall acts as the barrier between a private network and the public Internet. It monitors and controls all traffic entering and leaving the private network. This firewall plays a crucial role in enabling organizations to restrict access to internal systems, block malicious content from entering the network, and prevent unauthorized use of corporate systems and data exfiltration.
ad
How Does a Perimeter Firewall Work?
A perimeter firewall is situated at the boundary of a private network, preventing malicious traffic from breaching that boundary. It may belong to various types, including:
- Packet Filtering: These firewalls are the simplest, scrutinizing network packets and permitting or denying them based on access control lists (ACLs). They can restrict specific traffic types based on source and destination ports.
- Static Packet Filtering: Static packet filtering involves filtering traffic based on packet header addressing information. Larger organizations often use this method to block access to prohibited websites, such as social media sites.
- Stateful Firewalls: These firewalls monitor the state of network connections, using this data for access decisions. Unlike packet filtering firewalls, they can detect ACK scans by noticing out-of-sequence ACK packets.
- Stateful Inspection: Stateful inspection, a widely used firewall technique, maintains records of outgoing traffic and permits only the traffic that matches an initial request to return. This approach effectively prevents IP spoofing and network scanning attempts originating from external networks.
- Proxy Firewalls: Acting as intermediaries for user connections, proxy firewalls establish separate connections between users and the firewall, and between servers and the firewall. This helps safeguard users’ privacy by hiding their IP addresses.
- Next-Generation Firewalls (NGFWs): NGFWs merge packet filtering and stateful firewall features with additional security capabilities. They conduct deep packet inspection (DPI) and can include intrusion detection/prevention systems, URL filtering, and antivirus and antimalware functions.
Components of the Network Perimeter
ad
A perimeter firewall is a crucial component of the network perimeter, which comprises the following essential elements:
- Border Router: Positioned at the boundary where a private network meets the public Internet, the border router serves as the final router under an organization’s control. It physically connects both internal and external networks.
- Perimeter Firewall: Located behind the border router, the perimeter firewall acts as the initial defense against external threats for an organization. It screens and filters out malicious traffic before it can breach the private network.
- Intrusion Detection/Prevention System (IDS/IPS): An intrusion detection system (IDS) passively monitors network activities, generating alerts upon detecting potential threats. In contrast, an intrusion prevention system (IPS) actively blocks malicious traffic to provide proactive protection.
- Demilitarized Zone (DMZ): Positioned between the public and private networks, a DMZ is a designated network segment. It hosts publicly-accessible services like web and email servers while ensuring the isolation of the private network from potential external threats.
Security Requirements of a Perimeter Firewall
A perimeter firewall is tasked with safeguarding an organization and its users through the following functionalities:
- Web, Application, and Data Controls: It ensures users access trusted and untrusted resources safely, guarding against web-based attacks, exploits, and threats to corporate data.
- Advanced Threat Prevention: Capable of detecting and thwarting known and unknown threats, the firewall must possess Next-Generation Firewall (NGFW) features with threat intelligence and sandbox analysis capabilities.
Network Requirements of a Perimeter Firewall
A perimeter firewall serves as both a networking appliance and a security measure. It must fulfill several key network requirements:
- Redundancy: Given that all traffic flows through the perimeter firewall, any downtime could disrupt connectivity or compromise security. Therefore, it should be redundant to ensure continued operation even if a component fails.
- Performance: As the gateway for all inbound and outbound traffic, the firewall’s efficiency and speed significantly affect organizational operations. It must be capable of inspecting traffic at line speed to minimize latency.
- Network Interfaces and Port Capacity: Directly linked to both the public Internet and the private network, the perimeter firewall requires sufficient network interfaces and port capacity to support these connections and the associated traffic.
Benefits and Limitations of Strong Perimeter Firewall Security
A perimeter firewall delineates and upholds the separation between a public and private network. While perimeter firewalls offer advantages, they also come with limitations concerning an organization’s overall security stance.
Benefits of Strong Perimeter Firewall
Here are some of the advantages offered by a perimeter firewall:
- Network Traffic Visibility: Perimeter firewalls possess visibility into all traffic traversing the private network, aiding corporate security efforts and furnishing valuable insights into the utilization of internal and external services.
- Malicious Content Filtering: Utilizing a Next-Generation Firewall (NGFW) as a perimeter defense allows for the detection and prevention of malware and other malicious attacks from infiltrating an organization’s network.
- Enhanced User Privacy: By serving as an intermediary between internal users and external servers, perimeter firewalls can bolster user privacy.
- Data Loss Prevention: Perimeter firewalls aid in preventing the loss of sensitive data by identifying and blocking traffic that contravenes company policies.
- Stop Keyloggers: Keyloggers are a type of spyware designed to capture keystrokes with the aim of stealing critical information, including PIN codes and account passwords.
Limitations of Strong Perimeter Firewall
While perimeter firewalls offer advantages, they are not flawless solutions. Some of their limitations include:
- Limited to North-South Traffic Visibility: Perimeter firewalls solely scrutinize traffic passing through them, encompassing inbound and outbound traffic. East-west traffic within the secured network circumvents the perimeter and remains uninspected.
- Lack of Insider Threat Management: While perimeter firewalls thwart external threats from breaching the corporate network, they are unable to detect insider threats already inside the protected perimeter.
- Blind to Infected Mobile Devices: Perimeter firewalls can only identify malware entering the private network via network channels. Infected mobile devices connecting externally before accessing the private network bypass perimeter defenses.
FAQ’s
What is a perimeter firewall and how does it work?
A perimeter firewall serves as the barrier between a private network and the public Internet. It monitors and controls all traffic entering and leaving the private network. This firewall filters out malicious traffic and helps prevent unauthorized access to internal systems.
What are the different types of perimeter firewalls?
Perimeter firewalls come in various types, including packet filtering, static packet filtering, stateful firewalls, stateful inspection, proxy firewalls, and Next-Generation Firewalls (NGFWs). Each type offers different levels of security and functionality.
What components make up the network perimeter alongside a perimeter firewall?
The network perimeter includes components like the border router, intrusion detection/prevention systems (IDS/IPS), and a demilitarized zone (DMZ). These elements work together with the perimeter firewall to protect the private network from external threats.
What security requirements should a perimeter firewall meet?
A perimeter firewall should provide web, application, and data controls to ensure safe access to internal and external resources. It should also offer advanced threat prevention capabilities to detect and block both known and unknown threats effectively.
How can a perimeter firewall enhance network security?
A perimeter firewall enhances network security by providing visibility into all traffic passing through the private network, filtering out malicious content, protecting user privacy, and preventing data loss.
What are the limitations of perimeter firewalls?
Perimeter firewalls have limitations such as being limited to North-South traffic visibility, lacking insider threat management capabilities, and being blind to infected mobile devices that connect externally before accessing the private network.
How can organizations mitigate the limitations of perimeter firewalls?
Organizations can mitigate the limitations of perimeter firewalls by implementing additional security measures such as internal network monitoring for insider threats and deploying endpoint security solutions to detect and protect against malware on mobile devices.
Conclusion
Perimeter firewalls are crucial for network security, acting as the first line of defense against external threats. While they offer benefits like enhanced visibility and malware filtering, they also have limitations such as restricted visibility into internal traffic and blind spots for certain threats. To strengthen overall security, organizations must combine perimeter firewalls with additional measures tailored to address specific vulnerabilities and threats. This holistic approach ensures better protection against evolving cyber threats.
ad


Comments are closed.