What Is a Man in the Middle Attack (MITM)?
There are various types of security threats that attackers can utilize to exploit insecure applications. Some of these attacks can be carried out using automated software, while others require more direct involvement from attackers. This tutorial will explain the basic concept of a man-in-the-middle (MITM) attack, along with providing examples and techniques for mitigation.
ad
What is a Man-in-the-Middle Attack?
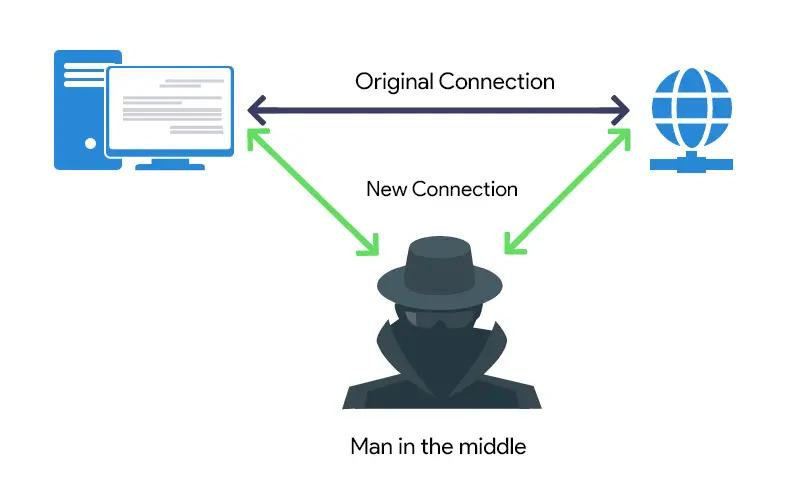
A man-in-the-middle (MITM) attack is a type of cyberattack where criminals exploit weak web-based protocols to interpose themselves between entities in a communication channel, allowing them to steal data.
In such attacks, none of the parties engaged in email, texting, or video calls are aware that an attacker has infiltrated the conversation and is actively stealing their data.
While many cyberattacks occur discreetly and without the victims’ awareness, certain MITM attacks involve more overt tactics. These may involve a bot generating convincing text messages, mimicking a person’s voice during a call, or spoofing an entire communications system to extract data that the attacker deems valuable from participants’ devices.
ad
Types Of Industries And Personas That Are Most Vulnerable To MITM Attacks
MITM attacks can target any entity, be it a business, organization, or individual, if cyber criminals perceive an opportunity for financial gain. The likelihood of an attack increases with the potential financial rewards.
On the dark web, stolen personal financial or health information may fetch only a few dollars per record. However, considering that a single data breach can compromise millions of records, the cumulative profit can be substantial.
Industries commonly targeted by MITM attacks include banks and their associated applications, financial institutions, healthcare systems, and businesses utilizing Internet of Things (IoT) devices in industrial networks. These vulnerable devices are widespread in manufacturing, industrial processes, power systems, critical infrastructure, and other sectors.
According to reports from SCORE and the SBA, small and midsize businesses are at a higher risk, with 43% of all cyberattacks targeting SMBs due to their lack of robust security measures.
Types of Man-in-the Middle (MITM) Attacks
Email Hijacking
In this type of cyberattack, known as email hijacking, cyber criminals seize control of the email accounts belonging to banks, financial institutions, or other trusted entities that handle sensitive data and finances. Once infiltrated, attackers can monitor transactions and communications between the institution and its clients.
In more sinister scenarios, attackers impersonate the bank’s email address and dispatch fraudulent emails to customers, urging them to divulge their credentials—or worse, transfer funds—to an account under the attackers’ control. Social engineering, or the cultivation of trust with victims, often plays a pivotal role in the success of this MITM attack variant.
Wi-Fi Eavesdropping
In Wi-Fi eavesdropping, cyber criminals entice victims to connect to a nearby wireless network with an authentic-sounding name. However, the network is actually configured to engage in malicious activities. It may masquerade as a network belonging to a nearby frequented business or adopt a seemingly innocuous name like “Free Public Wi-Fi Network.” In some instances, no password is required for connection.
Once connected to the malevolent Wi-Fi network, attackers have multiple options: they can monitor the user’s online activities or harvest login credentials, credit card details, and other sensitive data.
To safeguard against such attacks, users should always verify the network they are connecting to and disable the Wi-Fi auto-connect feature on their mobile devices when moving around locally, preventing automatic connection to malicious networks.
DNS Spoofing
DNS spoofing, also known as DNS cache poisoning, occurs when manipulated DNS records redirect legitimate online traffic to a counterfeit or spoofed website designed to mimic a site the user is likely familiar with and trusts.
Similar to other spoofing techniques, attackers coax users into unwittingly logging into the fake website, persuading them to take specific actions such as making payments or transferring funds to designated accounts. In the process, attackers pilfer as much data as possible from their victims.
Session Hijacking
Session hijacking, a variant of MITM attack, involves attackers waiting for victims to log into an application, such as banking or email services, and then pilfering the session cookie. Subsequently, attackers utilize the stolen cookie to access the victim’s account from their own browser.
Sessions, which denote temporary data exchanges between devices or between a computer and a user, are exploited by attackers as they identify logged-in users on websites. However, attackers must act swiftly, as sessions expire after a predetermined period, which could be as brief as a few minutes.
Secure Sockets Layer (SSL) Hijacking
Most contemporary websites indicate their use of a secure server by displaying “HTTPS” instead of “HTTP” in the URL’s initial segment in the browser’s address bar. This denotes the adoption of Hypertext Transfer Protocol Secure (HTTPS), a standard security protocol safeguarding all data exchanged with the secure server.
SSL and its successor, Transport Layer Security (TLS), establish security between networked computers. In an SSL hijacking, attackers intercept all data transmitted between a server and the user’s computer, exploiting vulnerabilities in the SSL protocol, which was deprecated in June 2015 due to its susceptibility.
ARP Cache Poisoning
The Address Resolution Protocol (ARP) is a communication protocol essential for discovering the link layer address, such as a media access control (MAC) address, associated with a given Internet Protocol (IP) address on a local network.
In ARP cache poisoning, cyber criminals deceive the victim’s computer with false information, tricking it into recognizing the attacker’s computer as the network gateway. Consequently, the victim’s computer unwittingly directs all its network traffic to the malicious actor instead of the legitimate network gateway. The attacker then analyzes and pilfers the diverted traffic, acquiring valuable information such as personally identifiable information (PII) stored in the victim’s browser.
IP Spoofing
IP spoofing, akin to DNS spoofing, involves redirecting internet traffic intended for a legitimate website to a fraudulent site. However, instead of spoofing the website’s DNS record, the attacker modifies the malicious site’s IP address to mimic the IP address of the intended legitimate website users aimed to visit.
Stealing Browser Cookies
A browser cookie, also known as an HTTP cookie, is a small piece of stored information collected by a web browser and stored locally on a user’s device. These cookies assist websites in remembering information to enhance the browsing experience.
To execute cookie theft, cyber criminals typically combine it with another MITM attack technique, such as Wi-Fi eavesdropping or session hijacking. By gaining access to a user’s device using one of these methods, attackers can pilfer browser cookies, granting them access to passwords, credit card details, and other sensitive information stored in the user’s browser.
📚 Also Read: What Is a Browser-in-the-Browser (BitB) Attack?
How Does a Man-in-the-Middle (MITM) Attack Work?
Irrespective of the particular techniques or combination of technologies required for a MITM attack, the fundamental sequence of actions remains consistent:
- Person A sends a message to Person B.
- The MITM attacker secretly intercepts the message, unbeknownst to Person A or Person B.
- The MITM attacker alters the message content or deletes the message entirely, again, without the knowledge of Person A or Person B.
In computing contexts, a MITM attack operates by exploiting weaknesses in network, web, or browser-based security protocols to redirect genuine traffic and pilfer information from unsuspecting victims.
Examples of Man-In-The-Middle attacks
In 2013, Edward Snowden disclosed documents he acquired during his tenure as a consultant at the National Security Agency (NSA). These documents revealed that the NSA masqueraded as Google, intercepting all traffic with the capability to forge SSL encryption certification. Utilizing this MITM attack, the NSA accessed the search records of all Google users, including American citizens, constituting illegal domestic surveillance of U.S. residents.
Internet Service Provider Comcast employed JavaScript to substitute its ads for those from third-party websites, a form of MITM attack known as code injection. By manipulating web traffic passing through their system, Comcast could inject code and replace all ads with their own or insert ads into content originally ad-free.
Equifax, one of the three major credit reporting agencies, experienced a MITM data breach in 2017, exposing the financial data of over 100 million customers to criminals over several months.
A vulnerability in a banking application used by HSBC, NatWest, Co-op, Santander, and Allied Irish Bank enabled criminals to pilfer personal information and credentials, including passwords and PIN codes.
MITM attacks have played a significant role in major data breaches. Notable breaches in 2021 included those at Cognyte (five billion records), Twitch (five billion records), LinkedIn (700 million records), and Facebook (553 million records).
MITM issues in mobile apps
Every mobile device user faces the risk of being targeted. Numerous apps neglect to implement certificate pinning, a security measure that binds the SSL encryption certificate to the correct destination hostname. Establishing this linkage requires proactive inclusion during application development, employing established, valid pinning relationships. Once a malicious proxy is in operation, it becomes impossible to implement certificate pinning retroactively, as the proxy will substitute the SSL certificate with a counterfeit one.
A proxy intervenes in the data transmission between the sender and receiver. In the case of a malicious proxy, it alters the data without detection by either the sender or receiver, perpetrating its actions covertly.
How to detect a Man-in-the Middle (MITM) attack?
While MITM attacks may initially appear conspicuous due to their reliance on tactics akin to other cyber threats like phishing or spoofing—activities that employees and users may have received training to identify and counter—detection requires a comprehensive approach encompassing both human and technical protocols, given the increasing sophistication of cyber criminals. As with all cybersecurity challenges, proactive prevention is paramount.
The following indicators may signal the presence of malicious eavesdropping on your network and the occurrence of a MITM attack:
- Unusual Disconnections: Unexpected or recurrent disconnections from a service, resulting in users being abruptly logged out and required to reauthenticate repeatedly, often signify a MITM attempt or attack. Cyber criminals exploit such opportunities to harvest usernames and passwords. While users may perceive this inconvenience as minor, MITM attackers rely on this repeated action for success.
- Suspicious URLs: In spoofing schemes, cyber criminals fabricate counterfeit websites mirroring recognizable, trusted ones to entice victims into disclosing their credentials. In the MITM variant, the webpage presented to users in their browser is a spoofed site, and the URL displayed in the address bar conspicuously deviates from the legitimate address of the trusted site or application. MITM attackers employ DNS hijacking to redirect users to the spoofed site, enabling the interception of messages and collection of data. Users engaging in personal financial transactions should meticulously scrutinize their financial institution’s webpages for any unfamiliar elements.
- Public, Unsecured Wi-Fi: Users should exercise caution when accessing public Wi-Fi networks provided by unfamiliar establishments. This caution does not extend to municipal Wi-Fi, which municipalities offer for residents’ internet connectivity. Even if users refrain from conducting banking transactions or other activities involving sensitive data on public Wi-Fi networks, a MITM attack can still deliver malicious code to intercept chats and messages. Cyber criminals often disguise their malicious networks with innocuous names like “Local Free Wireless,” enticing unsuspecting users. Despite offering ostensibly free connectivity, attackers surveil all user activity on these networks.
How to Prevent Man-in-the-Middle Attacks?
Implementing robust cybersecurity measures generally serves as a defense against MITM attacks.
- Update and secure home Wi-Fi routers: Regularly updating firmware and configuring security settings to the strongest level, currently WPA3, is crucial, especially with the prevalence of work-from-home policies.
- Use a virtual private network (VPN): VPNs encrypt data transmission between devices and the VPN server, making it difficult for attackers to manipulate.
- Enable end-to-end encryption: Encourage the use of encryption for emails and communications, and opt for applications that offer built-in encryption features like WhatsApp Messenger.
- Install patches and antivirus software: Consistently updating devices with patches and using antivirus software is essential for endpoint security.
- Employ strong passwords and a password manager: Encourage the use of strong passwords and password managers, along with implementing mobile device management software for enforcing password policies.
- Implement multi-factor authentication (MFA): MFA adds an extra layer of security beyond passwords, reducing reliance solely on passwords.
- Connect only to secure websites: Verify website security by checking for the padlock icon and using HTTPS protocol. Employ web filtering protocols to restrict access to non-HTTPS sites.
- Encrypt DNS traffic: Utilize DNS encryption mechanisms like DNS over TLS (DoT) and DNS queries over HTTPS to secure DNS traffic and authenticate external DNS resolvers.
- Adopt the zero-trust philosophy: Implement a zero-trust approach that requires continuous verification of devices, users, and applications before granting access, reducing the risk of MITM attacks.
- Deploy a UEBA solution: Utilize User and Entity Behavior Analytics (UEBA) solutions, to detect anomalies in user and device behavior, leveraging machine learning to identify potential MITM attacks and respond in real-time.
FAQ’s
Q: What exactly is a Man-in-the-Middle (MITM) Attack?
A: A MITM attack is a type of cyberattack where criminals exploit vulnerabilities in web-based protocols to position themselves between communicating entities. This allows them to intercept and steal data transmitted between the parties.
Who are the most vulnerable targets of MITM attacks?
A: MITM attacks can target any entity, including businesses, organizations, or individuals, especially those involved in financial transactions or handling sensitive data. Small and midsize businesses are particularly at risk due to their often less robust security measures.
What are some common types of MITM attacks?
Some common types of MITM attacks include email hijacking, Wi-Fi eavesdropping, DNS spoofing, session hijacking, SSL hijacking, ARP cache poisoning, IP spoofing, and stealing browser cookies.
How do MITM attacks work?
In a MITM attack, the attacker secretly intercepts communication between two parties, alters the message content, or even deletes messages altogether without the knowledge of the communicating entities.
What are some real-life examples of MITM attacks?
Notable examples include the NSA’s interception of Google’s traffic to access user search records, Comcast’s insertion of ads into web traffic, Equifax’s data breach compromising millions of customers’ financial data, and various banking app vulnerabilities exploited by cybercriminals.
How can individuals and organizations detect MITM attacks?
Indicators of a MITM attack include unusual disconnections from services, suspicious URLs, and the use of public, unsecured Wi-Fi networks. However, detecting these attacks often requires a comprehensive approach combining human vigilance and technical protocols.
What can be done to prevent MITM attacks?
Implementing robust cybersecurity measures such as updating Wi-Fi routers, using VPNs, enabling end-to-end encryption, installing patches and antivirus software, employing strong passwords and multi-factor authentication, connecting only to secure websites, encrypting DNS traffic, adopting a zero-trust philosophy, and deploying UEBA solutions can help prevent MITM attacks.
Conclusion
Man-in-the-Middle (MITM) attacks present serious threats to individuals and organizations, exploiting vulnerabilities in web-based protocols to intercept and manipulate communication for data theft. Detecting and preventing these attacks requires a comprehensive approach, combining human vigilance with technological safeguards. By implementing robust cybersecurity measures, such as updating Wi-Fi routers, using VPNs, and deploying advanced security solutions, individuals and organizations can mitigate the risks posed by MITM attacks and protect against cyber threats in the digital age.
ad


Comments are closed.