What is cross-site scripting (XSS) and how to prevent it?
In the dynamic landscape of web security, the threat of cross-site scripting (XSS) looms prominently as a potential exploit that can compromise the integrity of web applications. XSS vulnerabilities empower attackers to manipulate user interactions, leading to unauthorized access, data compromise, and potential control over the entire application. This article navigates through the intricacies of XSS, exploring its types, impacts, prevention strategies, and testing methodologies. From understanding the fundamental mechanisms to practical insights on mitigation, the discourse aims to equip readers with the knowledge necessary to fortify their web applications against XSS threats.
ad
What is cross-site scripting (XSS)?
Cross-site scripting (XSS), a web security vulnerability, enables attackers to jeopardize user interactions with a vulnerable application. It permits the attacker to bypass the same origin policy, intended to isolate various websites. Typically, cross-site scripting vulnerabilities empower attackers to impersonate a victim user, execute actions within the user’s capabilities, and retrieve the user’s data. If the victim user holds privileged access in the application, the attacker could potentially attain complete control over all functionality and data within the application.
How does XSS work?
The functioning of cross-site scripting involves manipulating a susceptible website to deliver malicious JavaScript to users. Once the malicious code runs in a victim’s browser, the attacker gains the ability to fully compromise the user’s interaction with the application.
ad
What are the types of XSS attacks?
There exist three primary categories of XSS attacks:
- Reflected XSS, wherein the malicious script originates from the current HTTP request.
- Stored XSS, wherein the malicious script originates from the website’s database.
- DOM-based XSS, wherein the vulnerability resides in client-side code rather than server-side code.
1. Reflected cross-site scripting
Reflected XSS is the simplest form of cross-site scripting, occurring when an application takes data from an HTTP request and includes it in the immediate response in an insecure manner.
Consider the following example of a reflected XSS vulnerability:
Original URL:
https://example-website.com/search?term=userInput
<p>Search results for userInput</p>
An attacker can exploit this by crafting an attack as follows:
Crafted URL:
https://example-website.com/search?term=<script>/* Malicious code here… */</script>
<p>Search results for <script>/* Malicious code here… */</script></p>
As the application doesn’t perform additional processing of the data, when the user opens the URL crafted by the attacker, the script executes in the user’s browser within the context of their session with the application. Consequently, the script can carry out any action and retrieve any data accessible to the user.
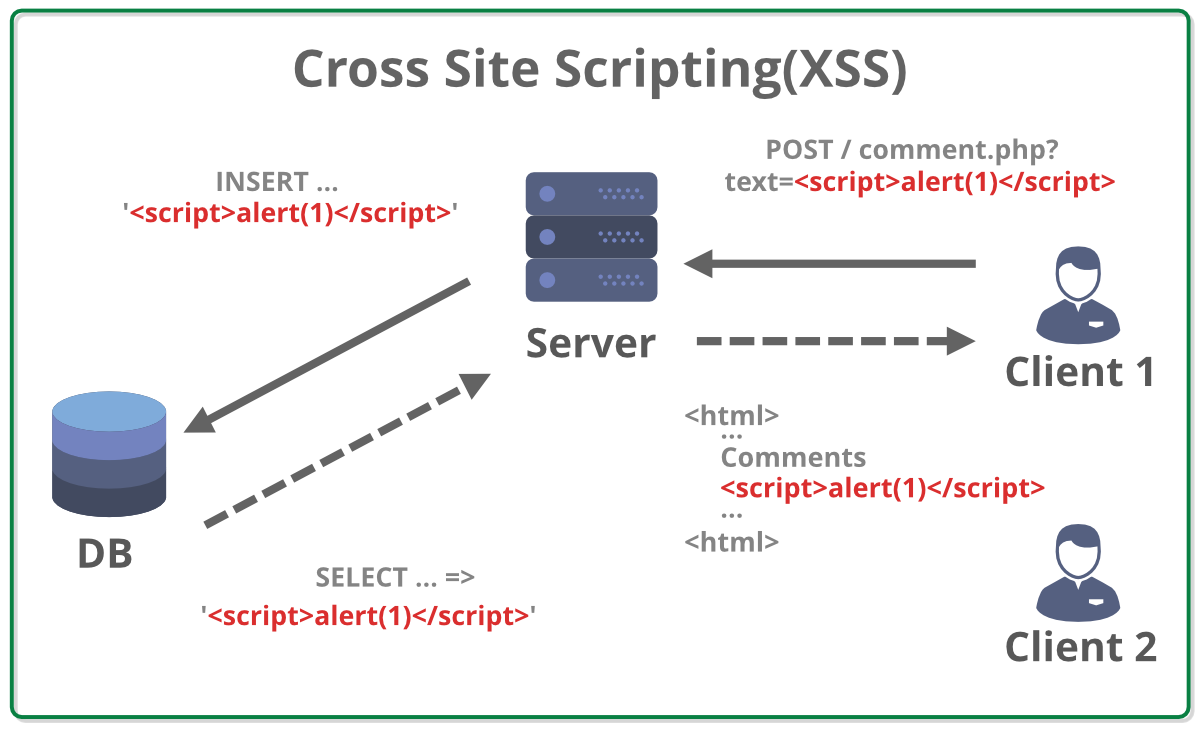
2. Stored cross-site scripting
Stored XSS, also known as persistent or second-order XSS, occurs when an application accepts data from an untrusted source and incorporates that data into subsequent HTTP responses in an insecure manner.
The susceptible data could be introduced to the application through various avenues, such as user input in HTTP requests (e.g., comments on a blog post, user profiles in a social network, or product reviews). Alternatively, the data may originate from other untrusted sources, like an email application displaying messages received over POP3, a ticketing system showcasing user-submitted issues, or a healthcare app displaying patient records.
Consider the following example of a stored XSS vulnerability in a comment section where users can submit comments:
Original Comment:
<div>This is an interesting post!</div>
Given that the application doesn’t perform additional processing of the data, an attacker can exploit this by submitting a comment containing malicious code:
<div><script>/* Malicious code here… */</script></div>
In this scenario, the attacker’s script becomes part of the stored data and is executed when other users access the comment, potentially compromising their interactions with the application.
3. DOM-based cross-site scripting
DOM-based XSS, also known as DOM XSS, occurs when an application incorporates client-side JavaScript that processes data from an untrusted source in an insecure manner, usually by directly writing the data back to the DOM.
Consider the following example, where an application employs JavaScript to extract the value from an input field and then inserts that value into an HTML element:
var username = document.getElementById(‘username’).value;
var greeting = document.getElementById(‘greeting’);
greeting.innerHTML = ‘Welcome, ‘ + username + ‘!’;
If the attacker can manipulate the value of the input field, they can easily construct a malicious value that triggers the execution of their own script:
Welcome, <img src=1 onerror=’/* Malicious code here… */’>!
Typically, the input field might be populated from a part of the HTTP request, such as a URL query string parameter, providing the attacker with the opportunity to launch an attack using a malicious URL, akin to the approach in reflected XSS.
What can XSS be used for?
An attacker exploiting a cross-site scripting vulnerability typically possesses the ability to:
- Impersonate or masquerade as the victim user.
- Execute any action within the user’s capabilities.
- Access any data available to the user.
- Capture the user’s login credentials.
- Virtually deface the website.
- Introduce trojan functionality into the website.
Impact of XSS vulnerabilities
The specific consequences of an XSS attack typically hinge on the characteristics of the application, including its functionality and data, as well as the compromised user’s status. For instance:
- In a brochureware application where all users are anonymous, and information is entirely public, the impact is likely to be minimal.
- In an application that houses sensitive data like banking transactions, emails, or healthcare records, the impact is usually significant.
- If the compromised user holds elevated privileges within the application, the impact is generally critical. This situation allows the attacker to attain complete control over the vulnerable application, compromising all users and their associated data.
How to find and test for XSS vulnerabilities
Burp Suite’s web vulnerability scanner is highly effective in quickly and reliably identifying the majority of XSS vulnerabilities.
Manual testing for reflected and stored XSS typically involves submitting simple unique input (such as a concise alphanumeric string) into every entry point within the application. The process includes identifying every instance where the submitted input is reflected in HTTP responses and individually testing each location to ascertain whether carefully crafted input can execute arbitrary JavaScript. This method aids in understanding the context of the XSS occurrence and selecting an appropriate payload for exploitation.
In the case of manually testing for DOM-based XSS stemming from URL parameters, a similar process is followed. It entails inserting simple unique input into the parameter, using the browser’s developer tools to inspect the DOM for this input, and testing each location to determine exploitability. However, detecting other types of DOM XSS, particularly those in non-URL-based input (such as document.cookie) or non-HTML-based sinks (like setTimeout), requires a thorough review of JavaScript code, which can be a time-intensive task. Burp Suite’s web vulnerability scanner integrates static and dynamic analysis of JavaScript, offering an automated and reliable approach to detecting DOM-based vulnerabilities.
Content security policy
Content Security Policy (CSP) is a browser mechanism designed to reduce the impact of cross-site scripting and certain other vulnerabilities. In cases where an application utilizing CSP exhibits behavior similar to cross-site scripting, the CSP may impede or block the exploitation of the vulnerability. However, it is common for the CSP to be bypassed, allowing for the exploitation of the underlying vulnerability.
Dangling markup injection
Dangling markup injection is a method used to capture cross-domain data when a complete cross-site scripting exploit is unfeasible, often due to input filters or other defensive measures. This technique is frequently utilized to seize sensitive information visible to other users, including CSRF tokens that could facilitate unauthorized actions on behalf of the user.
How to prevent XSS attacks
Preventing cross-site scripting varies in difficulty, with some cases being straightforward and others posing greater challenges depending on the application’s complexity and its handling of user-controllable data.
In general, effectively mitigating XSS vulnerabilities typically involves a combination of the following measures:
- Filter Input on Arrival: Apply strict filtering at the point where user input is received, focusing on expected or valid input.
- Encode Data on Output: When presenting user-controllable data in HTTP responses, encode the output to prevent it from being interpreted as active content. Depending on the output context, this may require using combinations of HTML, URL, JavaScript, and CSS encoding.
- Use Appropriate Response Headers: For HTTP responses not intended to include HTML or JavaScript, employ Content-Type and X-Content-Type-Options headers to ensure browsers interpret the responses correctly.
- Implement Content Security Policy (CSP): As a final layer of defense, employ Content Security Policy (CSP) to reduce the impact of any remaining XSS vulnerabilities.
FAQ’s
What exactly is cross-site scripting (XSS)?
Cross-site scripting (XSS) is a web security vulnerability that allows attackers to compromise user interactions with a vulnerable application. It enables attackers to impersonate users, execute actions within their capabilities, and access their data, potentially leading to full control over the application.
How does XSS work in practical terms?
XSS involves manipulating a susceptible website to deliver malicious JavaScript to users. Once executed in a victim’s browser, the attacker gains the ability to fully compromise the user’s interaction with the application.
How severe is the impact of XSS vulnerabilities?
Impact varies based on the application:
- Minimal impact for anonymous and public information.
- Significant impact for applications with sensitive data.
- Critical impact if the compromised user has elevated privileges.
What methods are effective for finding and testing XSS vulnerabilities?
Utilize Burp Suite’s web vulnerability scanner for automated detection. Manual testing involves submitting unique input, identifying reflected or stored locations, and testing for exploitability. For DOM-based XSS, inspect URL parameters and review JavaScript code.
What is the purpose of Content Security Policy (CSP)?
CSP is a browser mechanism designed to reduce the impact of XSS vulnerabilities. While it aims to block or impede exploitation, it can be bypassed, allowing for the exploitation of underlying vulnerabilities.
Can you elaborate on dangling markup injection and its use cases?
Dangling markup injection captures cross-domain data when a full XSS exploit is challenging. It is used to seize sensitive information visible to other users, including CSRF tokens for unauthorized actions.
How can one effectively prevent XSS attacks?
Effective prevention involves:
- Filtering input on arrival.
- Encoding data on output.
- Using appropriate response headers.
- Implementing Content Security Policy (CSP) as a final layer of defense.
Conclusion
safeguarding against cross-site scripting (XSS) is imperative for web application security. XSS vulnerabilities pose significant risks, including unauthorized data access and application compromise. Employing tools like Burp Suite, implementing preventive measures such as input filtering, encoding, and Content Security Policy (CSP) are crucial steps to fortify against XSS attacks. Staying vigilant and adopting a multi-faceted security approach are essential for web application integrity and user protection.
ad


Comments are closed.