What Is TLS (Transport Layer Security)
Transport Layer Security (TLS) is a method for securing information as it is transmitted over the Internet: website visitors, emailers, instant messenger users, and Voice over IP users (VoIP)
Transport-layer security works better than its predecessor SSL, and its latest version, TLS 1.3, improves both privacy and performance.
Even though the goal of Transport Layer Security is to keep web communications private, flaws in its design and implementation have led to security holes. But the latest version, TLS 1.3, is a big change that makes the crypto protocol stronger and easier to use.
What is TLS?
TLS is a cryptographic protocol that provides secure communications from one end of a network to the other. It is widely used for online communications and transactions. It is an IETF standard meant to stop people from listening in, messing with, or making up messages. Web browsers, instant messaging, e-mail, and voice over IP are all common applications that use TLS.
TLS is used by many businesses to protect all communications between their Web servers and browsers, whether or not they are sending sensitive data.
Secure socket layer (SSL), which came before TLS, was made by Netscape in 1995. SSL versions 1.0 and 2.0 had a lot of security holes, so the protocol had to be completely redesigned. In 1996, Netscape came out with SSL version 3.0, which TLS1.0 was based on. In 1999, the PCI Council said that SSL should eventually be phased out because TLS 1.0 was a big improvement over SSL 3.0.
TLS vs. SSL
TLS is faster and safer than SSL because it has stronger algorithms for authenticating messages, making keys, and encrypting data. SSL, on the other hand, does not support pre-shared keys, secure remote passwords, elliptical-curve keys, or Kerberos. TLS and SSL can’t work together, but TLS can still work with older devices that only support SSL.
The TLS protocol description says that there are two layers. The TLS record protocol protects the connection, and the TLS handshake protocol lets the client and server verify each other’s identities and agree on security keys before sending any data.
The TLS handshake is a process with several steps. The client and server exchange “hello” messages, keys, a cipher message, and a “finish” message as part of a basic TLS handshake. TLS is flexible enough to be used in different applications because the format and order of exchange can be changed. This is made possible by the multi-step process.
TLS flaws and breaches
Protocol and implementation flaws cause problems with security tools and technology all the time, and TLS is no exception. Here are some of the most serious attacks on TLS/SSL:
- BEAST (2011): The Browser Exploit Against SSL/TLS is a browser exploit that used a weakness in the cipher blocking chain (CBC) to get the unencrypted plaintext from an encrypted session.
- CRIME and BREACH (2012 and 2013): The people who made BEAST wrote the security exploit Compression Ratio Info-link Made Easy, which allows hackers to get the content of Web cookies even when compression and TLS are used. One bad way to use this is to get back the authentication cookies so that attackers can take over web sessions that have already been authenticated. Browser Reconnaissance and Exfiltration via Adaptive Compression of Hypertext, or BREACH, is based on CRIME and gets login tokens, email addresses, and other information.
- Heartbleed, which was found in 2014, lets hackers steal private keys from servers that should be safe. Anyone on the Internet could access infected servers and read the memory of systems that were protected by a weak version of OpenSSL. Threat actors were able to steal data from servers, listen in on conversations, and even pretend to be services or other users through the breach.
TLS 1.3 boosts security, performance, privacy
The Internet Engineering Task Force (IETF) wanted to bring the protocol up to date, and TLS 1.3 was the first big change they made. Think of older versions as bandages put on code that was already broken. Even though these might work for a while, the bad guys eventually figured out how to get around them. Work on TLS1.3 began in April 2014, and it was finally approved in March 2018. This took four years and 28 drafts.
The IETF wanted to make “major improvements in the areas of security, performance, and privacy” in addition to making a major change. The biggest change is that TLS 1.3 makes it much harder for attackers to read HTTPS-encrypted traffic, which protects privacy better.
Version 1.3 also speeds up the handshake by making the encryption process go faster. This is good for security, and it should also make secure web applications run faster. With TLS 1.2, the handshake took several trips back and forth. With version 1.3, there is only one round, and all the information is passed during that one round.
TLS 1.3 should be easy to set up because it is made to replace TLS 1.2 seamlessly and uses the same certificates and keys. Also, if both clients and servers support it, a connection can be set up automatically.
Early on in its development, there were a few problems. The most important one was found in a school system in Maryland, where upgrading to TLS 1.3 broke about 20,000 Chromebooks. Also, financial services companies were very against it because encryption made it impossible for them to see what was going on in their own networks. The IETF made a few changes to the protocol so that monitoring tools could work with it if it was set up correctly.
In addition to making security better, TLS 1.3 got rid of some older algorithms that did nothing but create security holes. These things are:
- RC4 Steam cipher
- DES
- 3DES
- RSA Key transport
- SHA-1 hashing
- CBC Mode ciphers
- MD5
- Diffie-Hellman groups
- EXPORT ciphers
Also, the updated protocol added a feature called “0-RTT resumption,” which lets the client and server remember if they have talked before. If the client and server have talked before, they can use the same keys, skip the security checks, and start talking right away. Some of the bigger tech companies are thought to have pushed for 0-RTT because they would benefit from the faster connections. However, security professionals are worried.
The security benefits of TLS 1.3 should be enough to justify it on their own, but there are also network reasons. TLS 1.3 is easier to use and uses less resources than its predecessor. It also makes security better. This makes it more efficient, so it uses less CPU cycles and has less latency. This makes it perform better.
What is the difference between TLS and HTTPS?
HTTPS is an implementation of TLS encryption on top of the HTTP protocol, which is used by all websites and some other web services. TLS encryption is used by any website that uses HTTPS.
Why should businesses and web applications use the TLS protocol?
TLS encryption can help prevent data breaches and other attacks on web applications. Today, all websites use HTTPS that is protected by TLS. The Google Chrome browser has been slowly cracking down on sites that don’t use HTTPS, and other browsers have done the same. People who use the Internet every day are less likely to visit sites that don’t have the HTTPS padlock icon.
![]()
What does TLS do?
Encryption, Authentication, and Integrity are the three main parts of what the TLS protocol does.
- Encryption: hides the data being transferred from third parties.
- Authentication: ensures that the parties exchanging information are who they claim to be.
- Integrity: verifies that the data has not been forged or tampered with.
How does TLS work?
To use TLS, a website or app must have a TLS certificate installed on its origin server (the certificate is also known as an “SSL certificate” because of the naming confusion described above). A certificate authority gives a TLS certificate to the person or company that owns a domain. The certificate has important information about who owns the domain and the server’s public key, both of which are needed to verify the server’s identity.
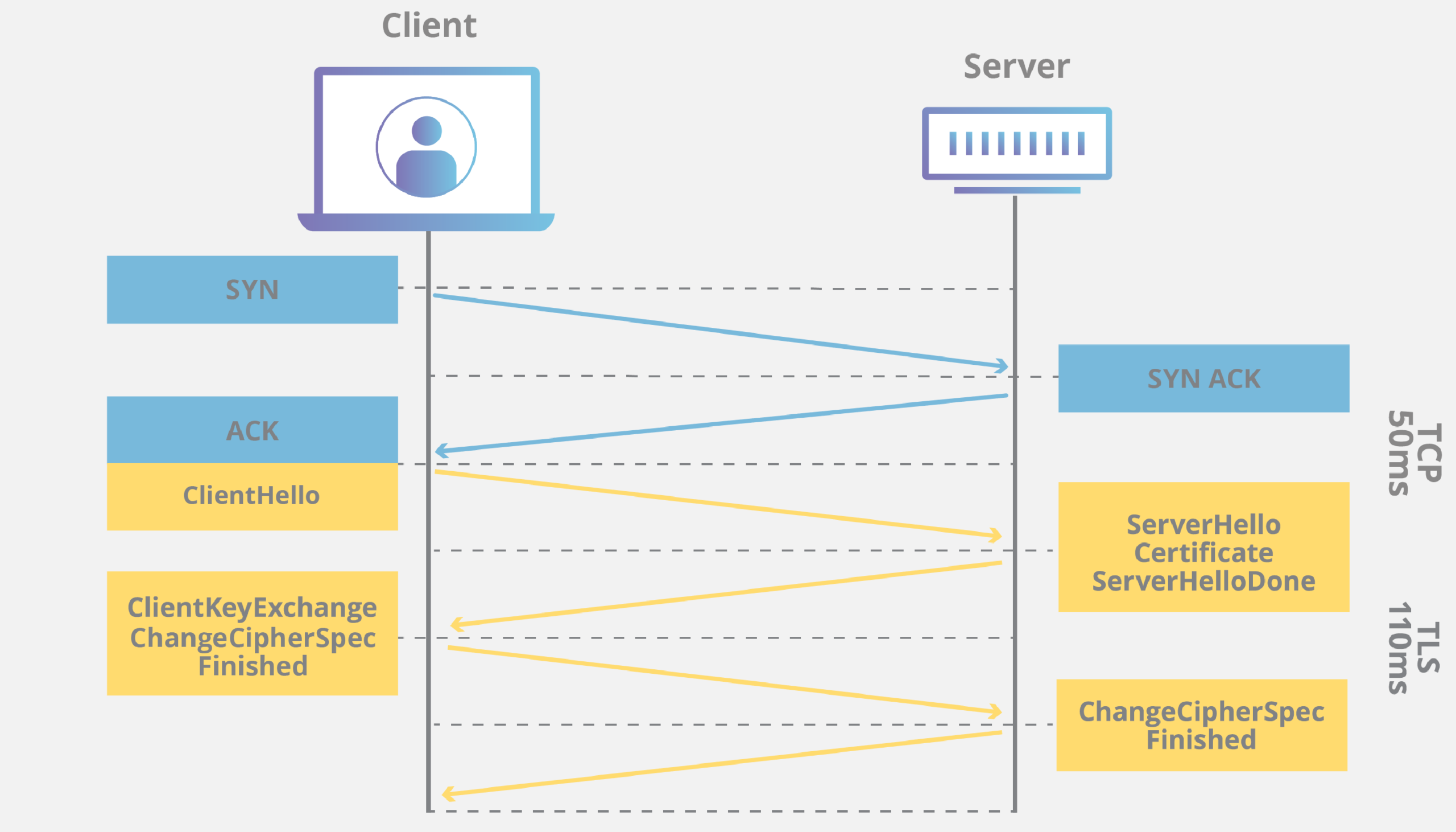
The TLS handshake is a series of steps that start a TLS connection. When a user goes to a website that uses TLS, the TLS handshake begins between the user’s device (also called the client device) and the web server.
During the TLS handshake, the web server and the user’s device:
- Specify which version of TLS (TLS 1.0, 1.2, 1.3, etc.) they will use
- Decide on which cipher suites (see below) they will use
- Authenticate the identity of the server using the server’s TLS certificate
- Generate session keys for encrypting messages between them after the handshake is complete.
During the TLS handshake, a cipher suite is set up for each session of communication. The cipher suite is a group of algorithms that tells you things like which shared encryption keys, or session keys, will be used for that session. Public key cryptography makes it possible for TLS to set the matching session keys over an unencrypted channel.
Authentication is also done during the handshake. Usually, the server proves its identity to the client. Public keys are used to do this. Public keys are encryption keys that only work in one direction. This means that anyone with the public key can decrypt data encrypted with the server’s private key to verify its authenticity, but only the original sender can encrypt data with the private key. The server’s TLS certificate includes its public key.
After data is encrypted and verified, a message authentication code is used to sign it (MAC). The receiver can then check the MAC to make sure the data is correct. This is kind of like the tamper-proof foil on a bottle of aspirin. If the foil is still on the bottle when you buy it, you know that no one has messed with your medicine.
How does TLS affect web application performance?
The latest versions of TLS have almost no effect on the speed of web applications.
Because setting up a TLS connection is a complicated process, some load time and computing power must be used. Before any data is sent, the client and server have to talk back and forth several times. This takes up milliseconds of load time for web applications and some memory on both the client and the server.
But there are technologies that can help make up for any possible delay caused by the TLS handshake. One is TLS False Start, which lets the server and client start sending data before the TLS handshake is done. TLS Session Resumption is another way to speed up TLS. It lets clients and servers who have already talked to each other use a shorter handshake.
Because of these changes, TLS is now a very fast protocol that shouldn’t change load times much. By today’s standards, the costs of computing that come with TLS are mostly not worth mentioning.
Since TLS 1.3 came out in 2018, it has become even faster. In TLS 1.3, TLS handshakes only need one round trip, or back-and-forth communication, instead of two. This saves a few milliseconds and speeds up the process. When a user has already connected to a website, there are no round trips in the TLS handshake, which speeds it up even more.
How to start implementing TLS on a website
download.zone gives all of its users free TLS/SSL certificates. If you don’t use download.zone, you’ll have to get an SSL certificate from a certificate authority, which will usually cost you money, and install it on your origin servers.
Conclusion
Transport Layer Security (TLS) is a widely used security protocol that turns plaintext text into ciphertext text and ciphertext text into plaintext text. This gives your data security and privacy through encrypted traffic, so hackers can’t get to your sensitive data.
Using TLS also has many benefits for businesses and web applications, such as improving your site’s SEO and building customer trust. This could help your business stay competitive on search engine results pages (SERPs).
SSL and TLS offer different ways to do things and different levels of security. Users often use both terms interchangeably, though, because they both do the same thing.
ad


Comments are closed.