What is Two-Factor Authentication (2FA) and how does it work?
We have given an in-depth information in our article here on how easily hackers can steal password and username combinations, it’s no surprise that corporate data breaches occur on a regular basis. And when they do, two-factor authentication is the most effective way to keep your sensitive data safe from theft.
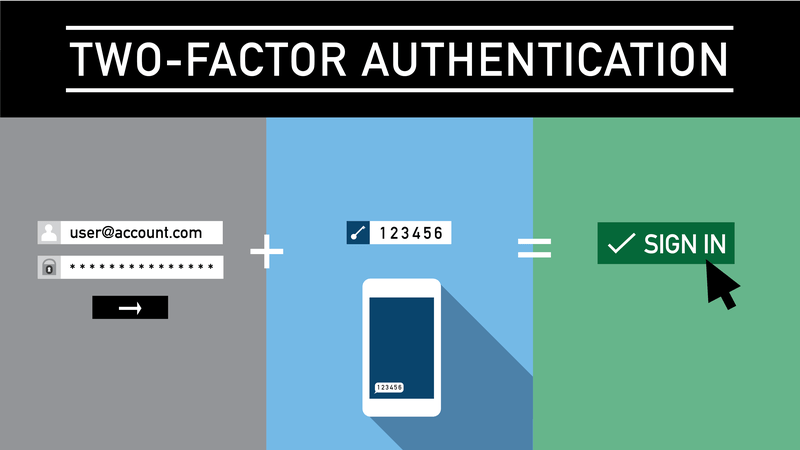
Two-factor authentication (2FA) protects your online accounts by adding an extra layer of security. To gain account access, you must provide an additional login credential in addition to your username and password, and obtaining that second credential necessitates access to something that belongs to you.
It is impossible to enter the account without this additional access method, making it impossible for hackers to access your account using only stolen password and login information.
The following is a simplified diagram of the Two-Factor Authentication Process.
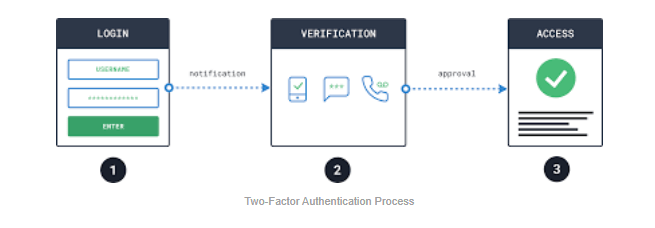
Doesn’t a strong password enough?
Before answering the question ‘what is two-factor authentication‘ or ‘what is 2FA,’ consider why it is critical to do everything possible to improve the security of your online accounts. Just having a strong password won’t give you a full proof security.
| You may like to learn how to improve your online privacy on chrome
Passwords aren’t perfect. They have several issues:
- People are fundamentally bad at choosing good passwords.
- Passwords are frequently written down by people.
- Passwords are frequently forgotten.
- People exchange passwords with one another.
- Many things require passwords, which leads to people using the same passwords for multiple purposes. People are hacked when websites are hacked and passwords are leaked all over the dark corners of the internet.
You could easily argue that this is a sign of “bad” people rather than “bad” passwords. We should all be able to agree that the combination of people and passwords is probably not ideal.
Passwords, like everything else, have flaws. They can provide us with reasonable assurance that you are who you say you are. However, this may not be sufficient for some applications, such as banking or other “important” information.
With so much of our lives taking place on mobile devices and laptop computers, it’s no surprise that our digital accounts have become a magnet for criminals. Malicious attacks on governments, businesses, and individuals are becoming more common. And there are no signs of a slowdown in hacks, data breaches, and other forms of cybercrime!
Fortunately, Two-factor authentication (2fa) is typically used in this situation for an extra layer of security. The degree of confidence can be increased if you can successfully authenticate using two (or more) independent authentication methods.
What exactly is two-factor authentication and why is it so popular?
Two-factor authentication (2FA), also known as two-step verification or dual-factor authentication, is a security procedure in which users provide two distinct authentication factors in order to be verified.
2FA is used to protect both a user’s credentials and the resources that the user has access to. Two-factor authentication provides a higher level of security than single-factor authentication (SFA), which requires the user to provide only one factor, typically a password or passcode. Two-factor authentication methods rely on the user providing a password as the first factor and a second, distinct factor – typically a security token or a biometric factor, such as a fingerprint or facial scan.
Two-factor authentication adds an extra layer of security to the authentication process by making it more difficult for attackers to gain access to a person’s devices or online accounts because a password alone is not enough to pass the authentication check, even if the victim’s password is hacked.
For a long time, two-factor authentication has been used to control access to sensitive systems and data. 2FA is increasingly being used by online service providers to protect their users’ credentials from being used by hackers who have stolen a password database or used phishing campaigns to obtain user passwords.
Two-factor authentication is classified into three types:
- Additional login credentials should only be known by the account holder. This includes answers to security questions and PIN numbers.
- Account holders’ devices that receive additional login credentials This is most commonly manifested as a security token, a mobile phone app, or a tablet device app.
- Account-specific biometric login credentials. This includes fingerprints and retina scans.
You can choose which 2FA method is best for you. Companies frequently prefer the device method because employees may believe that biometric options infringe on their privacy. Individuals frequently find it less cumbersome to secure their devices with biometric methods because they do not necessitate carrying around multiple devices.
How does two-factor authentication work?
Two-factor authentication secures an account by combining two unrelated authentication methods. In addition to your normal username and password, the second authentication method is usually required to be verified with something in your personal possession, such as your phone.
A login or access method that consists of a password and a security question is insecure because if someone knows one password, they almost certainly know — or can figure out — the security question. Because it is much more difficult to gain access to a completely different factor, such as your actual phone, two-factor authentication is far more secure.
The operation of two-factor authentication is explained by three major factors.
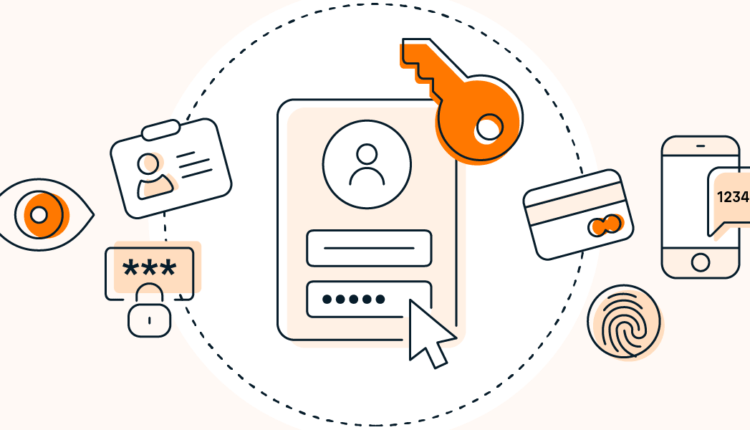
2FA: the three elements
Something you know (like a password), something you have (like a bank card), and something you are are the three factors that can be used for two-factor authentication (like face ID). Two of these factors are required for 2FA. To confirm your physical location, MFA may use all three — or even GPS tracking.
The 2FA authentication factors are as follows:
- Knowledge factor
You are aware of this. It cannot be physically lost or found, but like a password or PIN code, it can be copied.
- Possession factor
This is something you have that is difficult to duplicate but can be stolen, such as a bank card or physical key.
- Inherence (biometric) factor
This is something about you that cannot be easily faked, similar to a fingerprint or face ID.
- Location factor
The location from which an authentication attempt is made is typically used to denote a location factor. This can be enforced by limiting authentication attempts to specific devices in a specific location or by tracking the geographic source of an authentication attempt based on the source Internet Protocol address or some other geolocation information derived from the user’s mobile phone or other device, such as Global Positioning System (GPS) data.
- Time factor
A time factor limits user authentication to a specific time window for logging on and restricts access to the system outside of that window.
Most two-factor authentication methods use the first three authentication factors, but systems requiring additional security may use them to perform multifactor authentication (MFA), which uses two or more independent credentials for more secure authentication.
Two-factor authentication requires that the two access methods used be of different factor types. Using a username and password does not constitute 2FA because both are knowledge factors. Even an additional security question does not qualify as 2FA because it is also a knowledge factor.
Think about your garage door code and house key (possession factor). You need both to unlock your house from the garage. Two-factor authentication uses something you know (code) and something you have (key). Without one, you won’t get in.
Two-factor authentication examples:
ATM withdrawal
- PIN code known
- Your card is ready
OTP codes to access online accounts
- You know your logins
- Your phone’s there
International travelling
- You carry a valid passport
- Facial recognition, fingerprints, and retina scans verify your identity.
These examples explain why two-factor authentication increases security. With 2FA, a hacker can set up a keylogger to copy your password, but they can’t hack you without your phone.
Two-factor authentication rules are consistent, which makes them effective. The 2FA qualities of knowing, having, and being don’t change, and it’s hard to have access to more than one – unless you are who you say you are.
How to set up two-factor authentication (2fa) ?
Many apps and services support two-factor authentication, but it may not be enabled by default. Check the security settings of your account to see if 2FA is enabled. Google has its own Google Authenticator app, which automatically generates 2FA codes. You can also enable 2FA through your Google Account or Gmail account.
Here’s how to enable two-factor authentication on your Google Account:
1.Access your Google Account.
 2. Select Manage your Google Account by clicking your profile picture.
2. Select Manage your Google Account by clicking your profile picture.

3. In the left panel, select Security, then 2-Step Verification.
4. Click Get Started after highlighting 2-Step Verification in Google account settings.
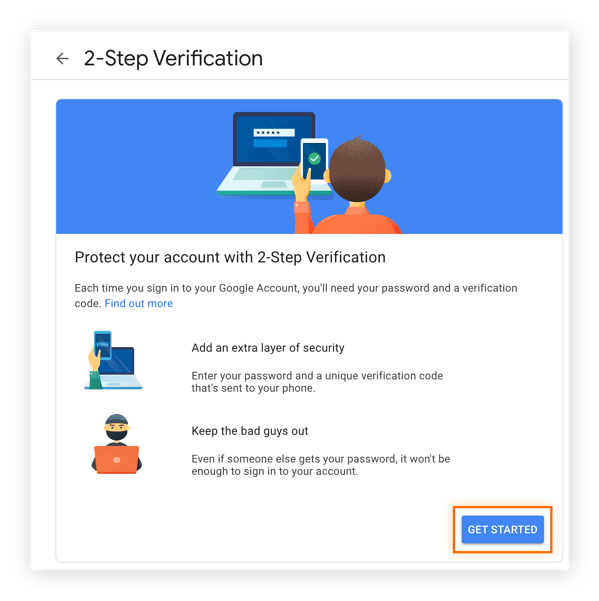
5. Confirm your password by clicking “Get started” on the 2-Step Verification page.
6. Choose how you want to confirm ownership of your phone: a prompt (the default), a security key, a text message, or a voice call. Then click the Try It Now button.
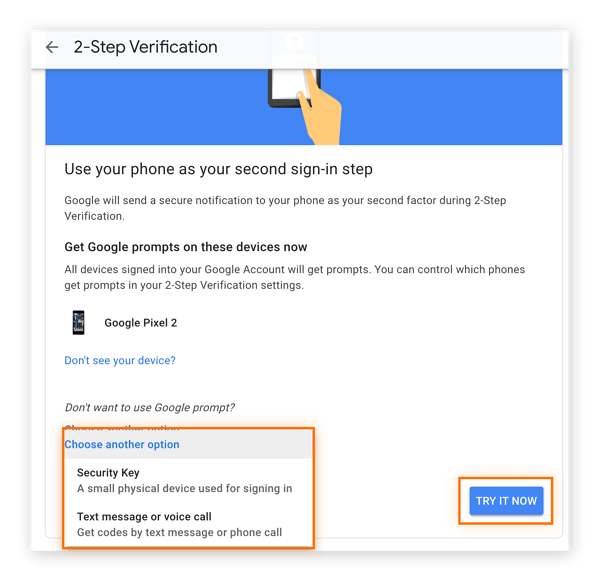
7. On Google’s 2-Step Verification page, Google will ask you to confirm using the prompt on your phone, highlighting other prompt options and the “Try it now” button.
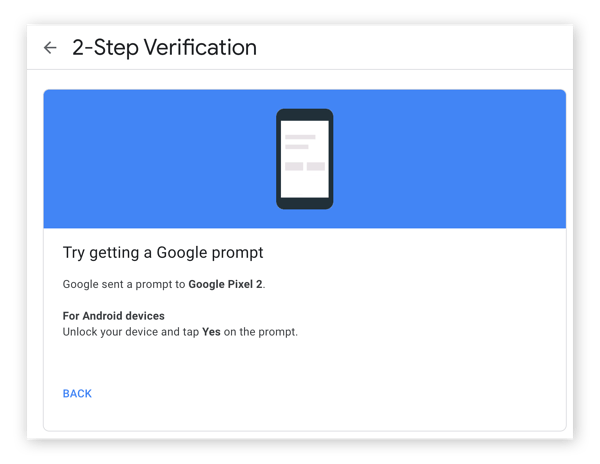
8. Verify using your preferred method of authentication.

9. Now, In case you lose your phone or can’t validate the prompt, add a backup number or email. Then click Send (text or call).

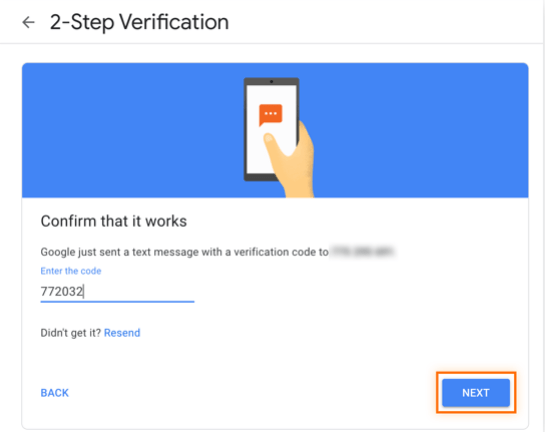
10. Google will send a verification code to your phone.
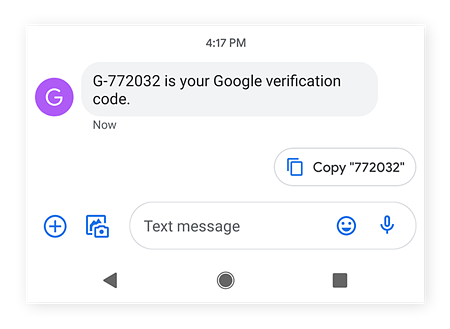
11. Enter your Google 2FA code, then click Next.
12. Now click Turn on.
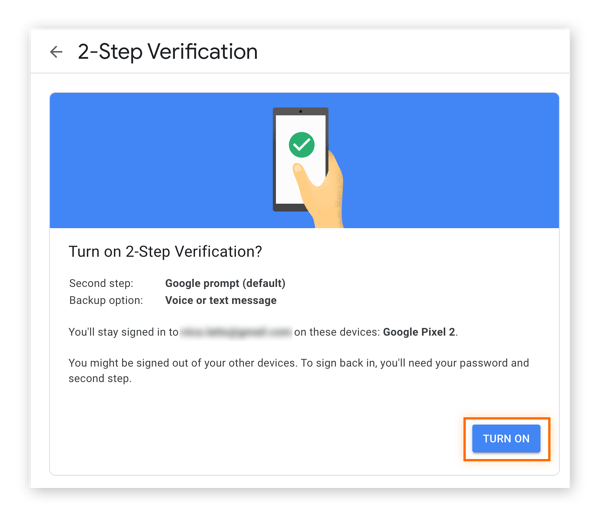
In Google’s 2-Step Verification confirmation screen, highlight the “Turn on” button.
13. Finish! Your Google Account has two-factor authentication. Verify that Google sent a confirmation email.
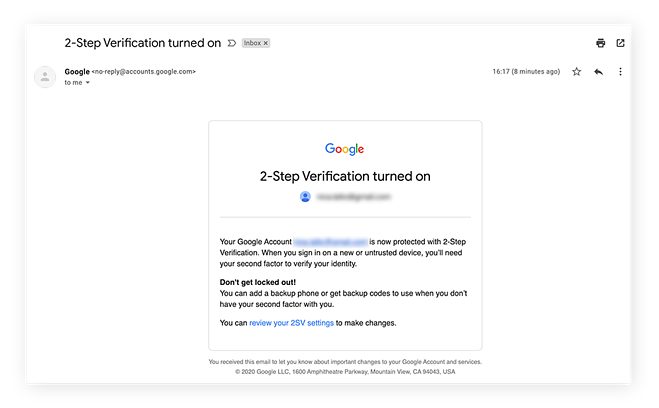
*Google has sent you an email confirming that 2-Step Verification has been enabled.
You can also enable 2FA on your Apple device, as well as Facebook, Reddit, and nearly any other app, platform, or device. Two-step authentication, which includes a strong password and another method of verification, is far more secure than a password alone.
Is Two-Factor Authentication really safe?
A 2FA-enabled account is far more secure than a simple username and password login, but it is not completely foolproof.
2FA Security via Text Message
One of the most serious 2FA security flaws for text messages is the ability of users to keep their cell phone numbers even when switching providers. Hackers can use mobile number portability to impersonate you and switch your number to a phone they control.
If this occurs, hackers will gain access to your accounts via your usernames and passwords.
2FA Security Authentication Applications
Because leaving your device unattended at work or losing it while travelling puts your accounts at risk, authentication apps like Google Authenticator are vulnerable to device theft.
Similarly, security tokens, which are widely regarded as one of the most secure types of 2FA, can be compromised at the manufacturer level.
Customers of RSA Security’s “SecurID” tokens experienced exactly this after a breach exposed sensitive information to hackers.
Biometric Two-Factor Authentication Security
People frequently believe that biometric security is impenetrable. The truth is quite different. Hackers can gain account access even when biometrics are enabled, just like any other security method.
True, a hacker is unlikely to remove your finger to gain access to your accounts (we hope), but these security systems aren’t magic. To function, they must store a digital representation of your fingerprint/retina. That, too, can be hacked.
Best Practices for Two-Factor Authentication
You should never protect your account with just a username and password. The number of corporate security breaches in recent memory demonstrates that hackers can easily gain access to your accounts.
However, two-factor authentication is not a foolproof method of preventing commerce fraud.
Using text messages, authenticator apps, or biometric methods is preferable to nothing, but you should go above and beyond by following these 2FA best practices:
- For text 2FA authentication, do not use your personal phone number.
Phone companies are notorious for being duped into changing account information by skilled hackers. Instead, create a dedicated Google Voice number that you can keep indefinitely and that no phone carrier can change. - Account resets via email should not be used.
It is more convenient to reset your passwords via email. This is because it allows a hacker to easily bypass other 2FA procedures and access the account with just a username and password. - Use a mix of authentication methods.
Multiple 2FA methods can be used to secure multiple accounts. And the more 2FA methods you employ, the more secure your data will be.
Two-factor authentication is a critical step in preventing eCommerce fraud. Although adding more layers is inconvenient, it is far less inconvenient — and costly — than a fraudster impersonating you, gaining access to your personal information, or stealing your bank account information.
Mobile device two-factor authentication
Smartphones provide a variety of 2FA capabilities, allowing businesses to choose what works best for them. Some devices can recognize fingerprints, use the built-in camera for facial recognition or iris scanning, and recognize voice using the microphone. As an additional factor, smartphones with GPS can confirm location. Voice or Short Message Service (SMS) can also be used as an out-of-band authentication channel.
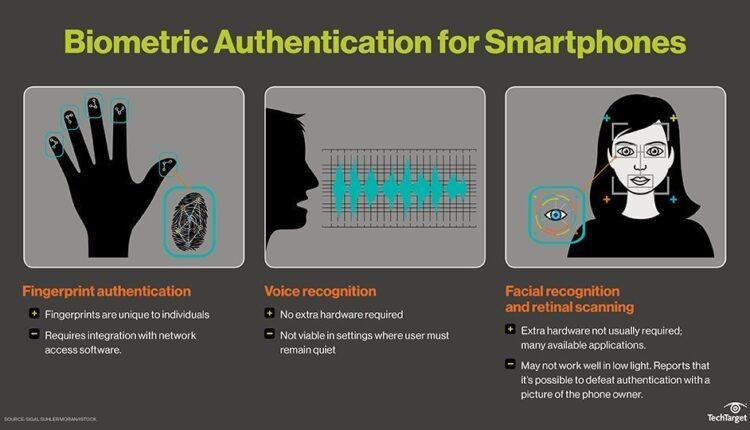
To receive verification codes via text message or automated phone call, enter a trusted phone number. To enroll in mobile 2FA, a user must verify at least one trusted phone number.
Apple iOS, Google Android, and Windows 10 all have 2FA apps that allow the phone to act as the physical device to satisfy the possession factor. Duo Security, based in Ann Arbor, Mich., and acquired by Cisco in 2018 for $2.35 billion, has a platform that allows customers to use trusted devices for two-factor authentication. Before verifying that a mobile device can also be trusted as an authentication factor, Duo’s platform first establishes that a user can be trusted.
Authenticator apps eliminate the need for a verification code obtained via text, voice call, or email. To access a website or web-based service that supports Google Authenticator, for example, users must enter their username and password – a knowledge factor. The user is then asked to enter a six-digit number. Instead of waiting a few seconds for a text message, an authenticator generates one for them. These values change every 30 seconds and are unique for each login. Users complete the verification process and demonstrate ownership of the correct device by entering the correct number.
These and other 2FA products provide information on the minimum system requirements for 2FA implementation.
Our Thoughts
Three-factor authentication combines a physical token, a password, and biometric data like fingerprints or voiceprints for enhanced security. Geolocation, device type, and time of day are also utilized to authenticate or ban users. Behavioral biometric identifiers, such as a user’s keystroke length, typing speed, and mouse movements, can also be monitored in real time for ongoing authentication instead of a single login check.
Passwords, while widespread, no longer give the security or user experience that companies and customers demand. Legacy security technologies like a password manager and MFA try to deal with usernames and passwords, but they rely on an antiquated architecture: the password database.
Many companies use passwordless authentication. Using biometrics and secure protocols, users can authenticate themselves without entering passwords. In business, this means employees may access their work without passwords and IT still controls every login. Blockchain is getting interest as an alternative to traditional identification methods, such as decentralized identity or self-sovereign identity.
ad


Comments are closed.