What Is the Mirai Botnet?
The Mirai botnet searches the internet for unprotected smart devices and takes control of them to form a network of bots that can execute severe cyberattacks. We’ll describe how these botnets operate, why new Mirai threats keep arising, and how to protect your connected devices with robust security software.
ad
What is Mirai?
Mirai is a type of malware that targets consumer devices such as smart cameras and home routers, converting them into a network of remotely controlled bots. Cybercriminals use these Mirai botnets to conduct large-scale distributed denial of service (DDoS) attacks on computer systems.
Mirai specifically affects networked smart home devices like routers, thermostats, baby monitors, and refrigerators by exploiting vulnerabilities in the Linux OS that many IoT devices use. This malware links these devices into a botnet.
Once part of the botnet, the hijacked devices are used to carry out further attacks as part of a network of zombie machines. While traditional botnets are often employed for phishing and spam attacks, Mirai botnets are particularly effective at taking down websites or servers through DDoS attacks, thanks to the nature of IoT devices.
ad
How was Mirai created?
The origins of Mirai can be traced back to a college student named Paras Jha and his friend Josiah White. In 2016, they developed the Mirai botnet source code and used it to attempt to extort Jha’s own university by launching DDoS attacks against the institution.
Jha and White then escalated their hacking activities by targeting servers that hosted the highly popular Minecraft video game, as well as the companies responsible for protecting these valuable gaming servers from such DDoS disruptions.
Who created the Mirai botnet?
Paras Jha and Josiah White were responsible for the initial development and use of the Mirai botnet against Minecraft gaming servers. However, in September 2016, it appears that they leaked their own code online to obscure the origins of their botnet attacks.
Once released, Mirai rapidly spiraled out of control as other cybercriminals replicated and modified it. Since then, it has continued to cause significant disruption, including a notable wide-scale DDoS attack that affected large portions of the internet across the US.
How does Mirai work?
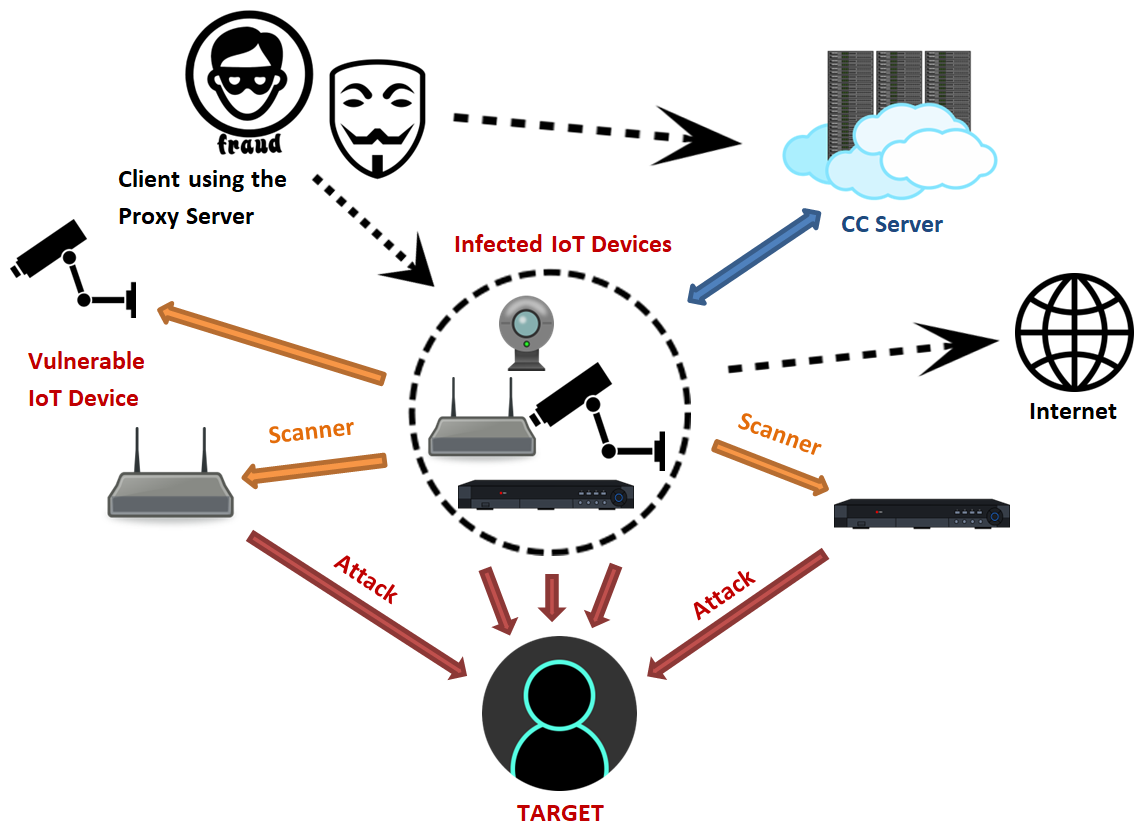
To understand how the Mirai botnet operates, you need to start with the extensive network of internet-connected household devices known as the Internet of Things. These devices are becoming increasingly common in modern smart homes but also present additional vulnerabilities for cybercriminals to exploit.
Mirai malware begins by scanning IP addresses to find smart devices running a version of Linux known as ARC. It then takes advantage of security weaknesses in these IoT devices by using default username and password combinations. If these credentials haven’t been changed or updated, Mirai can log in and infect the device with malware.
As more devices become part of the infected network, the cybercriminals controlling the Mirai botnets use them to overwhelm targeted websites or servers with more traffic than they can handle. This causes the site or service to become inaccessible to regular users until the DDoS attack is mitigated, often requiring the payment of a ransom.
Why does the Mirai malware remain dangerous?
The Mirai botnet is evolving.
Although its original creators have been apprehended, their source code continues to be used. It has led to the development of various variants, including Okiru, Satori, Masuta, and PureMasuta. For instance, PureMasuta can exploit the HNAP vulnerability in D-Link devices, while the OMG strain turns IoT devices into proxies, helping cybercriminals maintain anonymity.
Additionally, a newly discovered and potent botnet, known as IoTrooper or Reaper, can compromise IoT devices at a much faster rate than Mirai. Reaper targets a wider range of device manufacturers and has significantly greater control over its network of bots.
Mirai and smart devices
Once Mirai infects a smart device, it converts it into a zombie within a network of remotely controlled bots. To secure the device within the botnet, Mirai will even remove any pre-existing malware, all without the owner’s consent or knowledge.
Controlled by the botnet creator, the compromised IoT hardware can then be used to scan networks for additional vulnerable devices, drawing more victims into the Mirai botnet. Since most smart homes lack comprehensive network security, their devices remain susceptible to Mirai and other IoT botnets.
What kind of devices are under threat?
While home routers and cameras are the primary targets of the Mirai botnet, nearly any smart device can fall victim to IoT botnets. The same network connection that enables robot vacuums, IP intercoms, kitchen appliances, and smart vehicles to function in a smart home also serves as a potential entry point for malware.
Certain parts of the IoT remain immune to Mirai, but this is due to the malware’s creators intentionally programming the code to avoid attacking specific IP addresses, such as those belonging to the US Department of Defense.
Is Mirai still a threat?
Although the FBI quickly apprehended Mirai’s creators, the malware they developed continues to circulate. As a result, Mirai, its variants, and similar botnets still present a serious threat to unprotected devices and networks. This underscores the importance of safeguarding your devices with robust anti-malware software.
Defense against the Mirai botnet
Mirai exploits default usernames and passwords, attempting to find the right combination to gain access. Instead of brute-forcing a single device, Mirai will simply move on to an easier target. Therefore, your first priority should be changing the default login credentials and setting a strong password for your IoT devices as soon as possible.
Using a random password generator to create long, complex passwords that are difficult to guess or crack can help secure your otherwise vulnerable IoT devices.
However, even as cyber threats targeting smart devices become more advanced, built-in IoT security protocols often remain relatively weak. It only takes one compromised device to expose an entire system, so it’s crucial to take extra measures to secure your smart home.
What is the connection between Mirai and click fraud?
Pay-per-click (PPC), also referred to as cost-per-click (CPC), is an online advertising model where a company pays a website to display its advertisement. The payment is based on the number of visitors who click on the ad.
When CPC data is manipulated fraudulently, it is known as click fraud. This can occur through manual clicking, automated software, or bots, generating illicit profits for the website at the expense of the company running the ads.
The original creators of Mirai were convicted for renting out their botnet for DDoS attacks and engaging in click fraud.
Does botnet infection degrade performance for IoT devices?
It might. Occasionally, infected devices may run more slowly, but they typically continue to function as usual. This gives owners little incentive to remove the infection.
FAQ’s
What is the Mirai botnet?
Mirai is malware that turns smart devices like cameras and routers into bots for DDoS attacks. It spreads by exploiting default usernames and passwords.
Why is Mirai still a threat?
Although the creators were caught, Mirai’s code is still used, leading to new, dangerous variants that continue to target unsecured devices.
How can I protect my devices from Mirai?
Change default passwords on your devices and use strong, unique passwords. Regularly update firmware and consider using anti-malware software.
Which devices are at risk?
Any smart device connected to the internet, such as routers, cameras, and appliances, can be at risk if not properly secured.
Can Mirai affect device performance?
Infected devices might run slower but often function normally, making the infection hard to notice.
What’s the link between Mirai and click fraud?
The creators of Mirai also used the botnet for click fraud, generating false clicks on online ads to make money.
Conclusion
The Mirai botnet continues to be a serious threat, with its code leading to new, dangerous variants. To protect your devices, change default passwords, use strong credentials, and ensure your security measures are up-to-date. Staying vigilant can help keep your smart devices safe from these cyber threats.
ad


Comments are closed.