What is a Watering Hole Attack?
A watering hole attack is a type of cyberattack that focuses on groups of users by infecting websites they commonly visit. The term “watering hole” is derived from animal predators that wait near watering holes for opportunities to attack prey when they are vulnerable. Similarly, in the cyber context, attackers linger on specific websites, awaiting chances to inject malware and subsequently infect unsuspecting victims.
Unlike phishing and spear-phishing attacks, which aim to steal data or install malware directly on users’ devices, watering hole attacks have a different objective: to infiltrate users’ computers and gain entry into connected corporate networks. Through this attack method, cybercriminals aim to pilfer personal data, banking information, intellectual property, and illicit access to sensitive corporate systems.
Although relatively uncommon, watering hole attacks remain highly effective due to their targeting of legitimate websites that cannot be blacklisted. Cybercriminals leverage zero-day exploits, evading detection by antivirus software and scanners. Consequently, organizations and individuals lacking robust security practices face significant risks from watering hole attacks.
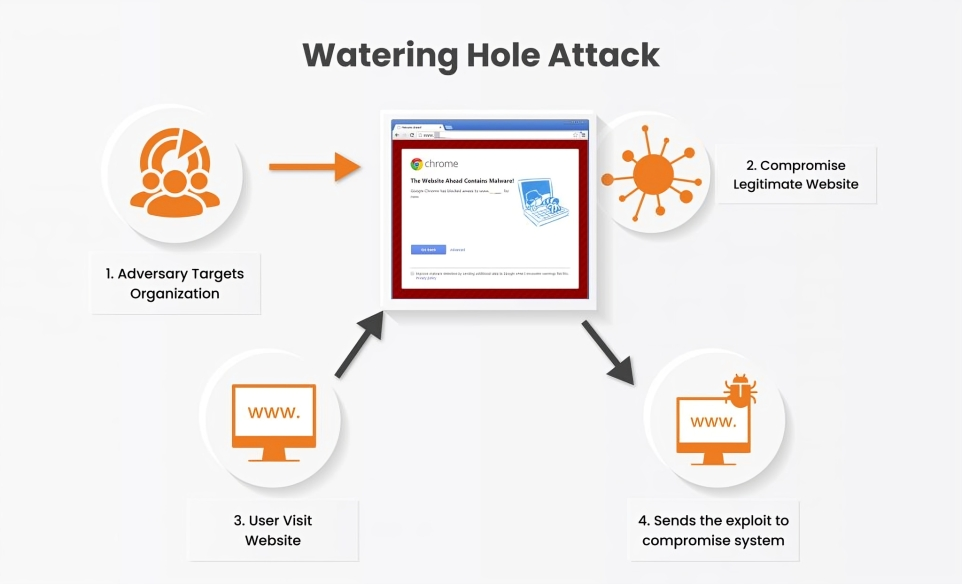
How Does a Watering Hole Attack Work?
ad
In a watering hole attack, cybercriminals wait on legitimate websites for opportunities to target victims. They may seek financial gain or aim to build a botnet by compromising popular consumer websites. Typically, attackers focus on public websites frequented by professionals in specific industries, such as discussion boards, industry conferences, and industry-standard bodies.
To begin, the attacker profiles their targets, often employees of large organizations, government agencies, or human rights groups, to discover the types of websites they visit most frequently. The attacker then searches for vulnerabilities within these sites, creates an exploit to compromise them, infects the websites, and waits for a victim. Often, they infect a website by injecting it with malicious Hypertext Markup Language (HTML) or JavaScript code, redirecting victims to a likely spoofed website hosting the attacker’s malware.
Some watering hole attacks involve cybercriminals delivering and installing malware without the victim realizing it, known as a drive-by attack. This exploit relies on the victim’s trust in the visited website, leading them to unknowingly download a file infected with malware. In such cases, the attacker typically uses malware like a Remote Access Trojan (RAT), providing remote access to the victim’s computer.
How To Prevent Watering Hole Attacks
Opportunistic watering hole attacks may be detected by web gateways equipped with known attack signature recognition. However, the sophisticated nature of these advanced attack methods by cybercriminals often demands more dynamic security solutions. These solutions must be capable of identifying, monitoring, and halting malicious activities while preventing users from accessing suspicious websites.
Implementing the following best practices can assist organizations in safeguarding their networks and users against falling victim to watering hole attacks:
- Regular security testing: Organizations should conduct routine tests on their security solutions to ensure they maintain adequate defense levels. This practice guarantees secure internet browsing for users, mitigates the risk of intentional or unintentional malware downloads, and blocks access to infected or malicious websites.
- Advanced threat protection: Utilizing security solutions equipped to handle advanced attack vectors is essential in warding off watering hole attacks. Incorporating tools like behavioral analysis solutions enhances the likelihood of detecting zero-day exploits before attackers can exploit users.
- System and software updates: Timely updates to systems and software, including prompt installation of operating system patches provided by vendors, are critical practices for evading watering hole attacks. Since attackers exploit vulnerabilities in website code, identifying and addressing software flaws before cybercriminals exploit them is imperative.
- Treat all traffic as untrusted: Adopting a cautious approach of regarding all traffic as untrusted until verified as legitimate is crucial for organizations. This principle is particularly relevant for third-party traffic and should be consistently applied to internet traffic, irrespective of its origin, whether from partner websites or well-known internet domains like those of Google.
- Test and secure against exposure: Secure web gateways (SWGs) play a vital role in enforcing internet access policies and filtering out unwanted or malicious software from reaching user-initiated internet connections. This becomes increasingly crucial with the expanding Internet-of-Things (IoT) and cloud applications, which broaden organizations’ attack surfaces. SWGs safeguard organizations from external and internal threats through features such as application control, Uniform Resource Locator (URL) filtering, data loss prevention (DLP), remote browser isolation, and thorough Hypertext Transfer Protocol Secure (HTTPS) inspection. Implementing such solutions is essential for shielding businesses against advanced cybersecurity threats like watering hole attacks.
📚 Also Read: What is a Salami Attack and How to protect against it?
Examples of Watering Hole Attacks
In 2015, a Chinese hacking group launched a watering hole attack targeting the renowned news organization Forbes. Exploiting zero-day vulnerabilities in Internet Explorer and Adobe Flash Player, the campaign displayed malicious versions of Forbes’ “Thought of the Day” feature via a Flash widget whenever visitors accessed the site. Consequently, any vulnerable devices visiting the Forbes website were susceptible to infection by the watering hole attack.
In August 2019, FortiGuard Labs uncovered a watering hole attack aimed at the community of a U.S.-based Chinese news site. This attack capitalized on known vulnerabilities in WinRAR and Rich Text Format (RTF) files, employing diverse techniques, tools, and backdoor functionalities to target victims.
Another notable instance of watering hole attacks occurred in February 2019, involving the exploitation of Microsoft’s Visual Basic Script (VBScript) programming language to disseminate unique malware. Discovered by Trend Micro researchers, this threat downloaded a “gist” snippet from GitHub, altered the code to craft an exploit, and employed a multistage infection strategy incorporating a backdoor undetectable by antivirus products. The malware also connected to private Slack channels to entice victims, showcasing the utilization of sophisticated hacking techniques.
FAQ’s
How does a watering hole attack differ from other cyberattacks like phishing?
Watering hole attacks target groups of users by infecting websites they commonly visit, unlike phishing attacks that aim to steal data directly from users’ devices. In watering hole attacks, cybercriminals infiltrate legitimate websites to infect users’ computers and gain access to connected corporate networks.
Why are watering hole attacks considered effective despite being relatively uncommon?
Watering hole attacks remain effective due to their targeting of legitimate websites that cannot be blacklisted. Additionally, cybercriminals utilize zero-day exploits, evading detection by antivirus software and scanners.
What are some common targets of watering hole attacks?
Typically, attackers focus on public websites frequented by professionals in specific industries, such as discussion boards, industry conferences, and industry-standard bodies.
How can organizations prevent watering hole attacks?
Implementing dynamic security solutions capable of identifying, monitoring, and halting malicious activities is crucial. Regular security testing, advanced threat protection, system and software updates, treating all traffic as untrusted, and employing secure web gateways are essential preventive measures.
Conclusion
Watering hole attacks pose a serious and effective threat in cybersecurity due to their targeted approach and use of zero-day exploits. Organizations must prioritize proactive security measures such as regular testing, advanced threat protection, timely updates, and dynamic security solutions to defend against these sophisticated attacks. By adopting these practices, businesses can strengthen their defenses and protect their networks and users from exploitation by cybercriminals.
ad


Comments are closed.