What is Scareware?
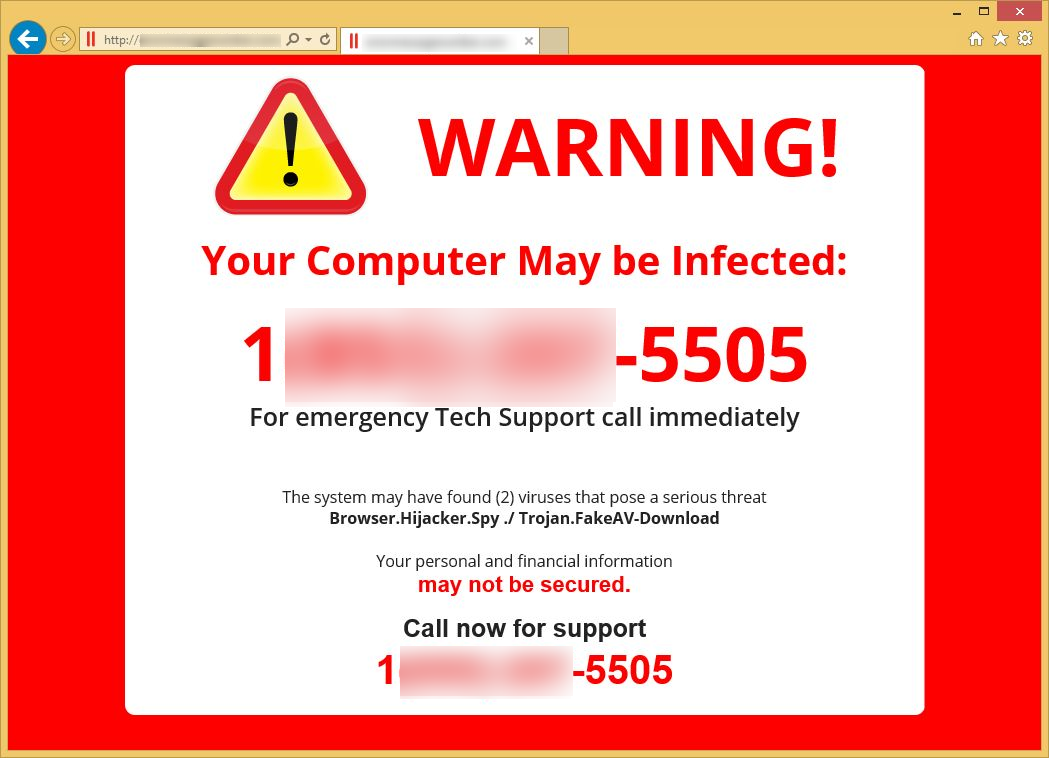
Have you ever encountered messages like “Warning! Your computer may be infected!!!” on your computer? The most advisable response is likely to ignore it.
Scareware, a type of ad or message, aims to frighten users into purchasing or downloading unnecessary (and possibly malicious) software—also known as scareware itself. This tactic is intended to induce feelings of shock and panic and is a form of social engineering.
What is scareware?
Scareware functions as a manipulative tactic, exploiting fear to deceive individuals into downloading malware, losing money, or revealing personal information.
ad
In its typical form, scareware falsely notifies users of a supposed virus on their system, then prompts them to purchase fake antivirus software, which either provides no protection or is malware itself.
Virtually all computer users encounter scareware attempts while browsing the internet, often through urgent pop-up warnings claiming malware detection during a “virus scan.” Initially, scareware attacks caused minor disruptions, with victims persuaded to spend a few dollars on useless software. However, in modern times, scareware serves as an entry point for more serious cyber threats, such as ransomware.
How does scareware work?
Scareware schemes typically commence with a message, which could be a forged text, a phishing email, or most commonly, a browser pop-up. The key feature of such messages is their use of scare tactics, such as threats of a virus or legal repercussions, aimed at compelling the victim to act promptly.
Scareware pop-ups often mimic the branding of reputable companies like Google to appear authentic. Fraudsters may also employ URLs and product names that seem legitimate, such as “Mac Virus Defense” or “Windows Fixer.” Some scammers disguise their pop-ups as alerts from the device’s operating system, displaying messages like “Android has detected a problem!” Others simulate notifications from genuine antivirus programs, such as “A recent scan found five viruses on your device.”
Following the scare tactics, scareware messages present a purported “solution” to the alleged “problem.” Typically, scammers direct victims to download counterfeit security software or make a payment. If users comply, several scenarios may unfold:
- Users are redirected to a fraudulent website, where they input their credit card details to purchase the software. However, no software exists, and scammers steal the victim’s information for identity theft.
- Some scammers charge users for software that serves no purpose, aside from potentially slowing down their device.
- In the most severe instances, scareware programs act as Trojan horses carrying malicious software, such as spyware designed to clandestinely collect personal data.
Even if victims refrain from following the scammers’ directives, scareware can infiltrate their devices. Certain hackers design their pop-up windows in a way that clicking the “close” button initiates a surreptitious drive-by download.
Scareware and ransomware
Hackers may utilize scareware tactics as a means to propagate ransomware, a malicious software type that seizes control of devices or files and demands payment for their release. It’s often easier to convince victims to download fake antivirus software than to breach network security.
Certain scareware disguises itself as ransomware to extort money. For instance, a scareware variant known as “ALC Ransomware” falsely notifies victims that their files have been encrypted and demands payment. In reality, no encryption has occurred. Hackers rely on users’ fear to coerce them into sending money regardless.
Furthermore, some scareware programs act as a form of ransomware themselves by rendering devices unusable until their demands are met. For example, a counterfeit antivirus program might flood a device with persistent pop-up “warnings” that only disappear after the user pays to “upgrade” the software.
Examples of scareware
Scareware scams come in many forms. Some of the most common tactics include:
Fake virus scams
The traditional scareware tactic employs pop-up messages to alert users that their devices have been infected with malware. These pop-ups often mimic authentic scan reports from legitimate antivirus software. Subsequently, scammers prompt users to download counterfeit security software, which either extracts their money or installs malware. For instance, the perpetrators of the counterfeit antivirus application SpySheriff pressured users into paying to eliminate non-existent malware.
Fake tech support
Scammers impersonate legitimate support personnel from companies like Apple or Microsoft. Typically, these scams commence with a pop-up directing the victim to call a specified phone number for assistance, although some scammers may initiate cold calls to their targets. Once in communication with the victim, the scammer persuades them to uninstall authentic security software and grant remote access to their device. Subsequently, the scammer either pilfers the victim’s data or installs malware.
In some instances, tech support scams entail charging victims for fraudulent services. This was exemplified in the 2019 Office Depot scandal, where employees conducted fake scans on customers’ computers and used the results to peddle unnecessary repair services. Upon the revelation of the scandal, the Federal Trade Commission mandated Office Depot and its partner, Support.com, to pay USD 35 million in settlements.
Malvertising
Malvertising refers to a cyberattack wherein hackers exploit legitimate advertisements or ad spaces, such as those found on Facebook or in Google search results, to disseminate viruses. In instances of scareware, a user may encounter an advertisement on a webpage offering free antivirus software. Given that it appears as an advertisement rather than a dubious pop-up, users might be more inclined to click on it.
Law enforcement scams
Cybercriminals often pose as law enforcement authorities, such as the police or the FBI. They employ pop-up notifications to warn victims about the discovery of “illegal material” on their devices. Victims are then coerced into paying a fine to resolve the purported issue. In some cases, these pop-up messages may even lock the victim’s screen until the payment is made, adding extra pressure.
Scareware removal and protection
Eliminating scareware from a device can pose significant challenges once it’s been infected. Scareware programs have the capability to deactivate other security software and conceal program files, thereby complicating detection efforts. Additionally, certain fake antivirus software has been observed to reinstall itself even after removal.
To thwart the establishment of scareware, organizations and users may find the following tools and practices beneficial:
Cybersecurity awareness training
Scareware, like other forms of social engineering, becomes less effective when encountered by users who are aware of the typical signs of an attack. This includes being able to distinguish between genuine antivirus notifications and deceptive pop-up ads.
Anti-malware tool
Authentic anti-malware and antivirus software are capable of preventing users from installing scareware programs. Additionally, they can aid in the removal of scareware that manages to infiltrate the device. As certain scams manipulate users into disabling antivirus software, security teams might restrict users’ permissions concerning these tools.
Network security tools
Firewalls act as a barrier to prevent malicious traffic from reaching users’ web browsers, while URL filters are effective in blocking access to scam websites. Furthermore, other network security tools like ad blockers, pop-up blockers, and spam filters also play a crucial role in preventing scareware messages from appearing.
Software updates and patches
Similar to many other cyberthreats, scareware programs capitalize on system vulnerabilities to infiltrate devices. Maintaining up-to-date security tools, web browsers, and other applications can effectively counter tactics such as malvertising and drive-by downloads.
FAQ’s
What is scareware?
Scareware is a deceptive tactic used by cybercriminals to frighten users into downloading malware, losing money, or divulging personal information through false alerts and fraudulent advertisements.
How does scareware work?
Scareware typically involves pop-up messages or deceptive advertisements that falsely claim the user’s device is infected with malware. Victims are then prompted to download fake antivirus software or pay a fee to resolve the issue, leading to financial loss or malware installation.
What are some common examples of scareware?
Scareware scams come in various forms, including fake virus alerts, fake tech support scams, malvertising, and law enforcement impersonation scams. These tactics aim to deceive users through fear and urgency.
How can I protect myself from scareware?
To defend against scareware, it’s crucial to stay informed about common tactics and signs of deception. Additionally, using reputable anti-malware software, keeping software and security tools up-to-date, and being cautious of suspicious pop-ups and advertisements can help mitigate the risk.
What should I do if I encounter scareware?
A: If you come across scareware messages or pop-ups, it’s advisable to ignore them and refrain from clicking on any links or providing personal information. Instead, close the pop-up window or browser tab and run a scan with legitimate antivirus software to ensure your device’s security.
Can scareware be removed from infected devices?
Removing scareware from infected devices can be challenging, as these programs often disable security software and hide their presence. However, using anti-malware tools and following best practices for malware removal can help eliminate scareware from your device.
How can organizations protect against scareware attacks?
Organizations can enhance their defenses against scareware by implementing cybersecurity awareness training for employees, deploying anti-malware solutions, utilizing network security tools like firewalls and URL filters, and maintaining regular software updates and patches to address vulnerabilities.
What role do software updates play in preventing scareware attacks?
Software updates and patches are essential for mitigating scareware attacks, as they help address known vulnerabilities that cybercriminals may exploit. By keeping security tools, web browsers, and other applications up-to-date, users can reduce the risk of falling victim to scareware tactics like malvertising and drive-by downloads.
Conclusion
Scareware poses a significant cybersecurity risk, exploiting fear to deceive users into downloading malware or revealing sensitive information. By staying vigilant and employing effective security measures like reputable anti-malware software, software updates, and network security tools, individuals and organizations can protect themselves against scareware attacks. Awareness of common scareware tactics is crucial for mitigating this pervasive threat in today’s digital environment.
ad


Comments are closed.