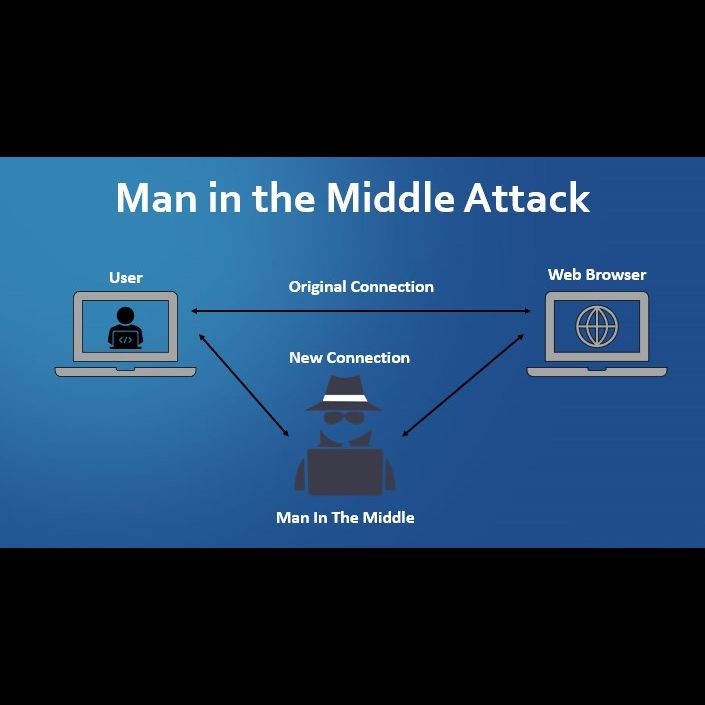
What Is a Man in the Middle Attack (MITM)?
There are various types of security threats that attackers can utilize to exploit insecure applications. Some of these attacks can […]
There are various types of security threats that attackers can utilize to exploit insecure applications. Some of these attacks can […]