What Is Certificate-Based Authentication and How it works?
Certificate-based authentication identifies a user, machine, or device before giving access to a resource, network, application, etc.
Certificate-based authentication is a part of the widely utilized SSL/TLS protocol, as well as numerous other internet security protocols. This is most evident in web browsers, which utilize digital certificates to authenticate online transactions and warn users if they attempt to access an untrusted or unverified website. However, in a broader sense, client certificate-based authentication refers to an end user’s device establishing its identity by transmitting a certificate in order to access a network or other services. This is in contrast to SSL/TLS, which requires servers to authenticate themselves to client devices.
What is Certificate-based authentication?
Certificate-based authentication identifies a user, device, or machine before allowing application, network, or resource access. Certificate-based authentication may be used for all endpoints, including IoT, unlike OTP and biometrics (IoT).
Certificate-based authentication is a more secure alternative to the usual username and password combination. It allows a user’s browser or client to automatically log in to various systems using a saved digital certificate.
Password-based authentication is preferred to certificate-based authentication. Certificate-based client authentication uses the user’s private key in addition to what the user knows (the password) (the password guarding the private key).

This level of control requires official conditions
- No unauthorized users have accessed the client password or machine.
- The client software private key database password is established.
- The software is set to request the password frequently.
Neither password-based nor certificate-based authentication addresses unlawful physical access to credentials or machines. Public-key cryptography verifies if a certificate’s public key and data’s private key match. Users must secure private keys and their devices’ physical security.
The necessity of certificate based authentication
Ease of Installation and easy to manage
Most certificate-based solutions come with a cloud technology that makes issuing, renewing, and revoking certificates easy. Auto enrollment and silent installations can simplify enrollment and issuance using Active Directory-integrated solutions.
Ease of use
Increasing security increases expenses and end-user burden. End users can use certificates easily, despite popular belief. After the certificate is installed (often automatically), nothing else has to be done. Most enterprise systems use certificate-based authentication.
Use access control policies
You can use group policies and permissions to control which users and machines can access certain apps and networks. So only privileged users can access crucial operations.
Mutual Authentication
Certificates provide mutual authentication, meaning both sides in a communication identify themselves, whether user-to-user, user-to-machine, or machine-to-machine. Before establishing a connection, a client must authenticate its identity to a company intranet and vice versa.
Extending to outside users
Certificates are easy to distribute to partners, independent contractors, and freelancers who need to access your networks. They won’t need local software, and the ease-of-use means you won’t need to provide any training.
How is certificate based authentication used?
Although certificate-based authentication is highly versatile and has many potential applications, the following are some of the most frequent ones we hear about from customers. The goal of all of these, as well as certificate-based authentication in general, is to prevent unauthorized users or rogue machines by allowing access only to authorized users and machines.
Authenticating users
- Windows login
- Accessing intranets, internal networks, or corporate email
- Using cloud-based services like Salesforce, SharePoint, and Google Apps
Authentication of devices and machines
- Locating mobile/field devices that require communication with back-end services (e.g. payment kiosks located in convenience stores)
- Before granting access to WiFi networks, VPNs, Gateways, and other resources, all staff computers and mobile devices must be identified.
- Verifying every server in the organization to enable mutual authentication
How certificate-based authentication works?
An electronic cryptographic document called a digital identity certificate is used to demonstrate private key possession. In contrast to username and password combinations, which are only capable of confirming the user who should have access, certificate-based authentication can validate the user, device, or computer. This additional capability is more essential than ever due to the rising sophistication of assaults as well as the exponential growth in the number of attack surfaces as more devices connect to the network.
Before allowing access to a resource or network, digital certificate-based authentication verifies a user, computer, or device with a digital certificate. Network administrators can revoke certificates from departing employees, renew certificates for current employees, and issue digital certificates to new employees thanks to digital certificate-based authentication.
A single sign-on procedure and certificates are used by a certificate-based authentication server to authenticate in the following steps:
- Using a private key, the client digitally signs a piece of data.
- The client’s certificate is sent over the network together with the signed data.
- The destination server receives both the certificate and the signed data, and after comparing the signed data with the certificate’s public key, it may verify the user’s identity.
- The user is authorized and given access to the network if the results line up.
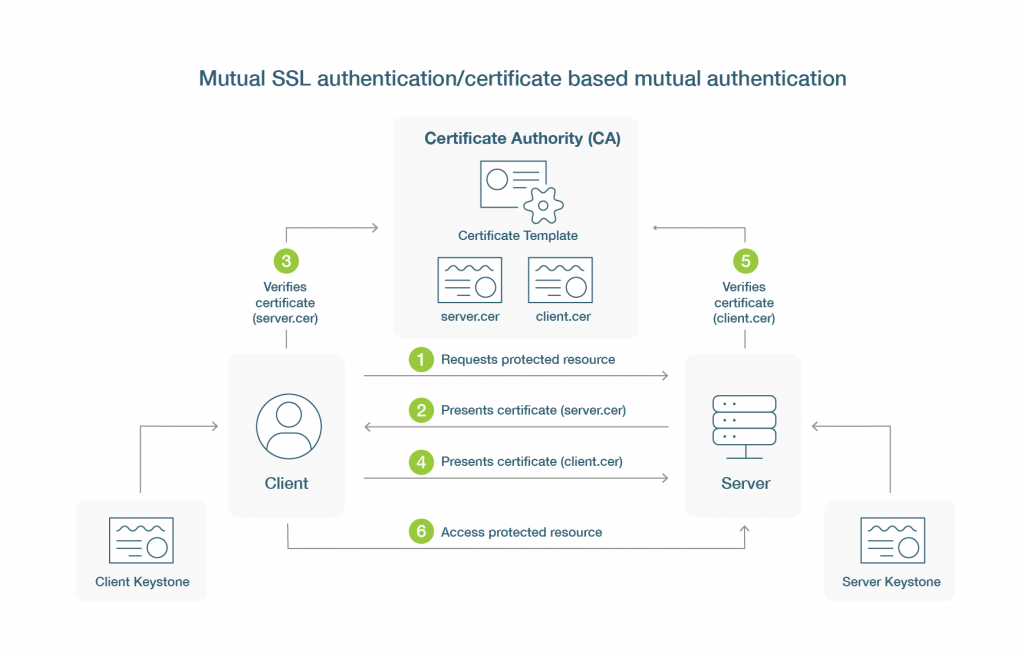
Since the core of authentication is the verification of a person’s or an object’s claimed identity, it is important to stress that client authentication certificates are digital files that are primarily used to limit system access to a select group of users or devices only, not as a way to verify an identity per se. However, in a broader security context, it significantly increases the security of user authentication and machine-to-machine communication.
Access management and building a zero-trust security architecture for businesses are not possible without user authentication. Employees, non-employees, and random people shouldn’t be able to access enterprise servers, networks, apps, or other digital resources without permission. Digital certificates can make sure that users who ask for access to protected sites or resources are real before they are actually given access. Public Key Infrastructure (PKI) certificate-based authentication is one way to reach this goal without using standard login protocols that use passwords. Users don’t have to enter their password again once they’ve logged into their device. Instead, their identity is linked to either their own digital attributes or the identity of their machine and sent to a specific server to be checked.
Digital certificates are important parts of the Public Key Infrastructure that can be trusted (PKI). In the digital world, these files are like “ID cards” for people and things. Just like a traditional form of ID, each digital certificate has its own set of features that make it different from the others. Most people trust them because before they are given out, users and devices have to prove who they are. Then, they can get them from a Certificate Authority, or CA, which is a trusted third party.
A CA looks at Certificate Signing Requests (CSR), which are the forms and paperwork for new digital certificates. This information is checked against official sources to make sure it is correct. The client authentication certificate is then given out only after the claimed identity has been checked and everything matches up.
There are also local, private CAs, and some companies choose to use them to give out their own client authentication certificates. Private certificate issuance is different because there is no need for a publicly trusted CA to check the information first. Because of this, private client authentication certificates aren’t trusted by the public and shouldn’t be used to protect access to external (public-facing) resources. Instead, they should only be used to protect access to internal resources.
Overall, you can think of PKI as the framework that makes it possible for cryptographic technologies (like digital certificates and public-private key pairs), processes, and policies to work together so that you can communicate securely over the internet.
The SSL/TLS handshake is also a part of traditional server authentication. This handshake lets two people have a private conversation in which they share information. The conversation happens over a secure, encrypted channel that no one else can listen in on.
(There are technical differences between the two types of TLS handshakes that are used right now, TLS 1.2 and TLS 1.3, but that’s not what we need to talk about here.)
Here’s a simplified overview of what happens in this process:
- The client sends a request to start a conversation to the server. This is usually done when the user types an address into their browser.
- In response to the first request, the server sends the client its SSL/TLS certificate right away. This has domain information that has been checked by the CA and a public key so that the client can check the claimed identity. The client does this by running the necessary cryptographic checks on the server certificate it received to make sure it is real and was issued by the attributed CA, and then agrees to a handshake.
- Using the server’s public key, the client encrypts a session key and transmits it back to the server.
- The server decrypts the client’s message with its private key. Both parties now have a shared session key, and the session can begin.
- The two sides finally switch over to the agreed-upon new encrypted channel. First, the client changes, and then the server does the same.
- When the user leaves the website, the session is over, and the session keys are thrown away.
Asymmetric encryption is used at first in the standard handshake because it is often thought to be the safest way to share information in public. But public key encryption requires using two different but related keys. This is a waste of time and resources because the keys have to be checked constantly. After authentication for the session, the client and server switch to using just one key in a symmetric encryption scheme. This is because it is more efficient for large-scale encryption and decryption of data.
PKI client authentication is done in a number of steps that are similar but different:
- By starting an HTTPS connection, the device tries to get access to a protected resource, like an internal website or a service.
- As with a traditional TLS handshake, the service or site sends the client a copy of its own SSL/TLS certificate. But this time, the server and device trade PKI certificates, because the site or service will also ask for the device’s public key and client authentication certificate to verify its claimed identity.
- First, the client checks that the server certificate is real and still valid by following the SSL/TLS certificate back to the original certificate that issued it. This is called the “root” certificate. If it matches, the process continues, but if it doesn’t, the connection is cut off right away.
- The client then sends its client authentication certificate to the web server so that the server can check that the user certificate is real and valid. Like trusted server certificates, trusted user certificates have a digital signature and were signed by a cryptographic public key that can be traced back to an issuing CA.
- The server checks the user’s identity and permissions against the resource that was asked for. It is important to link a certificate to a user’s unique identity because the server should refuse the connection if the user or device profile doesn’t have permission to use a resource that is linked to the certificate.
- Based on the authentication process, the server will either block access to the resource or let it through. Only a device or service that can successfully set up a secure, encrypted connection with the server and then check each other’s identities should be able to use certain resources.
Always keep in mind that certificate-based authentication’s high level of security will depend a lot on how well users and devices protect the physical devices and private keys in the network. For example, you can’t leave a device and, more importantly, the authentication credentials it holds open and able to be used and accessed by unauthorized users. If you do, that node could be hacked and given the wrong level of trust to get into the rest of the network.
Certificate based Authentication vs. token based authentication
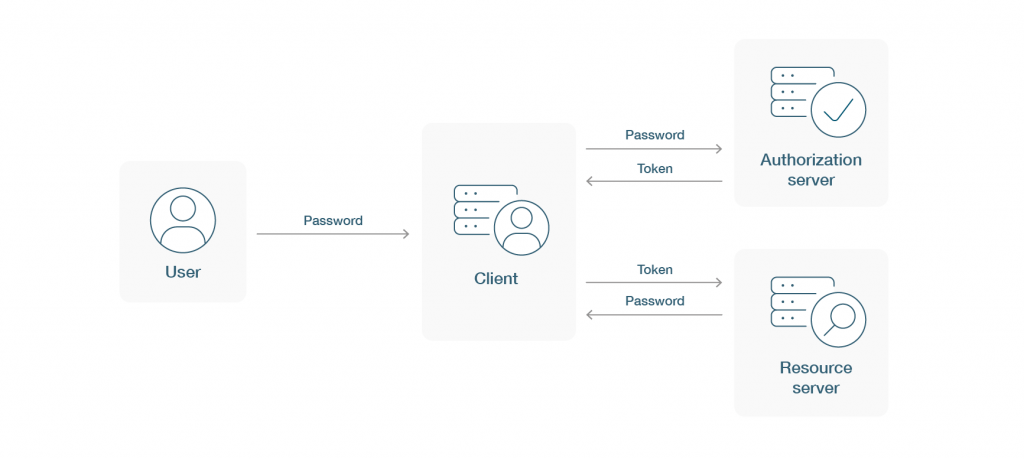
Protocols that use access tokens let users prove who they are in exchange for a unique access token. Users then use an app or website during the lifetime of the token for which it was issued. This way, they don’t have to re-enter their credentials every time they go back to a resource that was protected with the same token.
Auth tokens work like tickets to an event that is still going on. As long as the token is still good, the user has access. Or, to go back to the original example, as long as the event is still going on, the ticket stub can always be used to get back into the venue.
A token-based authentication and an API certificate-based authentication are different in other ways as well.
Certificates use a set of asymmetric keys and are based on public-key cryptography. The client keeps the private key and keeps it safe. The private key is never shared. The public key is sent to the Certificate Authority (CA), where it is signed and stamped into a certificate.
Benefits of certification based authentication
Setting up certificate-based authentication takes more time, but in the long run, it is much safer and saves time. PKI certificate-based authentication has many benefits if it is done right:
- Easy authentication process: Make it easier to prove who you are. Doesn’t need complicated or hard to remember passwords for the client. When employees don’t have to remember passwords, it’s easier for authorized users to get into privileged services and sites. This also cuts down on IT support time and employee stress.
- Reduce the risk of unsecured password uses: Certificate-based authentication makes it so that you can’t leave notes with passwords on an open desk or use the same login for more than one account.
- Passwords attacks like brute force and rainbow table no longer pose a risk: If users don’t have passwords, hackers can’t use brute force to get in.
- Phishing proof: By getting rid of passwords that can be phished, intercepted, stolen, shared, or broken in other ways, organizations make themselves less vulnerable to phishing.
- Extends to external users: It’s easy to give certificates to people outside of the organization who need access to the network, like freelancers, independent contractors, partners, and vendors. They won’t need much more training and won’t need any extra software.
- Ready to deal with new things: For example, if a user leaves the company and their certificate is invalidated, they will no longer have access to anything associated with them.
- Better access controls and allowing least privilege: Limit access to only the devices and people who need it to lower the risk of being exposed. Use the permissions and access control policies that are already in place to control which machines and users can connect to which networks and applications and to protect the most important and sensitive ones.
- Switch to a “zero-trust” infrastructure: Don’t trust anyone right away, and require all users to sign in with certificates instead of passwords.
- Highly Secure: Certificate-based multi-factor authentication (MFA) combined with a trusted platform module (TPM) may be safer than token- and SMS-based MFA alone.
- No need for extra hardware: Even though they are most secure when used with a TPM, most certificate-based solutions today are easy to set up and manage, and they come with a cloud-based platform for management. Certificates are stored locally on the machine or device, so they don’t need any extra hardware like OTP tokens or biometrics, which are used by some authentication methods. This saves money and cuts down on the time it takes to replace, distribute, and get rid of tokens.
- User-friendly: Increased security and the costs that come with it can always be a burden for end users. End users don’t have to do anything after installing a certificate, and most enterprise solutions already support authentication based on certificates.
- Authentication on both sides: Certificates make it possible for both people in a conversation to be identified, which is called mutual authentication. This makes it easier for administrators to find suspicious or unwarranted activity if a network transaction is made by someone with an unknown identity or an identity that is known to have been compromised.
Best Practices for Certificate-Based Authentication Implementation
The tools and procedures your firm uses to enable certificate authentication must be managed effectively. The following are the top client authentication management techniques:
- Establish a policy for managing certificates. This should be a fast reference guide for internal certificate management, containing information on which CAs to use, who within the business is authorized to administer certificates, what management tools or software to use, and which users should have access.
- Secure your private keys. Utilize a TPM or HSM to securely store private keys. Private keys shouldn’t ever be kept on servers with public access.
- Make a plan in the event that your certificate is revoked. The certificate lifecycle must be managed correctly. Making sure the procedures are in place to manage the effects of, say, a CA revoking a certification or determining when and how to renew any certifications that are about to expire is a part of this process.
- Regularly update user permissions. Access management mistakes can have severe results. If a person is no longer in a position that calls for them to have access, they shouldn’t still have it.
- For cert-based authentication, use a thorough management tool. The complete IT environment, including all of its digital certificates and keys, should be visible through certificate managers. Additionally, they must to provide a single platform for managing certificate lifecycles.
ad


Comments are closed.