What Is Botnet and How it Works
A botnet consists of Internet-connected devices that each execute bots. Botnets can be used to launch DDoS assaults, steal data, send spam, and access a device's connection. C&C software lets the owner control the botnet. "Botnet" combines "robot" with "network." The word is often used maliciously.
The word ‘botnet’ is much popular to industry experts who deal with the execution and monitoring of system security measures. If a restorative and robust system is to be established, the word “botnet,” which is frequently used for a chain of computers or systems that have been hijacked, should be fully understood. The incorrect use of these systems can lead to an incredible amount of confusion.
In this article I will explain everything about botnet, it’s working methodology and how to prevent yourself being a prey. Keep reading!
ad
What is botnet?
By definition, a botnet is a network of infected or taken over computers that are used to do things like send spam emails, spread malware, and set up DDoS attacks. The owner of a device is not required to give permission for a botnet to be turned on.
Botnets are not bad for the network by themselves, and they can be used for important tasks like managing chat rooms and keeping track of points in online games. The person in charge of the botnet is called a “bot-herder,” and each machine that is part of the network is called a “bot.”
ad
The main reason people put together botnets is to make boring tasks easier than ever. The best example of this kind of chatroom management is when it gets rid of people who don’t follow the rules. Botnets keep track of the language used in chats, which would be too hard for people to do on their own.
But some smart people have figured out how to use it badly by taking advantage of the fact that it can run code smoothly inside another system. Because of these features, hackers and other attackers were able to use it to steal passwords and track what keys were pressed on a device.
How does botnet work?
Now that you have a good idea of what a botnet is, it’s time to find out more about how it works. To start a botnet attack, the following steps must be taken:
Ready for wide spread attack: The first step in making a botnet is to infect as many connected devices as possible, so that there are enough bots to carry out the attack. It uses the power of the devices it has infected to do things that the owners of the devices don’t know about. But the amount of bandwidth that can be taken from a single computer isn’t enough, so the Botnet uses millions of devices to launch large-scale attacks. It makes bots this way by taking advantage of security holes in software or websites or by sending phishing emails. They often use a trojan horse virus to set up botnets.
Connection setting up: After hacking the device, as described in the previous step, it infects it with a specific piece of malware that connects the device back to the central botnet server. So, it connects all the devices in the botnet network, and they are ready to launch the attack. A bot herder tells the bot what to do by programming commands.
The attack: Once infected, a bot gives admin-level access to things like gathering and stealing user data, reading and writing system data, watching user activities, performing DDoS attacks, sending spam, launching brute force attacks, crypto mining, and so on.
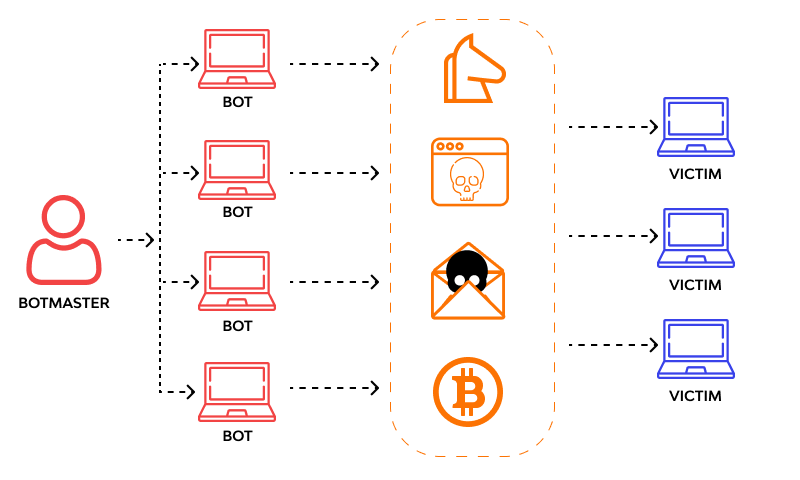
As you can see in the image above, a bot herder starts the attack by putting malicious code on several devices. These devices work together as the Botnet. The next step is for these devices to take over and do the last cyber attack. So, even if you can figure out where the cyberattack came from, it won’t be easy to find the bot herder.
In the next part of this tutorial about what a botnet is, you will learn more about botnets and look at how they are put together.
| Read more: What is trojan horse and how to prevent it
The main purpose of botnets
Depending on what the attackers want to do, botnets can be used in many ways to steal money or information. This is the most common way that botnets are used.
Theft of data to gain ransom
User data is very valuable on the market, and hackers use botnets to steal personal information or break into a business’s database. Later, they sell information about users to third parties to make money. These botnets do nothing but steal personal information while they sleep.
Online frauds to steal money
A botnet can be used to directly or indirectly steal money in an attack. Key ways to reach this goal are to send phishing emails or make a fake website for a bank. They can translate the information about the payment or transaction and use it to steal money.
Spamming and phishing frauds
With botnets, scammers can send spam emails and phishing emails to millions of people at once. There are spam botnets that are made to do this job.
No matter what method is used, the goal is the same: to steal money or information. But some attackers can use botnets just because they can. They use botnets to show off their skills and show the world how good they are. We have seen many security breaches happen when bad people steal business data and put it up for free on the dark web.
Mining for cryptocurrency
Cryptocurrency has become very popular, and attackers can use botnets to mine cryptocurrency. This is called “cryptojacking.”
| Read more: Best antivirus software for Windows Pc
Types of botnet attacks
Phishing
Phishing is one of the most common botnet attacks. It involves bad actors or hackers pretending to be trustworthy sources to get people to give them important information like passwords and banking credentials. Bad people can use these details to steal data and money. The attack is done in a number of ways, such as through phishing, vishing, and smishing. Spear and whale phishing are two methods of phishing that are often used to attack a large number of people.
DDoS
Known as Distributed Denial-of-Service attack, is when someone messes with a server’s normal traffic flow in such a way that real or intended users can’t get to the website. The attack works because it uses different systems that have been hacked to send out annoying traffic. It could be computers, PCs, IoT devices, and many other data-driven devices that have been hacked.
From another point of view, a DDoS attack can look like a traffic jam that was made on purpose to keep people from getting to their destinations.
Brute Force Attacks
The brute force attack is based on guessing and is the cause of more than 5% of all security breaches. The threat actor keeps trying different user credentials until he or she finds the right ones and gets unauthorized access to the system being targeted. This is a good place to use the Hit and Trial method. The process is easy and more likely to work. There are also tools that use brute force to do the job.
| Read more: What is a phishing and how to protect yourself
The botnet architecture
Over time, a botnet’s architecture has changed to make it work better and make it harder to track down. As we’ve seen, once it infects the number of devices that the botmaster wants, he or she can take control of the bots in two ways.
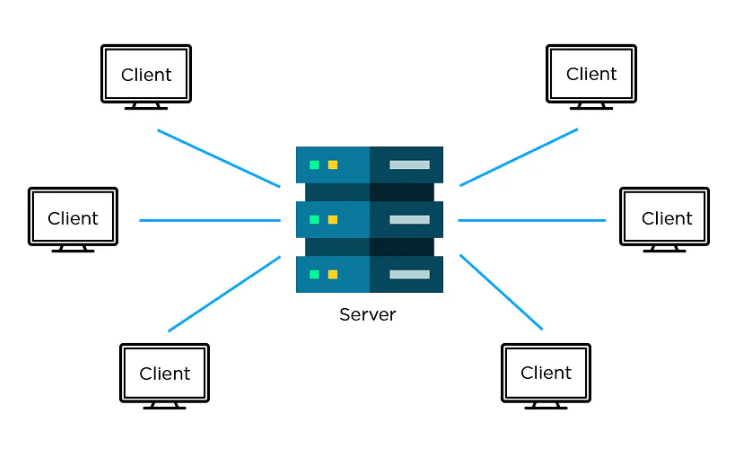
Client-Server Model
The client-server model is an old one that uses a command and control (C&C) server and communication protocols like IRC to work. IRC, or Internet Relay Chat, sends automated commands to bot devices that have been infected.
Before launching an attack, it often tells the bots to stay inactive and wait for instructions from the C&C server. When the bot herder sends a command to the server, it is sent to the clients. The clients then run the commands and send the results back to the bot herder.
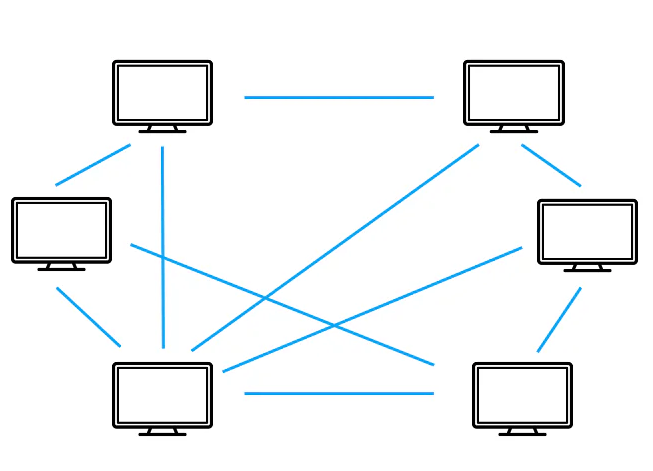
P2P Botnet
Instead of C&C servers, we use P2P, or peer-to-peer. In this case, infected bots are controlled by a peer-to-peer network that uses a decentralized method. As you can see in the picture above, bots are connected in a topological way and work as both C&C servers and clients. Today, hackers do this to avoid being caught and having a single point of failure.
In P2P botnets, the devices that have been infected look for malicious websites or other devices. The bot carefully checks out different IP addresses until it finds another infected computer. The bots then share updated commands or the newest versions of the malware.
The next part of this guide on what a botnet is will tell you about some of the most well-known botnets ever.
Well-known Botnet Attacks
You can see how dangerous a botnet can be now that you know how it works. Several dangerous cyber attacks are caused by networks of devices that have been taken over. You will now take a look at a few botnets that are very advanced.
Zeus
At its peak, this financial Trojan was responsible for 90% of all online bank fraud around the world. When it first appeared in July 2007, it was used to steal information from the US Department of Transportation.
Mirai
Mirai is a well-known botnet that is linked to Internet of Things (IoT) devices. It was found for the first time in 2016, and since then it has been used in some of the most disruptive DDoS attacks.
3ve
It was a different kind of Botnet that wasn’t found until 2016. It didn’t steal data or money, but instead made fake clicks on online ads hosted by fake websites.
Mariposa
Mariposa was first seen in 2009, and it was used to run scams online and launch DDoS attacks. It also stole the login information for victims’ personal accounts so that its operators could sell the information on the Dark Web.
Storm
Storm was one of the first P2P botnets. It was discovered in 2000 and had anywhere from 250,000 to 1 million infected devices. Attacks like DDoS and identity theft were dealt with by the Storm.
These are some of the most harmful and destructive botnets in history. So, in the next part of this tutorial on what a botnet is, you’ll find out how to protect yourself from an attack by a botnet.
How to keep Botnets away from you
To avoid getting infected by a botnet, you need a complete plan that includes things like good surfing habits, software updates, and anti-virus protection. Here are some important things to do to keep botnets away.
- Keeping your operating system up to date is a good way to avoid malware.
- Watch out for phishing emails and don’t open email attachments from people you don’t know.
- Don’t click on links that look sketchy, and be careful about which site you use to download things.
- Put firewalls, anti-virus software, and anti-spyware software on your computers.
- If you own a website, you should set up a way to verify users with more than one factor and install DDoS protection tools. This will protect your website from attacks by botnets.
If you do these things, hackers won’t be able to get into your network or devices. This is the end of this lesson on what a botnet is.
ad



Comments are closed.