What is a DDoS attack And How To Prevent It?
DDoS attacks are a major concern in today's Internet security. Learn more about how DDoS attacks work and how to prevent them.
A distributed denial-of-service (DDoS) attack is an attempt to stop normal traffic on a server, service, or network by flooding it with so much Internet traffic that it or the infrastructure around it can’t handle it.
DDoS attacks work because they use multiple computers that have been hacked as sources of attack traffic. Computers and other networked resources, like Internet of Things (IoT) devices, can be exploited machines.
At a high level, a DDoS attack is like an unexpected traffic jam that stops regular traffic from getting where it needs to go.
Recorded 2.9 million DDoS attacks in the first quarter of 2021. This is 31% more than in the same quarter of 2020. In Q1 2021, there were 2.9 million DDoS attacks, which is 31% more than in the same quarter of 2020.
DDoS attacks are one of the most feared types of cyberattacks, and for good reason. If a DDoS attack is done well, it can be almost impossible to stop and very hard to stop. They can start at any time and make even the most advanced IT companies’ servers useless. In 2018, GitHub was hit by the biggest DDoS attack ever, which sent over 120 million data packets per second to their servers.
No matter how big or small an attack is, the main idea is always the same. Send more requests to a server than it can handle. Keep doing this until it either stops working or crashes. Service disruptions often take hours to fix, which costs a lot of money.
How a DDoS attack works?
Instead of going into technical details, let’s think about a comparison. Let’s say you own a place where people can pick up burgers. People call in their orders and pick them up when they’re ready. One day, a prankster calls your place several times to order a total of 100 burgers.
This should keep all of your cooks busy, so you don’t need to take any more orders. But the jokester never takes the burgers. Not only did you waste all your time and money on fake orders, but you also couldn’t help real customers.
This can be annoying, but it’s easy to stop since one person is giving all the wrong orders. You can just block their number, which will solve the problem. A server can also have the same thing happen. One bad client can send a server a lot of fake requests, making it hard for the server to respond to real users.
But, just like in our example, it’s easy for the server to figure out that one client is a fake. All it has to do is block all requests from that client. This kind of attack is called a denial-of-service (DoS) attack, and it was the first step toward what we now call DDoS attacks.
Now, let’s say that several jokers are calling your burger place. Your landline phone never stops ringing, and it’s almost impossible to tell who is real and who isn’t. You also can’t just block phone numbers, since some of them might belong to real customers. Your whole operation has stopped. This is what happens when a DDoS attack happens to a server. Hackers send fake traffic from multiple computers that looks just like real traffic. This causes a server, network, or website to break down.
Top Reasons Of DDoS attack
Some of the most common reasons why DDoS attacks happen are:
- Ransom: After a DDoS attack, attackers usually ask for money. But sometimes an attack can be planned ahead of time by sending a ransom note.
- Hacktivism: DDoS attacks can also be used to get a message across. Hacktivists can use a DDoS attack to show how they feel about a law, a person, or a business.
- Competition: A survey from 2017 showed that more than 40% of companies that had a DDoS attack blamed it on their competitors. This seems even more likely now that a week-long DDoS attack can be bought for only $150.
📚 Also Read: What is Hacktivism?
Types of DDoS attacks
Even though the end goal of a DDoS attack is always to overwhelm the system, the ways to get there can be different. There are three main types of DDoS attacks.
1. Attacks on the application layer
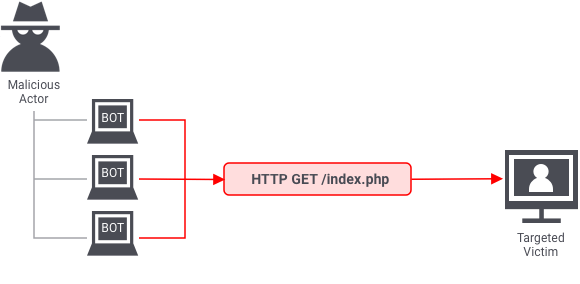
In the application layer, the server makes a response to a request from a client. For instance, if a user types http://www.xyz.com/learning/ into their browser, an HTTP request for the learning page is sent to the server. The server will get all the information about the page, put it in a response, and send it back to the browser.
The application layer is where this information is gathered and put together. An application layer attack happens when a hacker uses multiple bots or machines to ask the server for the same resource over and over again, until the server can’t handle it anymore.
HTTP flood attacks are the most common type of application layer attack. In these attacks, bad actors keep sending different HTTP requests to a server from different IP addresses. One example of this is asking a server over and over again to make PDF files. The server can’t tell that it’s being attacked because the IP address and other identifiers change with every request.
2. Protocol attacks

Protocol attacks try to use up all of a server’s resources or those of its networking systems, like firewalls, routing engines, or load balancers. The SYN flood attack is a type of protocol attack.
Before two computers can start talking to each other securely, they have to do a TCP handshake. A TCP handshake is a way for two parties to share basic information with each other. Usually, the first step of the TCP handshake is the SYN packet, which tells the server that the client wants to start a new channel.
In a SYN flood attack, the attacker sends a lot of SYN packets to the server, all of which have fake IP addresses. Through SYN-ACKs, the server responds to each packet and asks the client to finish the handshake. But the client(s) don’t answer, so the server keeps waiting. It crashes in the end because it waited too long for too many responses.
3. Volumetric attacks
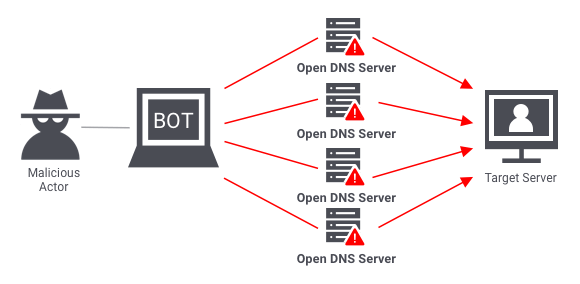
Volumetric attacks are done by sending so much traffic to a server that it can no longer handle any more. The DNS amplification attack is the most common type of volumetric attack.
In this kind of attack, the spoofed IP address of the target is used to send requests to a DNS server. The DNS server then sends the target server its response. When done on a large scale, the flood of DNS responses can mess up the server being targeted.
How To Stop an in Progress DDoS Attack?
To stop a DDoS attack, you need to know what the most common signs are.
Typical signs of a DDoS
- A lot of traffic from clients who are the same or have similar traits. Such as type of device, type and version of browser, IP or IP range, location, etc.
- A sudden, sharp increase in the amount of traffic at a single endpoint or server.
- A server keeps going down for no apparent reason.
- It takes too long for your site to respond to requests.
How to deal with a DDoS attack
Once you know you’re under a DDoS attack, you need to act quickly so you can keep your site from going down for a long time. If you wait too long, your server might start to crash, and it might take hours to fix everything.
The hardest thing about stopping a DDoS attack is that it’s often almost impossible to do so without affecting normal traffic. This is because attackers go to a lot of trouble to make fake traffic look like real traffic. So, here are some things you can say in response:
- Blackhole filtering: Look at the traffic coming in and choose a way to limit it. Use the criterion to send bad traffic to a blackhole, which is basically the same as dropping it.
- Casting: Spread the traffic across multiple servers to increase your capacity and make it less likely that one server will get too busy.
- IP Blocking: If you see a lot of traffic from the same range of IP addresses that you didn’t expect, block them.
📚 Also Read: Your IP Has Been Temporarily Blocked: Tricks to Unblock It
Do you have to report the breach?
According to GDPR, if your breach puts people’s rights and freedoms at risk, you must tell the Information Commissioner’s Office (ICO). If you think the risk is low, you don’t have to tell anyone about it. But if you decide not to report a breach, you should write down why, because you might be asked to explain it later.
How to Stop a DDoS Attack
Stopping a DDoS attack in progress can be hard and could affect your real users. This is why it’s important to try to stop problems before they happen. In addition to the precautions listed below, you should also make a plan for how to handle a DDoS attack in an emergency, since even the best defenses can sometimes be beaten by sophisticated attacks.
- Real-time packet analysis: Means analyzing packets as they come into your system based on different rules and getting rid of the ones that could be harmful.
- DDoS defense system (DDS): A DDS can find content that looks legitimate but is actually harmful. It protects against both protocol attacks and volumetric attacks without any help from a person.
- Web application firewalls (WAF): They are a great way to protect against application layer DDoS attacks. They give you a way to sort incoming requests based on different rules, which can also be added on the fly in response to an attack.
- Rate limiting: Set a limit on how many requests a server can handle in a certain amount of time.
More Information
DOS vs DDOS attacks: What are the differences
- DOS Attack is a denial of service attack. In this attack, a computer sends a lot of traffic to a victim’s computer and shuts it down. When done on a website, a DoS attack is used to stop users from being able to use the site. This attack works by sending a lot of traffic to the server of a website that is connected to the internet.
- “DDOS Attack” means “distributed denial of service.” In this attack, “dos attacks” are done from many different places using many systems.
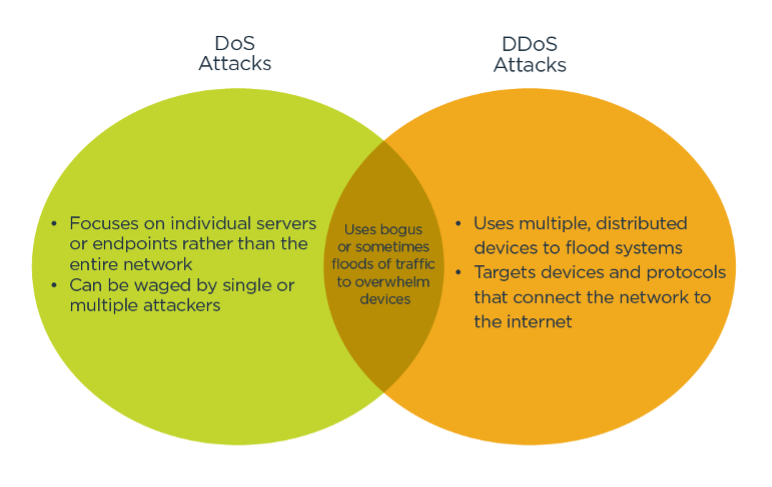
Difference between DOS and DDOS attacks:
| DOS | DDOS |
|---|---|
| DOS Stands for Denial of service attack. | DDOS Stands for Distributed Denial of service attack. |
| The victim system is attacked by a single system in a DOS attack. | In DDoS, several systems attack the system that is being attacked. |
| The data sent from a single location is used to load the victim’s PC. | The data packets sent from different places are used to load the victim’s computer. |
| Dos attack is slower as compared to DDoS. | DDoS attack is faster than Dos Attack. |
| Can be blocked easily as only one system is used. | It is difficult to block this attack as multiple devices are sending packets and attacking from multiple locations. |
| DOS Attack tools can only be used on a single device. | The volumeBots are used in a DDoS attack to attack at the same time. |
| DOS Attacks are Easy to trace. | DDOS Attacks are Difficult to trace. |
| Volume of traffic in the Dos attack is less as compared to DDos. | With a DDoS attack, the attacker can send a lot of traffic to the network that is being attacked. |
| There are different kinds of DOS attacks, such as:
1. Buffer overflow attacks 2. Ping of Death or ICMP flood 3. Teardrop Attack 4. Flooding Attack |
Types of DDOS Attacks are:
1. Volumetric Attacks 2. Fragmentation Attacks 3. Application Layer Attacks 4. Protocol Attack. |
DDoS Attack History
In 1974, David Dennis, then 13 years old and a student at University High School across the street from the Computer-Based Education Research Laboratory (CERL) at the University of Illinois Urbana-Champaign, launched the first DoS attack. David just found out that the PLATO terminals at CERL can run a new command. PLATO was one of the first computerized learning systems that more than one person could use at the same time. It was also one of the first multi-user computer systems. The command, which was called “ext” or “external,” was meant to make it possible to talk to external devices that were connected to the terminals. But if it was run on a terminal with no external devices attached, it would lock up the terminal and make it useless until it was shut down and turned back on.
Some of the famous DDoS attacks in the recent past
In the past few years, DDoS attacks have become much more common and have shut down businesses for long periods of time.
- In February 2020, Amazon Web Services (AWS) was hit by a sophisticated DDoS attack that kept its incident response teams busy for a few days and affected customers all over the world.
- In February of 2021, the EXMO Cryptocurrency Exchange was hit by a DDoS attack that shut it down for nearly five hours.
- Australia was recently hit by a large, long-lasting, state-backed DDoS attack.
- Belgium was also hit by a DDoS attack, which went after the country’s parliament, police, and universities.
Every day, there are hundreds of thousands of DDoS attacks that don’t have names or records, but are still successful. In fact, these are the attacks that do the most damage and cost the most money. The rise in DDoS attacks is likely to continue, which will make IT professionals with skills to stop them very valuable.
ad



Comments are closed.