What is a Web Application Firewall (WAF)?
A web application firewall (WAF) serves to safeguard web applications against a range of application layer attacks, including cross-site scripting (XSS), SQL injection, and cookie poisoning, among others. Application breaches stand as the primary source of security incidents, acting as the entry point to compromise valuable data. By implementing an effective WAF, you can thwart various attacks that seek to extract data by compromising your systems.
ad
How does a web application firewall (WAF) work?
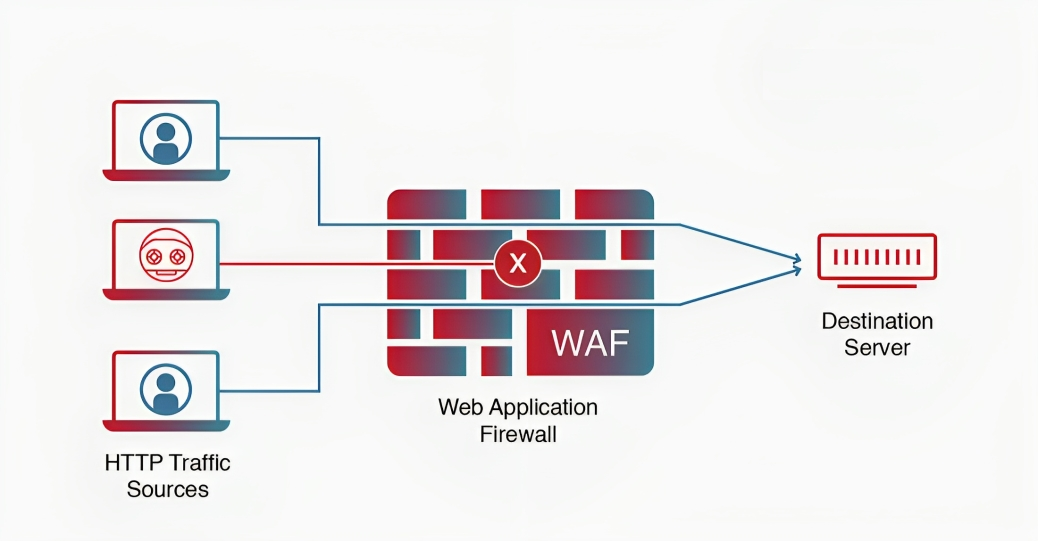
A Web Application Firewall (WAF) plays a crucial role in securing your web applications. It accomplishes this by filtering, monitoring, and blocking any malicious HTTP/S traffic directed towards the web application, and it ensures that unauthorized data cannot leave the application. The WAF achieves this by following a set of policies that determine the nature of traffic, distinguishing between malicious and safe data. Acting as a reverse proxy, much like a proxy server protects a client’s identity, the WAF operates as an intermediary to shield the web app server from potential threats posed by malicious clients.
WAFs are available in different forms, including software, appliances, or as-a-service, offering flexibility in implementation. Customizable policies cater to the specific needs of your web application(s). While many WAFs require regular policy updates to address emerging vulnerabilities, some leverage machine learning advancements to update automatically. This automated feature becomes increasingly critical in the face of a growing threat landscape marked by complexity and ambiguity.
The difference between a web application firewall (WAF), an intrusion prevention system (IPS) and a next-generation firewall (NGFW)
ad
An Intrusion Prevention System (IPS) serves as a comprehensive security product, employing a signature and policy-based approach to identify well-known vulnerabilities and attack vectors through a signature database and established policies. It establishes a standard based on these elements and issues alerts when traffic deviates from this norm. While primarily operating at layers 3 and 4, some IPS solutions may offer limited protection at the application layer (layer 7), safeguarding traffic across various protocol types such as DNS, SMTP, TELNET, RDP, SSH, and FTP.
A Web Application Firewall (WAF) specializes in protecting the application layer, meticulously analyzing each HTTP/S request at that level. It is typically user, session, and application-aware, understanding the web apps it protects and their associated services. Serving as an intermediary between users and apps, a WAF scrutinizes all communications before reaching the app or the user. Traditional WAFs ensure that only allowed actions, in accordance with the security policy, can be executed. They are often considered a trusted first line of defense for applications, particularly against the OWASP Top 10, a foundational list of commonly observed application vulnerabilities.
- Injection attacks
- Broken Authentication
- Sensitive data exposure
- XML External Entities (XXE)
- Broken Access control
- Security misconfigurations
- Cross Site Scripting (XSS)
- Insecure Deserialization
Conversely, a Next-Generation Firewall (NGFW) monitors outbound Internet traffic, covering websites, email accounts, and SaaS. Its primary focus is on protecting the user rather than the web application. An NGFW enforces user-based policies, adds context to security policies, and includes features like URL filtering, anti-virus/anti-malware, and potentially its own Intrusion Prevention Systems (IPS). Unlike a WAF, typically a reverse proxy used by servers, NGFWs often function as forward proxies used by clients like browsers.
The different ways to deploy a WAF
The deployment of a WAF can take various forms, contingent on factors such as the location of your applications, required services, preferred management approach, and the desired level of architectural flexibility and performance. Consider whether self-management is preferable or if outsourcing is a more suitable option. Additionally, weigh the advantages of a cloud-based solution against an on-premises WAF. Your deployment preferences play a crucial role in determining the most suitable WAF for your needs. The following options outline your choices.
WAF Deployment Modes:
- Cloud-based + Fully Managed as a Service: This presents an excellent choice if you seek the quickest and most straightforward method to deploy a WAF for your applications, particularly if your in-house security/IT resources are limited.
- Cloud-based + Self Managed: Enjoy the flexibility and security policy portability of the cloud while retaining control over traffic management and security policy settings.
- Cloud-based + Auto-Provisioned: This option offers the easiest way to initiate a WAF in the cloud, deploying security policies in a straightforward and cost-effective manner.
- On-premises Advanced WAF (virtual or hardware appliance): This option caters to the most demanding deployment requirements where flexibility, performance, and advanced security considerations are mission-critical.
Benefits of using a WAF
- Prevents Exploitation of Known Vulnerabilities: WAFs can hinder attacks that exploit recognized vulnerabilities in web applications.
- Guards Against Zero-Day Attacks: WAFs can employ machine learning to identify and thwart zero-day attacks, targeting vulnerabilities not yet known to the security community.
- Mitigates Data Breach Risks: WAFs contribute to preventing data breaches by obstructing attacks designed to illicitly access and steal data.
- Enhances Website Performance: WAFs play a role in improving website performance by obstructing malicious traffic, thereby preventing slowdowns.
- Eases Security Team Responsibilities: WAFs assist in alleviating the workload on security teams by automating the detection and prevention of malicious traffic.
FAQ’s
How does a web application firewall (WAF) work?
A WAF operates by filtering, monitoring, and blocking malicious HTTP/S traffic directed towards a web application. It follows a set of policies to distinguish between malicious and safe data, acting as a reverse proxy to shield the web app server from potential threats.
What forms do WAFs come in, and how do they differ in implementation?
WAFs are available as software, appliances, or as-a-service, offering flexibility. Customizable policies cater to specific web application needs. Some WAFs require regular policy updates, while others use machine learning to update automatically, addressing emerging vulnerabilities.
What distinguishes a WAF from an Intrusion Prevention System (IPS) and a Next-Generation Firewall (NGFW)?
A WAF specializes in protecting the application layer, serving as an intermediary between users and apps. IPS focuses on comprehensive security through signature and policy-based approaches. NGFW monitors outbound Internet traffic, emphasizing user protection over web application security.
What are the deployment options for a WAF?
Deployment options vary based on application location, required services, and management preferences. Choices include Cloud-based + Fully Managed as a Service, Cloud-based + Self Managed, Cloud-based + Auto-Provisioned, and On-premises Advanced WAF (virtual or hardware appliance).
How does a WAF benefit web applications and security teams?
WAFs offer benefits such as preventing exploitation of known vulnerabilities, guarding against zero-day attacks using machine learning, mitigating data breach risks, enhancing website performance by blocking malicious traffic, and easing the workload on security teams through automated detection and prevention.
Conclusion
Web Application Firewall (WAF) plays a critical role in defending web applications from diverse cyber threats. Its capabilities in preventing breaches, improving website performance, and automating security tasks highlight its importance in modern cybersecurity. The diverse deployment options and benefits make WAF a key component in securing digital assets against evolving threats, ensuring a robust defense for web applications in today’s complex digital landscape.
ad


Comments are closed.