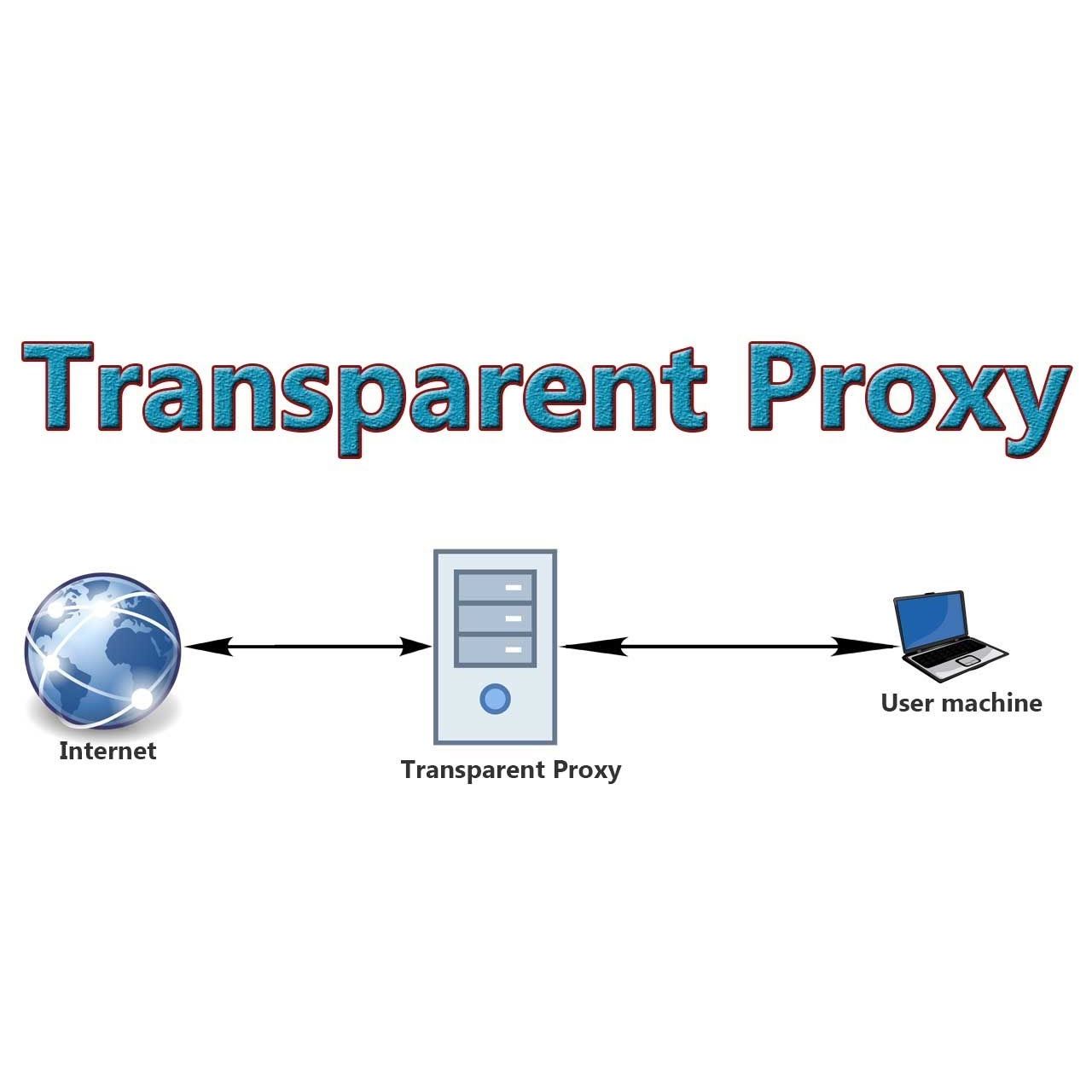
What exactly is a transparent proxy? It functions as an intermediary server situated between a user’s device and the website they’re attempting to reach. Nevertheless, a transparent proxy server doesn’t alter requests. This is the differentiating factor between an HTTPS transparent proxy and a non-transparent one, as the latter alters a device’s requests to a website.
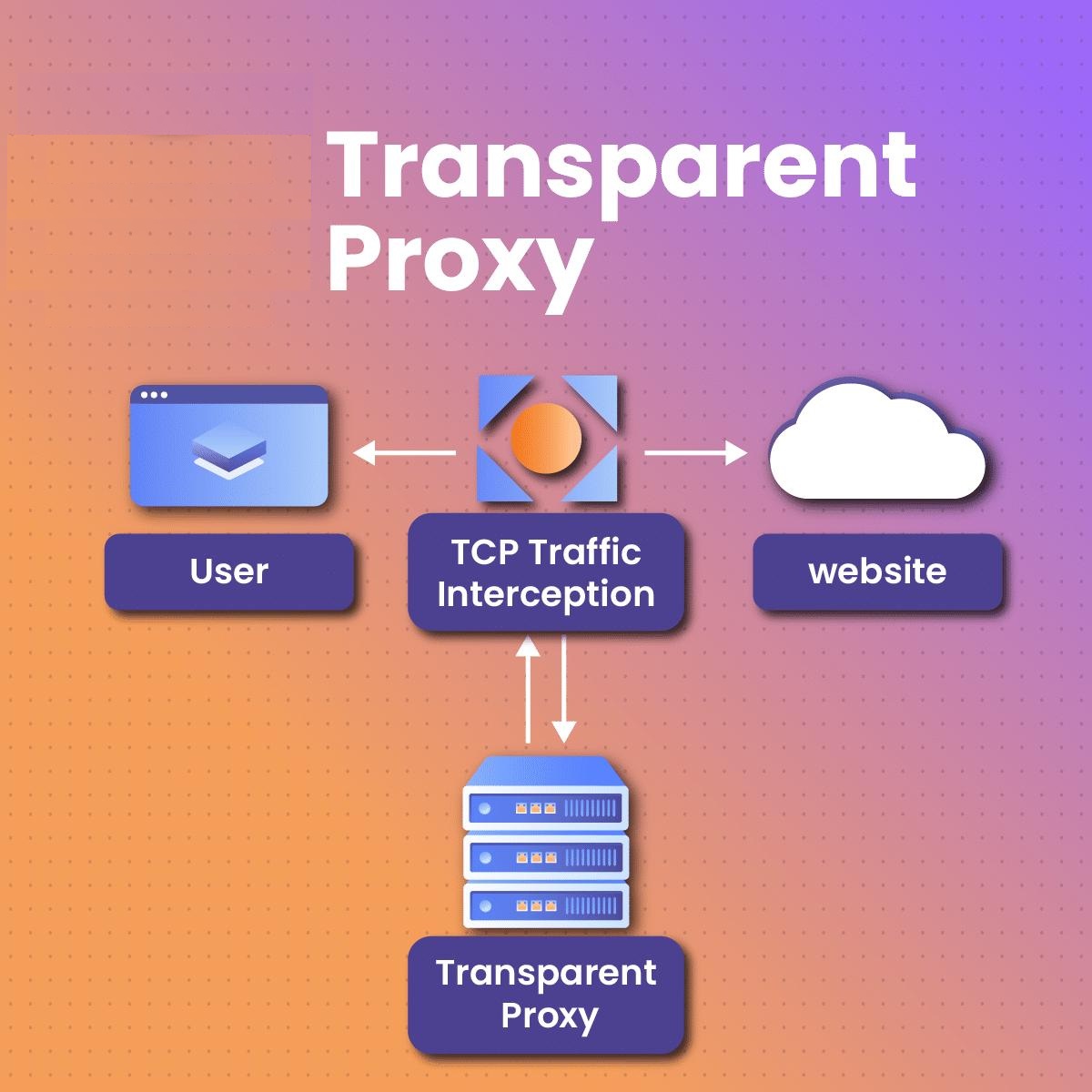
How Does a Transparent Proxy Work?
A transparent proxy can be set up without your knowledge or any input from your end regarding software or configurations. It’s often referred to as a “forced proxy” because it can be imposed by a webmaster or an internet service provider (ISP) without users being informed.
These proxies act as intermediaries between clients and the internet, intercepting connections.
When utilizing a transparent proxy, the user’s actual IP address is disclosed in the HTTP header. Such a proxy only authenticates and identifies your connection; it does not shield or modify your IP address.
Why Do Companies Use a Transparent Proxy?
After a transparent proxy has been established, it’s commonly employed for content filtering purposes. For instance, parents might utilize it to block their children from accessing inappropriate websites. Similarly, in a corporate setting, it can restrict access to specific websites—whether due to containing harmful content or posing a distraction to employees. IT administrators may be tasked with implementing a transparent proxy for such purposes.
Furthermore, a transparent proxy can be utilized to thwart distributed denial-of-service (DDoS) attacks, which seek to overwhelm a website or web application with an avalanche of requests. This is feasible because a transparent proxy can identify suspicious requests based on their origin or volume and subsequently deny them until the security team resolves the attack.
Transparent Proxy for Secure Email
Another application of a transparent proxy is to monitor email content and encrypt it to prevent unauthorized access. This involves examining the content of emails as they are transmitted to and from the end user. If the transparent proxy identifies any malicious or suspicious content, it can discard the email, thereby preventing its delivery.
Transparent Proxy vs. Non-Transparent Proxy
| Transparent Proxy | Non-transparent Proxy | |
|---|---|---|
| Configuration | Once configured on the network, it’ll handle incoming traffic automatically. | Needs to be configured on each device. |
| Privacy | The client’s IP address and geo-location are visible. | The client’s IP address and geo-location are concealed. |
| Awareness | The client is unaware of the proxy. | The client is aware of the proxy and is usually the one to set it up. |
| Request modification | The proxy doesn’t modify the client’s requests. | The proxy modifies the client’s requests. |
Use Cases for Transparent Proxy
Transparent proxies have a variety of uses, including:
Content Filtering or Censorship
Transparent proxies are often employed to filter or censor content, commonly by governmental organizations, businesses, and educational institutions. They block access to specific internet domains, presenting users with error messages if they attempt to access restricted websites. These messages can be customized by the organization managing the transparent proxy, making it difficult for users to determine if their access was restricted. This discreet censorship effectively prevents users from accessing potentially harmful sites without their awareness.
Authentication Gateway
Transparent proxies also serve as authentication gateways. When users are redirected to a different web page than their intended destination and prompted for authentication credentials, they are interacting with a transparent proxy. The proxy intercepts the user’s request, verifies their authorization, and grants access accordingly.
Web Caching
Transparent proxies are commonly used for web caching to reduce bandwidth usage for internet service providers (ISPs). Web caching involves storing frequently accessed data within the proxy’s cache. When a user requests this content, the proxy retrieves it from the cache instead of fetching it from the original web server. This results in faster content delivery and bandwidth savings for the ISP.
Advantages and disadvantages of transparent proxies
Like many technologies, transparent proxies have their advantages and disadvantages. Here are some of the key points:
Advantages of transparent proxies
- Content Filtering: Transparent proxies allow you to restrict access to certain websites and filter out harmful content by implementing and configuring them.
- Data Compression: Due to their caching and data compression features, transparent proxies efficiently deliver the same content to multiple users, making them beneficial for improving network performance, particularly in businesses.
- Gateway Proxy Functionality: Transparent proxies can be set up to block undesirable traffic based on predefined rules, making them effective tools for preventing access to hazardous or distracting websites.
- Latency Reduction: Transparent proxies are favored by many providers for their ability to reduce latency and enhance transmission bandwidth. This is achieved through caching web content and delivering it to users more swiftly.
- DDoS Security: Moreover, transparent proxies help protect servers from Distributed Denial of Service (DDoS) attacks by acting as a buffer against botnets that inundate websites or web applications with unwanted requests.
Disadvantages of transparent proxies
- Potential Network Issues from Misconfiguration: Incorrect setup or configuration of a transparent proxy can significantly hinder network performance. Improper caching and traffic redirection settings may lead to connection failures and sluggish speeds.
- Interception of Traffic and Privacy Concerns: Transparent proxies intercept all network traffic, making them susceptible to eavesdropping, especially if the proxy is compromised by a hacker. A breach could expose vast amounts of sensitive data to unauthorized access.
- Risk of Data Breaches: In the event of a breach in your transparent proxy, hackers could exploit it to extract valuable information from your organization, posing a significant risk of data leaks.
How To Detect and Bypass a Transparent Proxy
When contemplating how to detect a transparent proxy, it’s essential to note that while some proxies are easily identifiable based on their configuration, others operate covertly, making them more challenging to discern.
One indicator of traffic passing through a transparent proxy is if it’s rerouted to a different site before reaching its intended destination. For instance, if you encounter unexpected login prompts while attempting to access a website over a public Wi-Fi network, it likely indicates interaction with a transparent proxy.
To evade a transparent proxy, you might need to switch to an alternative network. For example, if your workplace’s transparent proxy blocks access to specific websites, connecting to a different network can bypass these restrictions.
Imagine you’re trying to stream a training video hosted on a company server, but the transparent proxy prevents access. By connecting to a personal mobile hotspot, you can bypass the proxy and access the video directly from the company server.
FAQ’s
What is a transparent proxy and how does it work?
A transparent proxy serves as a mediator between a user’s device and the website they’re trying to access. Unlike other proxies, it doesn’t alter requests, maintaining the original data flow. This distinction is particularly noticeable when comparing it to HTTPS transparent proxies, which do not modify user requests.
How can I detect if a transparent proxy is in use?
Transparent proxies can be detected by observing any rerouting of traffic to different sites before reaching the intended destination. For instance, encountering unexpected login prompts while accessing a website over public Wi-Fi could indicate interaction with a transparent proxy.
Can transparent proxies compromise privacy?
While transparent proxies don’t modify user requests, they intercept all network traffic, raising privacy concerns. If compromised by a hacker, they could be exploited for eavesdropping, potentially exposing sensitive data to unauthorized access.
How can I bypass a transparent proxy?
Bypassing a transparent proxy may involve switching to an alternative network. For example, if your workplace’s transparent proxy restricts access to certain websites, connecting to a different network can circumvent these restrictions. Additionally, utilizing a personal mobile hotspot can help bypass the proxy and access restricted content directly from the source.
What are the advantages and disadvantages of using transparent proxies?
Advantages include efficient content filtering, data compression, reduced latency, and enhanced DDoS security. However, potential disadvantages such as network issues from misconfiguration, interception of traffic leading to privacy concerns, and the risk of data breaches should also be considered.
Conclusion
Transparent proxies serve as vital tools for network management, offering benefits like content filtering and enhanced security. While they provide valuable functionalities, careful consideration is needed to avoid potential drawbacks such as misconfiguration and privacy concerns. Despite challenges, transparent proxies remain essential for optimizing network performance and ensuring secure communication. Understanding their capabilities and limitations allows businesses to leverage them effectively while safeguarding against risks.