E-Commerce Security Threats and Their Solutions
The impact of e commerce security risks is undeniably significant when it comes to transactions as they cause a great […]
/* --- top bar --- */
.dz-top-bar{
background:#212121;
display:flex;
justify-content:space-between;
align-items:center;
padding:15px 20px;
}
.dz-logo-wrapper{flex-grow:1;display:flex;justify-content:flex-start;}
.dz-logo{
color:#fff;
font-size:24px;
font-weight:700;
letter-spacing:1.5px;
position:relative;
left:34%; /* move logo to align "A" above 'o' of Windows */
}
.dz-ad-slot{
background:#333;
color:#aaa;
display:flex;
justify-content:center;
align-items:center;
width:728px;height:90px;
font-size:16px;
border:1px solid #444;
border-radius:4px;
}
/* --- main menu --- */
.dz-menu{
display:flex;
justify-content:center;
flex-wrap:wrap;
padding:8px 0;
background:#0d47a1;
}
.dz-menu-item{
color:#fff;
text-decoration:none;
padding:8px 15px;
font-size:14px;
font-weight:500;
border-radius:4px;
transition:background .2s,color .2s;
margin:0 4px;
}
.dz-menu-item:hover,
.dz-menu-item.active{
background:#1e88e5;
}
/* --- dropdown bar --- */
.dz-dropdown-content{
position:absolute;
top:100%;
left:0;
width:100%;
height:0;
overflow:hidden;
background:#212121;
box-shadow:0 4px 6px rgba(0,0,0,.3);
z-index:999;
transition:height .2s ease-out;
}
.dz-dropdown-content.open{
height:auto;
min-height:45px;
display:flex;
padding:10px 0;
}
/* --- dropdown panels --- */
.dz-dropdown-panel{
display:none;
width:100%;
justify-content:center;
flex-wrap:wrap;
padding:0 20px;
}
.dz-dropdown-panel.active{display:flex;}
.dz-dropdown-panel a{
color:#e0e0e0;
text-decoration:none;
padding:5px 15px;
margin:5px 10px;
font-size:13px;
border-radius:4px;
transition:background .2s,color .2s;
}
.dz-dropdown-panel a:hover{
color:#fff;
background:#424242;
}
/* grouped headings */
.dz-subgroup{
display:flex;
flex-direction:column;
align-items:flex-start;
margin:0 25px;
min-width:180px;
}
.dz-subgroup h4{
color:#fc8c1e;
font-size:13px;
font-weight:600;
margin-bottom:6px;
text-transform:uppercase;
letter-spacing:.5px;
}
/* responsive */
@media(max-width:1100px){
.dz-ad-slot{display:none;}
.dz-logo-wrapper{justify-content:center;}
.dz-logo{left:0;}
.dz-top-bar{justify-content:center;}
}
@media(max-width:600px){
.dz-menu{flex-wrap:wrap;}
.dz-menu-item{font-size:12px;padding:6px 10px;margin:2px;}
}
document.addEventListener("DOMContentLoaded",()=>{ const triggers=document.querySelectorAll(".dz-menu-item.dropdown"); const dropdown=document.querySelector(".dz-dropdown-content"); const panels=document.querySelectorAll(".dz-dropdown-panel"); const header=document.querySelector(".dz-header-wrap"); let active=null,timer=null;
const closeAll=()=>{ if(timer)clearTimeout(timer); dropdown.classList.remove("open"); panels.forEach(p=>p.classList.remove("active")); triggers.forEach(t=>t.classList.remove("active")); active=null; };
const openPanel=(btn,panel)=>{ closeAll(); btn.classList.add("active"); panel.classList.add("active"); dropdown.classList.add("open"); active=btn; };
triggers.forEach(btn=>{ btn.addEventListener("click",e=>{ e.preventDefault(); const panel=document.querySelector(`.${btn.dataset.panel}`); if(!panel)return; active===btn?closeAll():openPanel(btn,panel); }); });
if(header){ header.addEventListener("mouseleave",()=>{ if(active)timer=setTimeout(closeAll,250); }); header.addEventListener("mouseenter",()=>{ if(timer)clearTimeout(timer); }); }
document.addEventListener("click",e=>{ if(header&&!header.contains(e.target)&&active)closeAll(); }); });
The impact of e commerce security risks is undeniably significant when it comes to transactions as they cause a great […]
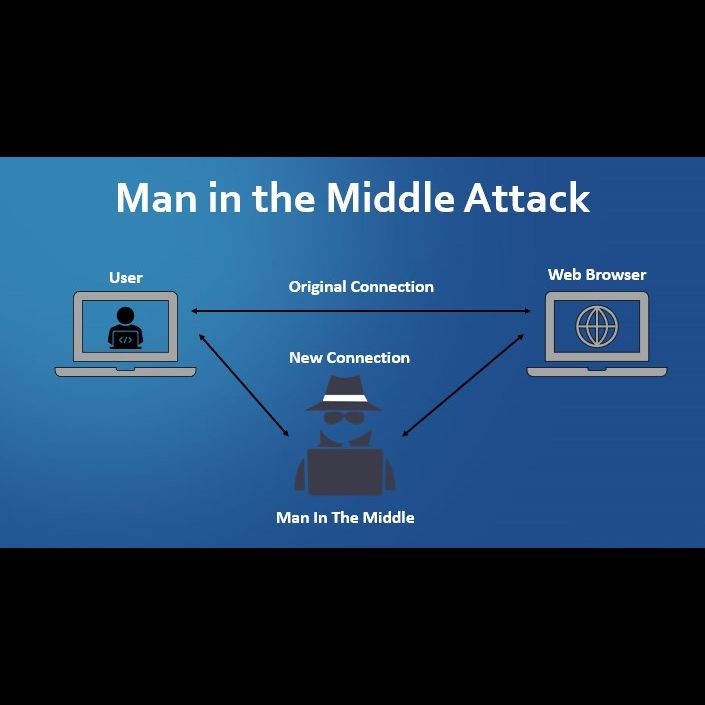
There are various types of security threats that attackers can utilize to exploit insecure applications. Some of these attacks can
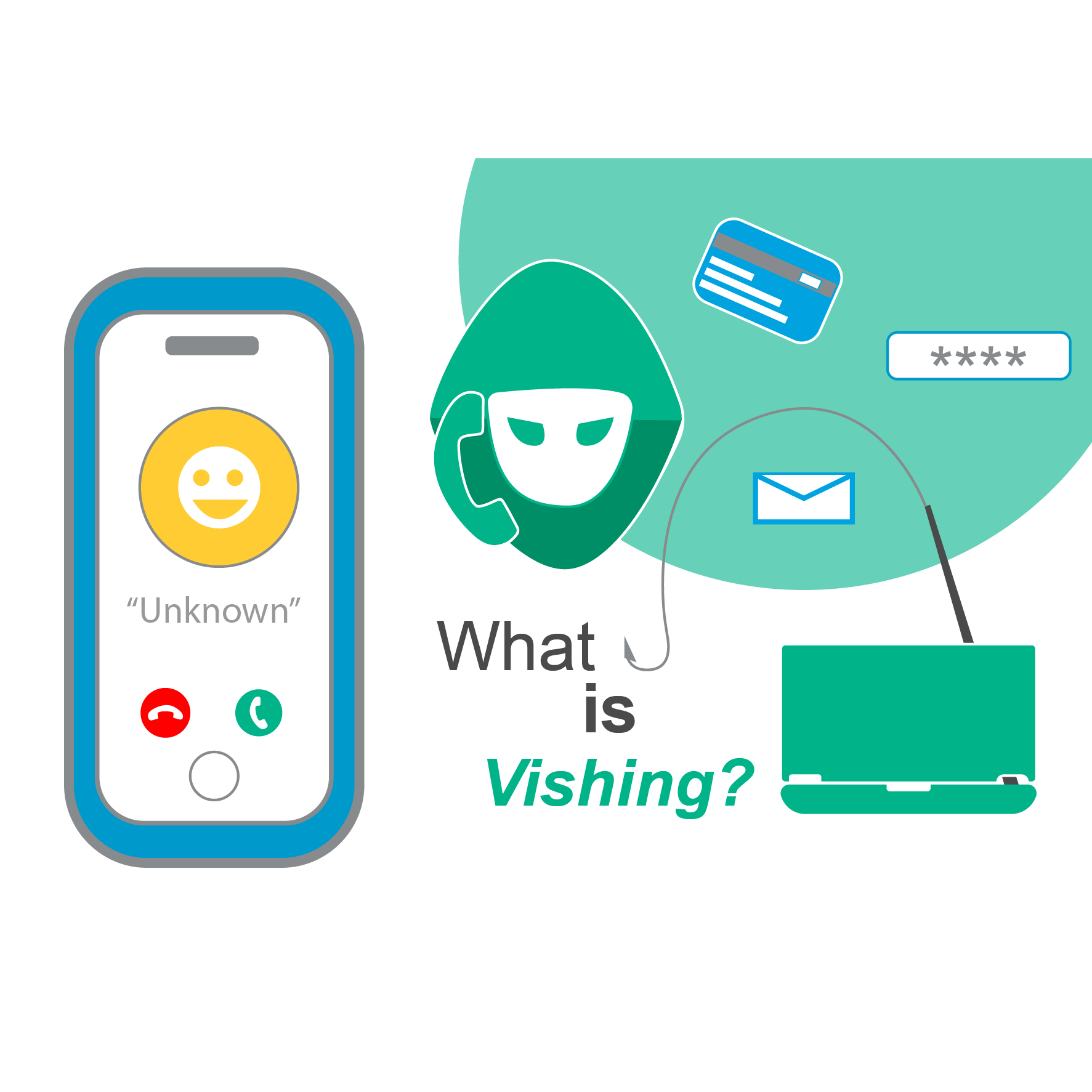
Vishing, which stands for voice phishing, involves using deceptive phone calls to deceive victims into sharing sensitive information such as
Have you ever encountered messages like “Warning! Your computer may be infected!!!” on your computer? The most advisable response is