Browser Hijacking: What Is It and How to Remove
Browser hijackers change internet settings without your permission. They clutter your system at best. Worst-case scenario: ransomware. Learn about browser hijackers, how to remove them, and how antivirus software can keep you safe online.
Browser hijackers, or just “hijackers,” are a type of malware that changes the settings of a user’s Internet browser without their knowledge or permission. Usually, hijackers change the homepage and the search engine that is used by default. Some, however, are known to inject ads, which makes them adware. When users visit certain sites, they are automatically redirected to places that could be dangerous, and the affected system can sometimes be drastically changed. Some hijackers also have keyloggers, which can record the keystrokes of users to get potentially valuable information, like account credentials, that they type into websites.
What is browser hijacker?
A browser hijacker is a type of malware that changes your web browser settings without your permission and sends you to websites you didn’t want to go to. It is often called a browser redirect virus because it sends the browser to other, usually harmful, websites.
One of the goals of a browser hijacker is to help a cybercriminal make money from fake ads. For example, a browser might change the victim’s homepage to the hijacker’s search page. Next, the hijacker changes a victim’s web searches so that the victim sees links that the hijacker wants the victim to see instead of real search results. The hijacker gets paid when the user clicks on the search results. The cybercriminal can also give marketing information about the victim’s browsing habits to third parties.
If a browser hijacker has spyware, the attacker could get the user’s banking information, credit card number, or other sensitive information. Browser hijackers may also install ransomware, a type of malware that encrypts data on the victim’s system and holds it hostage until the victim pays the hijackers a certain amount of money to unlock it.
History
People think that browser hijackers came from a group of companies in Tel Aviv, Israel, called Download Valley. These companies make software that makes money off of free software. Some of the software that these companies make is adware, spyware, and hijackers.
How browser hijacking works?
Most of the time, you download web browser hijackers by accident when you install software that looks safe, like browser toolbars or add-ons. Malware packages are sometimes included with the software itself. Another common method is to trick people into letting more downloads when they agree to a website’s terms and conditions.
No matter how it got on your device, once the unwanted app is there, it can take over your web browser and change things without your permission. Which browser settings are changed and how they are changed vary from hijacker to hijacker, as do the effects on computers that have been infected.
Some browser hijackers, like the Ask toolbar, are not very dangerous because they only make small changes that are more annoying than harmful. But even these can cause your system to get clogged up with files that slow down your computer.
Worse, browser hijackers can be used as a backdoor to let more malware into your system through unsafe websites or even to track what you do online and get to your private information.
How dangerous is browser hijacking?
Most people think of browser hijackers as less dangerous than other types of malware, but this underplays the fact that they can lead people to some of the most dangerous cyber threats.
By changing your browser’s home page or search engine settings, hijackers can send you to any website they want, many of which contain viruses and other cyberthreats. Even people who know a lot about technology can be fooled into trusting malicious sites this way.
Also, the annoying pop-ups caused by browser hijackers are often a gateway for future attacks, especially when the “X” or “close” buttons hide “install” commands that, when clicked, let in a flood of malware.
Some pages and pop-ups that browser hijackers push don’t even need you to click on them to infect your computer. Instead, they use “drive-by downloads” that don’t require any direct user action.
Some very sneaky hijackers also have spyware that lets cybercriminals watch what you do online and get to your personal information. Keyloggers record everything you type, so hackers who know what they’re doing can find your passwords, read your private messages, and get to your banking information.
In the worst cases, hackers could use this pile of personal information to steal someone’s identity. If that wasn’t enough, once they’re in your system, they can install ransomware or botnet malware to take full control of your device.
Once bad people have access to your computer, you don’t know where they will stop. That’s why it’s important to use strong security software to protect your computer and personal information.
Most of the time, you download web browser hijackers by accident when you install software that looks safe, like browser toolbars or add-ons. Malware packages are sometimes included with the software itself. Another common method is to trick people into letting more downloads when they agree to a website’s terms and conditions.
No matter how it got on your device, once the unwanted app is there, it can take over your web browser and change things without your permission. Which browser settings are changed and how they are changed vary from hijacker to hijacker, as do the effects on computers that have been infected.
Some browser hijackers, like the Ask toolbar, are not very dangerous because they only make small changes that are more annoying than harmful. But even these can cause your system to get clogged up with files that slow down your computer.
Worse, browser hijackers can be used as a backdoor to let more malware into your system through unsafe websites or even to track what you do online and get to your private information.
Signs of browser hijacking
There are four main signs that your browser has been taken over: spam, a change in your homepage or other default settings, pop-ups, and not enough space on your hard drive.
Spam: If your browser is hijacked, your default search engine could be changed to one that sends you spam ads or sends you to sites that aren’t safe. These redirects can take you to more dangerous places with more adware, spyware, and other browser hijackers.
Changed settings: A browser hijacker can change your default homepage, browser, and even your default settings. A common method is to take over the toolbar with websites full of ads or fake bookmarks. If all of a sudden your browser has new features or a new homepage, it’s possible that someone took over your browser. If someone changed your default browser, we can help you change it back in Windows.
Pop-ups: Pop-up ads are the most common way that a browser is taken over. Your time on the internet will be filled with ads, and every click you make could bring up a frustrating pop-up. These ads can also show up as links that are put in strange places, like search results or random articles. If your favorite site is now full of ads, it may be because someone took over the site.
Low space: All of this hijacking uses up your device’s storage space and resources. Some signs that your browser has been taken over are not having enough space and taking a long time to load. Getting rid of browser hijackers can give you more space on your hard drive and make your browser run faster. If you still feel slow after getting rid of the hijacking threats, try switching to one of the fastest web browsers.
Low performance: Performance problems and slow page loads can happen if hijacker malware is running a lot of heavy processes in the background.
Examples of browser hijacking
There are many different kinds of hijackers. Some send ads to your browser, others change your default search engine or home page, and still others secretly keep track of what you type. A browser hijacker can not only take over your web space, but it can also install malware. Learn about browser hijackers so you can avoid having your browser taken over.
Some of the most well-known browser hijackers are listed below:
Ask Toolbar
Ask Toolbar is an add-on that comes with many free products. It replaces your default search engine or homepage without asking you. Ask Toolbar used to be called Ask Jeeves before it changed its name. Even though it is often seen as malware, it is still one of the most popular search engines in the world.
Ask Toolbar often sends you to a different site or doesn’t find what you’re looking for at all, and it fills up your browser with sponsored junk. Any product that changes the way your browser works is risky.
Babylon toolbar
In 2011, the Babylon Toolbar started to be used. Without the developer’s permission, download.com, which is owned by CNET, began putting the software with other downloads. The Babylon Toolbar made search.babylon.com the default search engine on the default browser and slowly spread to the other browsers on the computer.
CoolWebSearch
Spyware like CoolWebSearch takes over Google Chrome, Mozilla, Internet Explorer, and other Windows browsers’ search engines. CoolWebSearch sends search requests to its own pay-per-click search engine, which also keeps track of what you look for. CoolWebSearch can even change your browser’s bookmarks and history so that online casinos and adult websites, which are among its sponsors, show up there.
Coupon server
Coupon Server is advertising software that shows pop-up boxes with “coupons,” comparison shopping, and sponsored links that lead to more advertising software. Coupon Server tries to force people to use its search engine-looking homepage.
Coupon Server is a threat to your data security and to your security in general because it can change your browser settings without telling you.
GoSave
GoSave is a plug-in that says it will give you special discounts when you shop online, but it really just puts ads in every part of your browser, even your search results. If you click on a GoSave ad, you might get more adware or other viruses.
GoSave also keeps track of things like your IP address, search terms, cookies, and other information that can be used to find you. You can try one of the best browsers for privacy or delete your browser’s cookies to make it harder for people to track you.
RocketTab
RocketTab is adware that says it will help you search the internet better, but all it does is flood you with ads, change web text into links to products, and show you pop-ups for sketchy software. Some free software for the Internet instals RocketTab without telling you what it is.
Risks of browser hijacking
Your computer is at risk when your browser is taken over by adware, web tracking, or identity theft.
Adware: It is software that sneaks into your browser and fills it with ads. Spamming ads is not only annoying, but it also uses up your computer’s resources and slows it down. Adware is made to be annoying and hard to control. The more ads you click on, the more money the hacker makes.
Tracking: If someone takes over your browser, they might be able to follow you. Web tracking lets hijackers follow you around the web and keep track of everything you do. As you click and surf, browser hijackers keep track of what you do and build a profile of you. Businesses and marketers can get a good idea of who you are over time by putting together your IP address, the pages you visit, where you are, what you search for, and other information.
Identity theft: If a cybercriminal gets enough of your personal information, he or she will soon steal your identity in full. A hijacked browser can sometimes lead to a whole system being taken over, and hijacked computers can put the personal information of an entire family at risk.
How to remove browser hijackers
To get rid of browser hijackers, you have to do more than just put back your preferred settings. As long as the malware is in your system, it will override any changes you make and go back to the way it was set up when it was first installed. Most malware, like browser hijackers, is easy to get rid of, which is a good thing.
1. Uninstall programs, apps, and add-ons that are causing problems
Uninstalling it from your device is the easiest way to get rid of a browser hijacker. This, of course, depends on being able to figure out which program, app, or add-on is causing the trouble. Start with any software that was installed right before the problems started or any other unknown programs that look suspicious.
After you take these programs off your computer, you should restart it. The bad program may have also downloaded more software, which you’ll also need to find and uninstall if you don’t want the hijacking to keep happening.
How to get rid of PC software, apps, and add-ons
1. Once you’ve found the most likely cause, click the Windows start button in the lower left corner of your screen and use the search function to find the Control Panel.
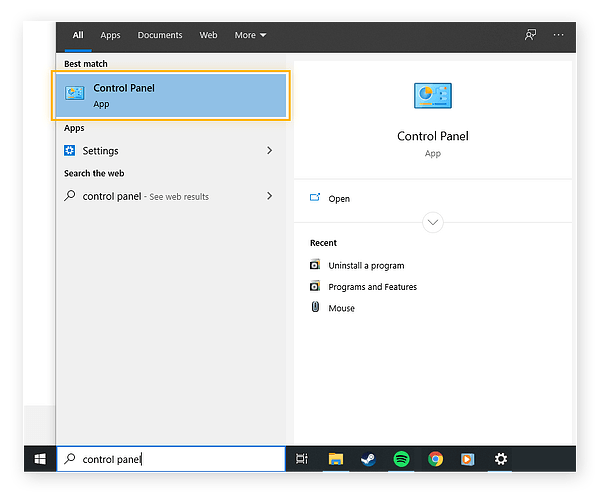
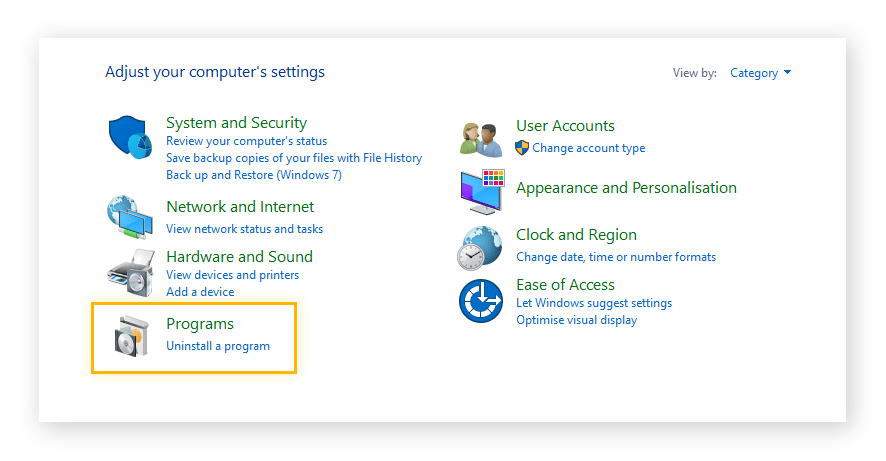
2. Go to the Control Panel and click on Programs. Then click on Uninstall a program.
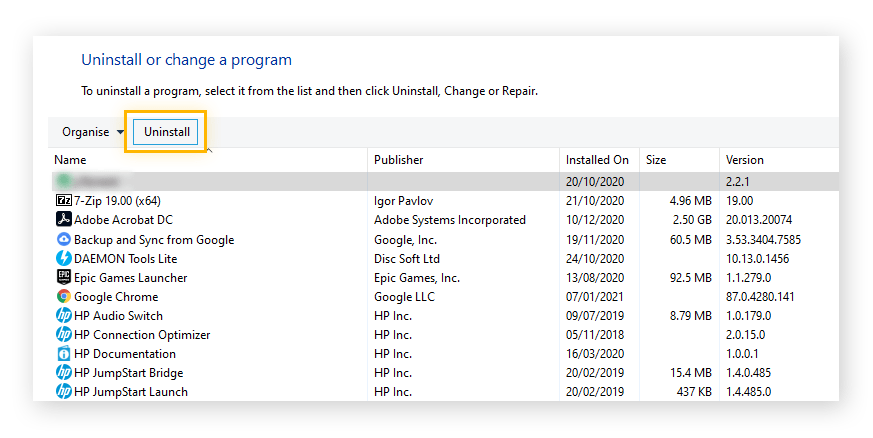
3. Click the Uninstall button next to the software you want to get rid of. You might be asked to confirm that you want to get rid of the app or program.
How to get rid of Mac programs, apps, and add-ons
1. Click the Applications icon in the Finder menu.
2. Click and drag the program’s icon into the Trash, which is at the far right end of the Dock.

3. Empty your Trash to remove the program from your device.
2. Restart your Pc in safe mode with networking
Malware that does more damage may be so deeply embedded that you can’t just get rid of it by removing the programme it got in through. In this case, you’ll need to restart your computer in Safe Mode with Networking so you can install malware removal tools to get rid of the browser hijacker without putting your device at risk.
Safe Mode with Networking for Windows
Follow these 5 steps if you have a PC:
1. Click the Power button on the Windows start menu and hold down the Shift key while you click Restart to restart your computer.
2. After your computer starts up again, it will show you a menu with more options. Choose Fix Problems.
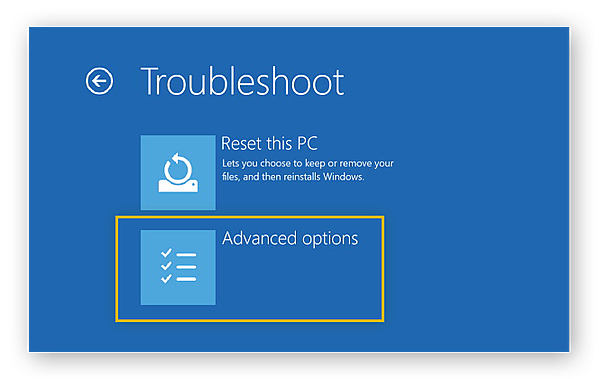
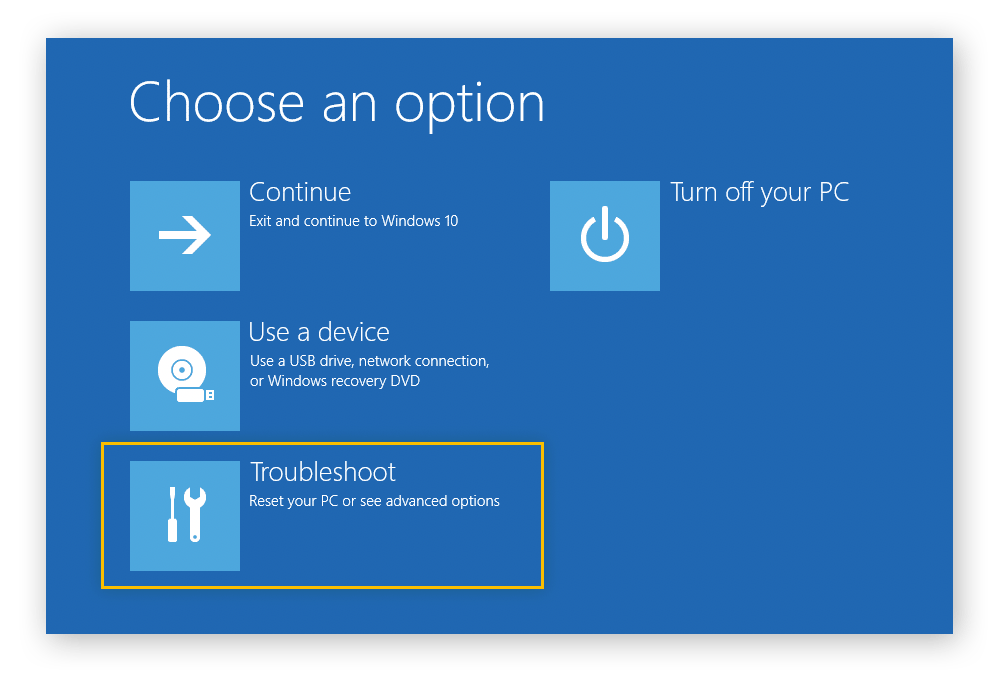 3. Click Advanced Options.
3. Click Advanced Options.
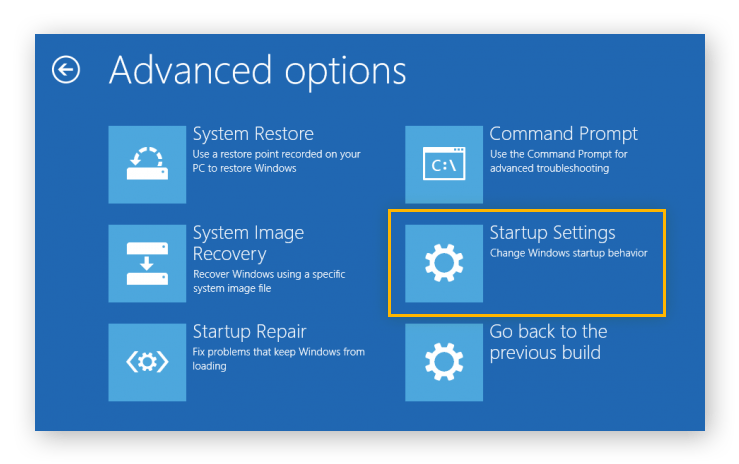
4. Select Startup Settings.
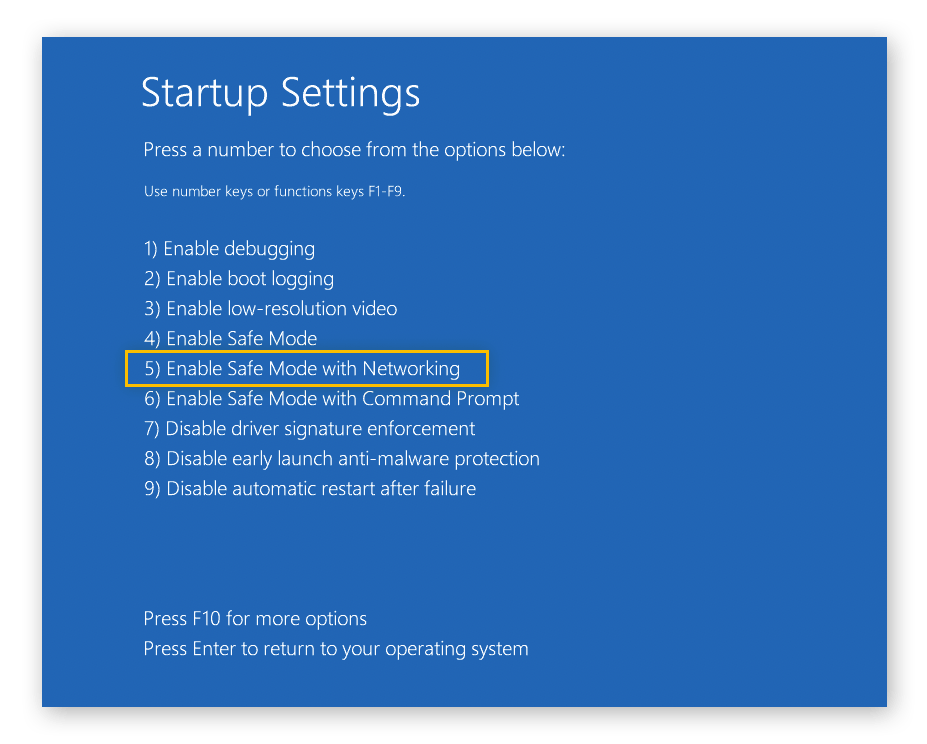
5. To turn on Safe Mode with Networking, press F5. This will let your computer keep starting up in Safe Mode, but it will also let you connect to the internet.
Mac’s Safe Mode
Just put your device to sleep and wait 10 seconds. Then, turn your Mac back on and press and hold the Shift key until you see the sign-in screen. You should now be in Safe Mode and be able to log in normally.
3. Reset web browsers and clear cache
Once all the malware is gone from your computer, you can take control of your browser again. Since you don’t know which settings the hijacker changed, it’s best to use your browser’s Settings menu to put everything back to how it was before. Then you can make changes to your preferences from scratch.
Or, you can download a secure browser and start using it. You can also change the settings for your default browser. Check out our guide to the safest and most private web browsers.
To get rid of any leftover traces of the hijacker, you’ll need to clear your browser’s cache and delete its cookies. That will get rid of bloatware and junk files that might be taking up too much space, slowing down your computer, or putting your privacy at risk.
Your browser’s settings menu has a place where you can manually delete cookies. But the best way to clean your browser and keep it clean is to use a tool that is made just for that.
How to keep hackers away from taking over your browsers
It’s hard to keep someone from taking over your browser. It helps to clean up browser cookies and history directories often. Malware can also install itself on browsers, so it’s important to install and keep up-to-date antivirus software. When someone tries to install software without the user’s permission, the security software should warn the user and ask what to do next. This lowers the chance of getting sick.
Also, try not to run freeware programs. When you install them, they may install software you don’t know about. Also, make sure to check the download settings of any software you want to install. This will make it less likely that your computer will get programs you don’t want.
No matter what users do to protect themselves, the best way to start is by making sure their operating system and browser are always up to date and by being careful when they visit websites.
ad



Comments are closed.