What is Session Hijacking Attack?
Logging into websites or portals is a daily routine for most internet users. When you log in to a website, a session begins. This session, which facilitates communication between two systems, remains active until you end it. While sessions are necessary for online communication, they also create a potential vulnerability known as session hijacking. Read on to understand session hijacking, how it works, and how you can protect yourself.
What is session hijacking?
ad
Session hijacking—also known as cookie hijacking, cookie side-jacking, or TCP session hijacking—occurs when an attacker seizes control of your internet session. This can happen while you’re shopping online, paying bills, or checking your bank balance. Session hijackers typically focus on browsers or web applications, aiming to take over your session and access your personal information and passwords.
By deceiving websites into believing they are you, session hijackers can cause significant security issues. This type of attack enables unauthorized access to protected accounts and the sensitive data they contain by impersonating a legitimate user.
What is a session?
Every time a user accesses a website or application through an HTTP connection, the service first authenticates the user (typically with a username and password) before establishing communication and granting access. However, HTTP connections are inherently ‘stateless,’ meaning each action the user takes is treated as an isolated event. As a result, if we relied solely on HTTP, users would need to re-authenticate for every action or page they view.
ad
Sessions solve this problem. Once a user logs in, a session is created on the server hosting the website or application, serving as a reference for the initial authentication. Users remain authenticated as long as the session remains active on the server, and they can end the session by logging out. Some services automatically end a session after a period of inactivity.
To manage these sessions, many services issue a session ID—a string of numbers and letters stored in temporary session cookies, URLs, or hidden fields on the website. In some cases, these session IDs are encrypted. Often, session IDs are based on predictable information, such as a user’s IP address.
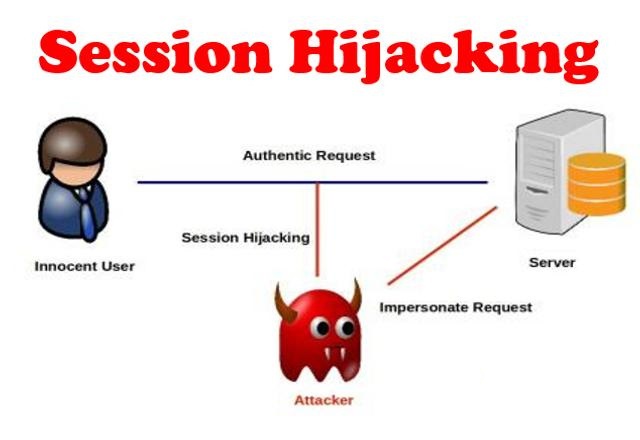
How does session hijacking work?
Step 1: An internet user logs into an account as usual.
This could be their online bank or credit card account, an online store, an application, or a portal. The website or application installs a temporary session cookie in the user’s browser. This cookie contains information that allows the site to keep the user authenticated, logged in, and to track their activity during the session. The session cookie remains in the browser until the user logs out or is automatically logged out after a period of inactivity.
Step 2: A criminal gains access to the user’s valid session.
Cybercriminals use various techniques to hijack sessions. Often, this involves stealing the user’s session cookie, finding the session ID within the cookie, and using that information to take over the session. The session ID, also known as a session key, allows the criminal to take over the session without being detected.
Step 3: The session hijacker benefits from stealing the session.
Once the original user continues their online activities, the hijacker can use the active session to carry out malicious actions. This could include stealing money from the user’s bank account, making unauthorized purchases, collecting personal data for identity theft, or encrypting valuable data and demanding a ransom for its release.
Session hijacking attacks are typically targeted at busy networks with a high volume of active communication sessions. The large number of sessions provides the attacker with many opportunities to exploit and makes detection less likely due to the sheer volume of active sessions on the server.
Types of session hijacking
Cross-site scripting
In a cross-site scripting attack, cybercriminals exploit security vulnerabilities in a web server or application. The attacker injects malicious scripts into web pages, which cause your web browser to reveal your session key to the attacker, allowing them to take over your session.
Session side jacking (also known as session sniffing)
In this type of attack, the criminal needs access to a user’s network traffic. They may gain this access when the user connects to unsecured Wi-Fi or through man-in-the-middle attacks. Session side jacking involves the criminal using ‘packet sniffing’ to monitor the user’s network traffic in search of active sessions. Once the attacker finds a session cookie, they can use it to hijack the session.
Session fixation
In a session fixation attack, the criminal creates a session ID and tricks the user into starting a session with it. This could be done by sending an email with a link to a login form for the website the attacker wants to access. When the user logs in with the fake session ID, the attacker gains unauthorized access.
Man-in-the-browser attack
Similar to a man-in-the-middle attack, this method requires the attacker to first infect the victim’s computer with a Trojan. Once the malware is installed, it waits for the victim to visit a targeted site. The man-in-the-browser malware can then silently alter transaction details or initiate additional transactions without the user’s knowledge. Since these actions originate from the victim’s computer, they are difficult for the web service to detect as fraudulent.
Predictable session token ID
Some web servers use custom algorithms or predefined patterns to generate session IDs. The more predictable the session token, the weaker its security. If attackers capture several IDs and analyze the pattern, they may be able to predict a valid session ID, making it easier to hijack a session. This approach is somewhat similar to a brute force attack.
Impact of session hijacking attacks
Failing to take measures to prevent session hijacking carries several risks, including:
Identity theft
Attackers can gain unauthorized access to sensitive personal information stored in accounts, potentially stealing a victim’s identity beyond the compromised website or application.
Financial theft
Session hijacking allows attackers to perform financial transactions on behalf of the user, such as transferring money from a bank account or making purchases using saved payment information.
Malware infection
If a hacker obtains a user’s session ID, they might also infect the user’s computer with malware, gaining control of the system and potentially stealing data.
Denial-of-Service (DoS) attacks
A hacker who takes over a user’s session could initiate a DoS attack against the associated website or server, causing service disruptions or crashes.
Access to additional systems through SSO
SSO (Single Sign-On) allows users to access multiple systems with one login. Attackers who hijack a session can exploit this access to gain unauthorized entry to other systems, increasing the potential impact of the attack. This risk is particularly significant for organizations that use SSO for employees. Even highly secure systems with robust authentication protocols and less predictable session cookies are only as secure as the weakest link in the entire system.
Session hijacking attack examples
Zoom bombing
During the COVID-19 pandemic, video conferencing apps like Zoom saw a surge in usage and became frequent targets for session hijackers, leading to incidents known as ‘Zoom bombing.’ Reports emerged of hijackers joining private video sessions, where they would shout profanities, use hateful language, and share explicit images. In response, Zoom implemented enhanced privacy measures to reduce these risks.
Slack
In 2019, a researcher discovered a vulnerability in Slack through a bug bounty platform that allowed attackers to force users into fake session redirects to steal their session cookies. This vulnerability could expose any data shared within Slack, which can be substantial for many organizations. Slack promptly addressed the issue and patched the vulnerability within 24 hours of being notified.
GitLab
In 2017, a security researcher found a vulnerability in GitLab where users’ session tokens were exposed directly in the URL. Further investigation revealed that GitLab used persistent session tokens that did not expire, meaning that once an attacker obtained a token, they could use it indefinitely. This combination of exposed tokens and their persistence posed a significant risk, making users vulnerable to various severe attacks through session hijacking, including brute force attacks. GitLab resolved the issue by revising how it managed and stored session tokens.
How to prevent session hijacking
Here are some tips to enhance your security and prevent session hijacking;
Avoid public Wi-Fi
for important tasks such, as banking, shopping online or accessing your email and social media accounts. Cybercriminals could be lurking nearby attempting to intercept session cookies and other sensitive information using packet sniffing techniques.
Use a VPN
Consider utilizing a Virtual Private Network (VPN) when connecting to Wi Fi to add a layer of protection against session hijackers. A VPN conceals your IP address. Ensures privacy by establishing a tunnel through which all your online activities pass. It encrypts the data transmitted and received.
Be wary of phishing and scams
Stay vigilant against phishing attempts and other online scams by refraining from clicking on links in emails unless you can verify the senders legitimacy. Session hijackers may send emails with links that could infect your device with malware or lead you to a fake login page designed to steal your credentials.
Check site security
Keep an eye on the security measures implemented by trusted entities, like banks, email providers, e commerce platforms and social media networks to safeguard against session hijacking. Be cautious of websites, with URLs that begin with HTTPS. The ‘S’ signifies ‘secure’. Avoid using stores or services that lack strong security measures as it could expose you to the risk of a session hijacking attack.
Install antivirus software
Utilize antivirus programs that can efficiently identify viruses and shield you from forms of malware (including those used by attackers for session hijacking). Ensure your devices are regularly updated by enabling updates, on all systems.
FAQ’s
What is session hijacking?
Session hijacking occurs when an attacker gains control of your online session by stealing your session cookie or ID. This allows them to impersonate you and access your personal information and accounts.
What is a session?
A session is the period during which you stay logged into a website or application. It uses a session ID to keep you authenticated without needing to re-enter your credentials for every action.
How does session hijacking work?
- Login: You log in, creating a session with a session cookie.
- Hijacking: An attacker steals your session cookie or ID.
- Exploitation: The attacker uses the stolen session to access your accounts or perform actions as you.
Conclusion
Session hijacking can put your online security at risk. To protect yourself, use a VPN, avoid public Wi-Fi for sensitive tasks, watch out for phishing scams, check for secure website connections, and keep your antivirus updated. These steps will help safeguard your data and online activities.
ad


Comments are closed.